Google this week launched a new Top Level Domain of .zip and it has cybersecurity professionals worried.
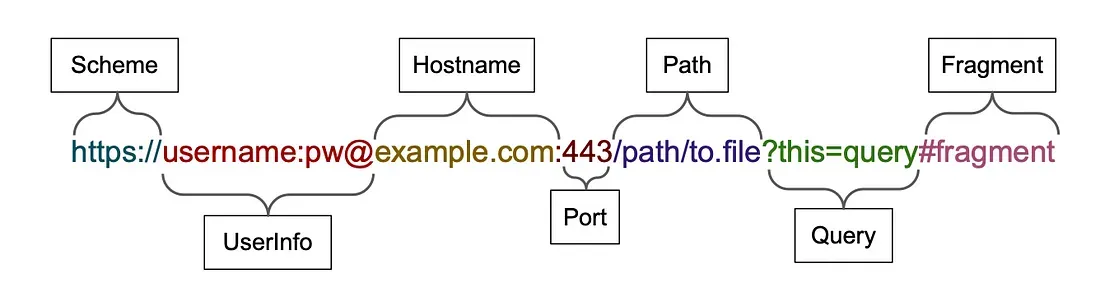
Here’s why. The way that modern browsers treat URLs – considering everything after @ as the host name, rather than the “user information” before it – means that it is easy to create a convincing looking domain that at first glance looks like a well-known .com address, but which really directs a user elsewhere.
If you hit https://ft.com∕@thestack.technology for example, you will get our domain, not the ft.com, despite the initial part of the URL clearly – to most eyes – pointing to the well-known Financial Times domain.
.zip is typically seen as a compressed file type, rather than a TLD. And with the unicode characters U+2044 (⁄) and U+2215 (∕) also allowed in hostnames – both characters which look like a “real” forward slash but which are not treated as forward slashes by the browser – much fun can be had crafting effective phishing emails..
.zip domain security concerns: a simple phishing example
Security researchers at Huntress Labs gave the following example: “If a user wants to download a copy of the open source software Kubernetes, they would visit the Github releases section and download the url from:
But by simply buying the v1271.zip for $15 and spinning up a domain that will “respond to any web request with an attachment evil.exe” [simple example of a malicious programme] they were able to create convincing looking domain by using U+2215 (∕) slashes and adding the @ before the v.1.27.1.zip
Whilst similar malicious domains or links could have been fairly easily spun up before with a .TLD of choice (and there is already no shortage – the use of a TLD that closely resembles a trusted file type has rubbed many up the wrong way and may, most suspect, make for particularly convincing phishing expeditions for Bad Guys™.
Google, say many, should have known better.
As one disgruntled security professional going by the handle @swiftonsecurity put it: “Changing things because it's funny to upset user expectations is not something we want to see in governing institutions or companies.”
Needless to say, if your security setup does not already assume the risk of a user clicking a malicious link that tries to spawn across your network, then perhaps you are not doing security right: Phishing has long been a risk and whilst this may heighten it, it is unlikely to fundamentally reshape anyone's threat model in the long run.
Browser isolation (which runs browser code far away from local devices, preventing infection across risky sites and effectively sandboxing the behaviour of anything opened from them, has arguably never looked more attractive. Agree? Disagree? Views on the responsiblity or otherwise of the .TLD or others? Get in touch.








