Threat researchers at Mandiant say a Chinese threat group has been exploiting a critical vCenter Server vulnerability for two years, undetected.
The CVSS 9.8 vulnerability, allocated CVE-2023-34048 and affecting almost all versions of vCenter Server, was patched by VMware in October 2023.
The company has only just learned – and informed customers today (January 19) – that it has been under active exploitation since 2021.
vCenter Server is an "advanced server management software that provides a centralized platform for controlling your VMware vSphere environments" – i.e. letting admins manage ESX and ESXi servers and VMs.
Several thousand instances appear to be publicly exposed.
VMware said in its advisory that: “There are no workarounds that remove the vulnerability, which allows unauthenticated remote command execution on vulnerable systems” – to reiterate, a patch is available.
vCenter Server vulnerability: Expect exploitation of CVE-2023-34048 to now be 'democratised'
In a Q&A updated today (January 19) VMware said that “you are affected by this vulnerability if you are running any version of vSphere except the latest updates for vSphere 6.5, 6.7, 7.0, or 8.0.” Its initial advisory is here.
As of January 18, 2024 VMware is aware of exploitation in the wild, it added. This appears to have been flagged by incident response specialist Mandiant, which in a January 19 blog said that “Mandiant and VMware Product Security have found UNC3886, a highly advanced China-nexus espionage group, has been exploiting CVE-2023-34048 as far back as late 2021… UNC3886 has a track record of utilizing zero-day vulnerabilities to complete their mission without being detected” the company added.
Mandiant said it uncovered the exploitation whilst exploring how another VMware vulnerability was being exploited by hackers, namely June 2023’s authentication bypass vulnerability, CVE-2023-20867 (allocated a lowly CVSS 3.9 rating by VMware for already requiring root access to exploit: Mandiant said the attackers were using it to live off the land and move laterally without leaving logs, as reported by The Stack here at the time…)
Mandiant said on January 19: “When covering the discovery of CVE-2023-20867 in VMware’s tools, the attack path in Figure 1 [see below] was presented describing the flow of attacker activity within the VMware ecosystem (i.e. vCenter, ESXi Hypervisors, Virtualized Guest Machines)”
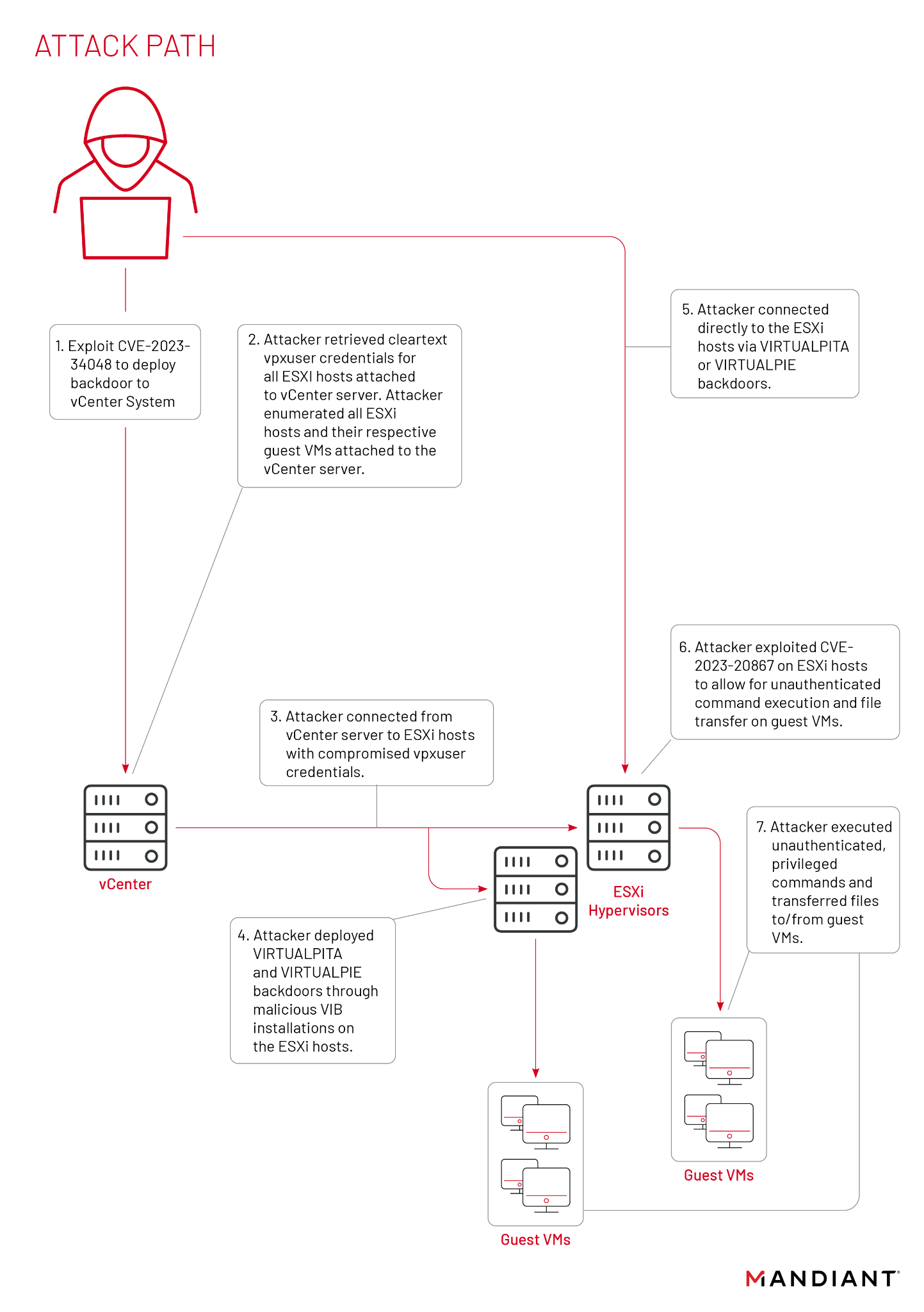
Traces in VMware service crash logs show the "vmdird" service crashing minutes prior to attacker backdoors being deployed, Mandiant said.
“Mandiant has observed these crashes across multiple UNC3886 cases between late 2021 and early 2022, leaving a window of roughly a year and a half that this attacker had access to this vulnerability. Most environments where these crashes were observed had log entries preserved, but the "vmdird" core dumps themselves were removed. VMware’s default configurations keep core dumps for an indefinite amount of time on the system, suggesting the core dumps were purposely removed by the attacker in an attempt to cover their tracks.”
The earlier lateral movement vulnerability meanwhile, CVE-2023-20867, let the cyber espionage threat group “execute commands and transfer files to and from guest VMs from a compromised ESXi host without the need for guest credentials [and without generating] an authentication log event on the guest VM when commands are executed from the ESXi host” Mandiant’s earlier 2023 blog showed. Now the initial access point has been cleared up too: vCenter Server vulnerability CVE-2023-34048. Patch up.









