Security researchers at Kaspersky have identified a new UEFI rootkit in the wild that exhibits some unique behaviours -- including its modification of existing legitimate UEFI firmware rather than adding drivers to it.
Attributing the sophisticated campaign to APT41, a Chinese speaking threat actor, Kaspersky said that the original UEFI firmware was tampered with to embed a malicious code that it has dubbed MoonBounce; this was used to deploy user-mode malware that stages execution of further payloads downloaded from the internet.
UEFI firmware is responsible for initialising hardware then loading and transferring control to the OS. It runs before the OS itself and has higher privileges. Attacks that compromise it are hard to spot and highly persistent.
The attack seemed "aimed at long term espionage against a high-profile entity" the company said. It found just one example of the UEFI implant attack which provided "highly stealthy and persistent storage for malware in the system" but multiple other likely associated malicious malware samples during its investigation.
UEFI rootkits are a potential nightmare for security teams: they are hard to detect and typically able to survive both OS reinstallation and as in this instance, hard disk replacement too. (The first UEFI rootkit found in the wild, dubbed LoJax, was spotted by security researchers at ESET in 2018, again, being used by an APT actor.)
How did MoonBounce UEFI rootkit get there? Nobody knows
Senior Kaspersky researcher Mark Lechtic said: "During investigation of anomalous UEFI level behaviour in our telemetry, we found a tampered CORE_DXE module, originally used... to bootstrap system startup through initialization of externally callable routines (Boot Services, Runtime Services etc.)
"The attackers appended malicious pieces of shellcode and a kernel-mode driver into a newly created section within the CORE_DXE image and caused the invokation of the former through inline hooks set in several Boot Services routines. Consequently, when CORE_DXE runs during system startup it is forced to execute malicious code that propagates to other components in the boot sequence, namely the Windows OS loader and kernel."
Connect with the team and follow The Stack on LinkedIn
Kaspersky said it lacks “sufficient evidence to retrace how the UEFI firmware was infected in the first place.”
A company called Hacking Team that sold offensive security tools and which itself got breached in 2015 had developed a UEFI rootkit the installation procedures for which suggested using a USB drive. But security researchers at Eclypsium have demonstrated remote UEFI based attacks in the past: remote vectors are viable.
Its researchers said that the “infection chain itself does not leave any traces on the hard drive, as its components operate in memory only, thus facilitating a fileless attack with a small footprint” – it is underpinned by an implant found in the UEFI firmware within the SPI flash, a non-volatile storage external to the hard drive.
Kaspersky's full technical write-up including IOCs is here.
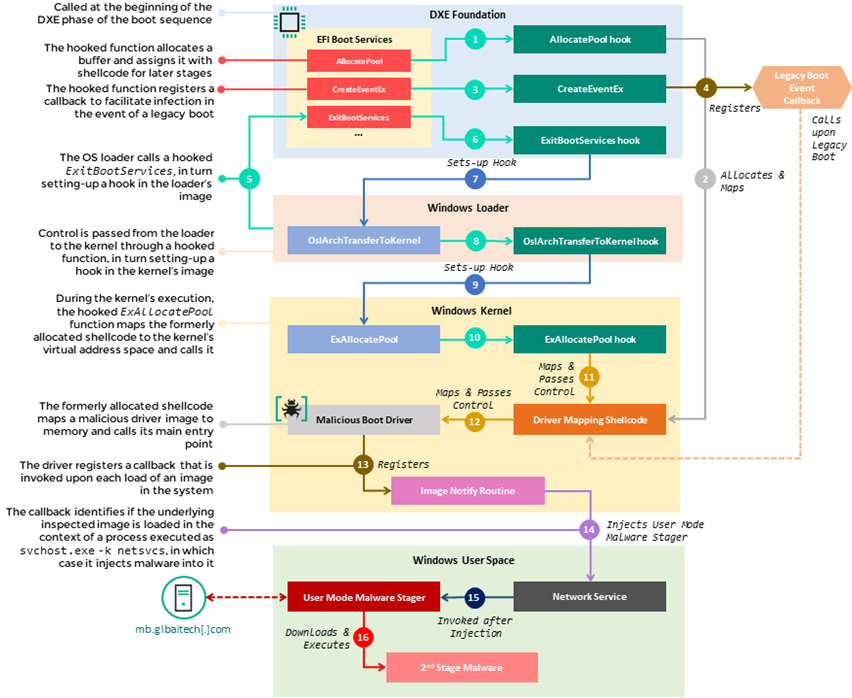
The technique is “more subtle and stealthy” than previous UEFI firmware compromises (i.e. LoJax and MosaicRegressor) which worked through the addition of of DXE drivers to the overall firmware image on the SPI flash. By contrast, MoonBounce is modifying an existing firmware component to alter its behaviour.
The Russian security firm's researchers found a number of other stagers and malware on machines during their investigation, including a previously unkown backdoor that was being used to contact a C2 server using a RESTful API, with a hardcoded IP address and a hypermedia directory path on the underlying server used for information exchange.
Kaspersky's MoonBounce research represents the third UEFI rootkit it has spotted in the wild. Writing after its 2020 identification of MosaicRegressor, hardware security specialist Eclypsium noted that "implant code itself is easy to build and the UEFI file system format is largely unmodified by individual OEMs. This creates a relatively low barrier to entry for attackers and we are therefore likely to see this type of capability show up in other campaigns."








