Back in 2019 Gartner coined the term “SASE”. Standing for “Secure Access Service Edge”, like “Zero Trust” the term has come to mean everything and nothing – and has always, candidly, somewhat confused The Stack.
Gartner describes it as a “global delivery of converged networking and security-as-a-service capabilities such as: SD-WAN, SWG, CASB, FWaaS and ZTNA.” Shoot us now and bury us under a hill of acronyms.
So what the hell is SASE, really? Where do you plug it in? Do you need to add more hardware to a rack? Whose networks is it replacing and why? Gadzooks sir; why does nobody speak plain English anymore?
SASE pioneer Cato Networks seemed like a good place to start asking questions, so we sat down with Cato’s Chief Strategy Officer Yishay Yovel.
Cato got there early...
The Israeli company, founded in 2015 (before Gartner started flinging around verbiage about this approach to networks and security) has all the acronyms and “consolidates all enterprise traffic, WAN, internet, and cloud, into a consistent, optimized, and resilient cloud network.”
The company was founded by Check Point co-founder Shlomo Kramer and is growing fast after a slow start: It hit $100 million in ARR in 2022, and grew 59% in 2023, adding 700 more customers – in late 2023 landing brewer Carlsberg in a major win for a “SASE” deployment that will span 200+ locations and 25,000 remote users. As Yovel says proudly, it has gone from $50k deals to multi-million deals in recent years and is landing increasingly large customers as understanding of the proposition grows.
Security and Network as a managed service
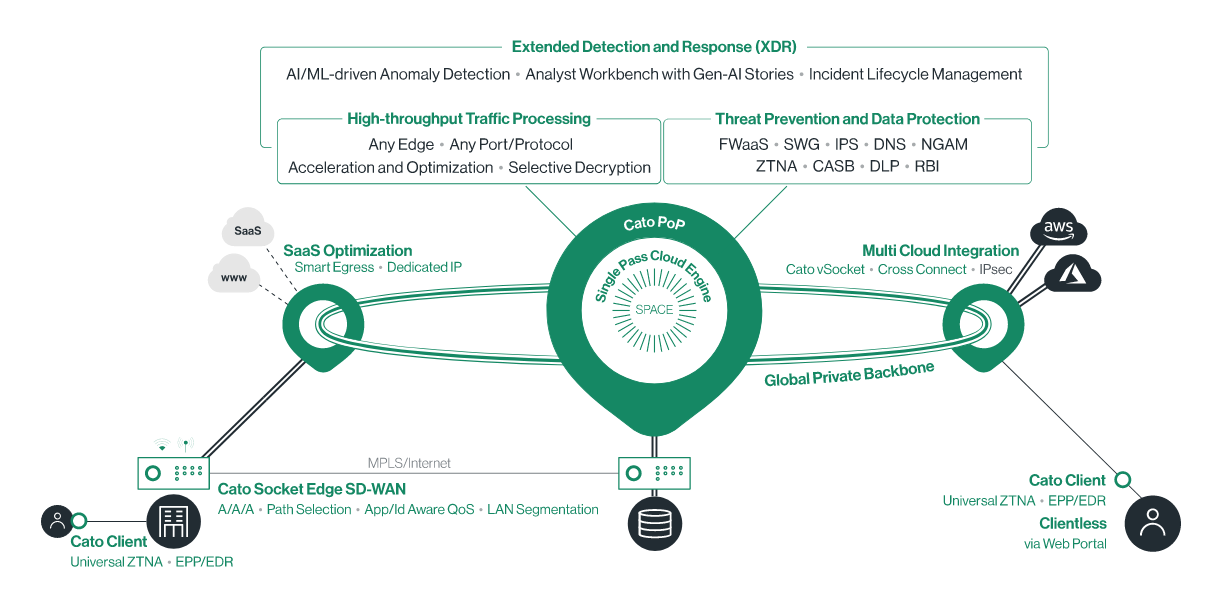
Nice picture, good words, again; what does that mean, exactly?
The shortest version is that you can offload all your network onto Cato’s and bake in a lot of security around that without having to do too much management of it – and without having to patch problematic appliances.
That includes your on-premises network; i.e. a good SASE provider can own both traditional “north-south” (network traffic coming in and out of an internal network) as well as the “east-west” traffic inside a network.
SASE is POP’ing off
Much like CDN and even content providers like Netflix have built up their own “points of presence” or POPs, so has Cato Networks – which has built up around 90 POPs globally (think bare metal compute nodes running in Tier 1 data centres), interconnected by what Yovel describes as a “Five 9s carrier-grade network” of multiple tier-1 network providers, “backed by SLAs on availability, latency, packet loss, and jitter.”
Customers get shipped a small physical appliance called a “socket” that automatically identifies the nearest POP. If a tunnel disconnects the Cato Socket reestablishes the tunnel to the nearest available PoP. (It provides a version for branch offices and another for data centres. Both are monitored and updated by Cato’s network operations centre.)
Or as Yovel puts it: “SASE has two sides: There is the SD-WAN side and then there is the secure cloud network side. The device has one mission, which is to move the traffic from the location – the branch, the data centre – to the nearest point of presence, this is done dynamically. Everything else is done in the cloud: Security is done in the cloud; global routing is done the cloud. So we [have] a cloud-first, lightweight edge strategy..."
(Cato, he notes, just added the ability to handle 10-Gigabit over a single tunnel from a data centre to one of its PoPs.)
To Yovel, having a trusted provider that does, crudely, for your network AND security what the cloud did for your compute and storage (i.e. made it a managed service, stripped out the pressure of managing and patching depreciating infrastructure) is a Good Thing for a Good Many People – particularly those wrangling with myriad applications, firewalls, networks and frankly stretched-thin people trying to stay on top of all of the above.
“CATO created what is essentially a cloud network that is available everywhere, at any scale, very fluid, with security embedded into that cloud network… we are not just your security vendor: we are your secure network, so you run all your traffic through us; not just users to applications, but everything to everything. For us to do that, the network has to be both rock solid and high performance for all use cases”.
That’s a huge leap of faith for many organisations, The Stack ventures; both as a prospective single-point-of-failure and, for the cynically minded, the risk that this turns into the ultimate “Adversary-in-the-Middle” (AiTM) attack; either if things go south somewhere in CATO’s infrastructure or you just don’t trust it as a vendor. Ditto, in heavily regulated industries regulators are still fretting about the cloud; what’s the appetite like for offloading the entirety of a network to a third-party provider like Cato?
“Obviously we have a lot of certifications, SOC 1,2,3, ISO 27017, 27001, we do penetration testing…” he says. “It’s traffic in encrypted tunnels, it's very hard to get to, we don't store anything, everything is in transit…
"There are situations like that – we don't sell to these industries; we just don’t."
"In terms of regulation in general, there is a demarcation point between companies that are so regulated that cannot be in the cloud, or can't adopt cloud in a meaningful way and companies that can,” he adds.
“If the conversation is ‘we can't really work with you because we fundamentally cannot trust cloud providers’ – and there are situations like that – we don't sell to these industries; we just don’t,” Yovel says.
"We can co-exist" with old networks
“In the future, we may create separate clouds. This is something that some of our competitors [have done]; build separate clouds for highly regulated entities. Right now we have a single cloud and the second way we operate, we achieve economies of scale and cost efficiency which is also valuable to our customers. If customers can tolerate the level of… here's what we do from a security posture; here are the certifications we have; here's what we do architecturally…. If you cannot play with that then we cannot be your provider,” he says, refreshingly directly.
What about customers tempted by part of this proposition but also stuck with complex legacy file servers that for whatever reason need an existing VPN/network access setup? “We can co-exist” Yovel says. “We have [customers with] hundreds of locations, thousands of people. It's going to take time and it’s okay to coexist; you have the old network, you have the new network, you're starting to move people, you're starting to move locations, from one network to the other. Routing protocols like BGP, and others allow you to interoperate the two networks pretty seamlessly.
“In the early days some customers just bought us for global connectivity between two locations, they had a Frankfurt data centre and some offices in Asia and said ‘I want just these four or five places connected, because they have latency issues, performance issues, or security concerns…”
SASE meets Zero Trust?
SASE often sits among vendor literature on Zero Trust or is equally abused in marketing. To Yovel “SASE is very solution-oriented: You buy SASE to solve something very specific and see the results immediately. Zero Trust is a multi-year initiative that is three-dimensional. But with SASE you start with a bunch of point solutions. At the end of the deployment, which can vary in length, depending on your complexity and your own ability to move fast enough, those legacy solutions [firewalls, VPNs] are out.”
“Because of what I explained on the network side, global MPLS suddenly goes away. So you don't need global telcos to provide MPLS: That's a point solution. [MPLS or Multiprotocol Label Switching, is a “Level 2.5” networking technology that routes traffic using the shortest path.]
“Because we are 360 degrees – we are east-west and north-south – we replace firewalls; we replace more firewalls than any other technology. That takes out costs and takes out complexity. Then obviously if you have let's say you have a Zscaler in your environment to be able to give Secure Web Access to users that firewalls are not good at, we take that out too.”
Zscaler is, of course, a key rival and Yovel takes a moment to have a light dig: “Zscaler, Cloudflare, Netskope are trying to convince the market that firewalls are not needed. But they are needed because they see traffic that those cloud solutions do not see.” (Part of Cato’s proposition is a cloud-native “firewall-as-a-service” that the company says can replace “all legacy firewall capabilities in a network” and which spans “traffic over all ports and protocols… not limited to HTTP/S traffic only.” )
What does he mean that they don’t see? “Let's say a user got into the office with malware on their laptop. That malware is trying to propagate to the data centre over the Wide Area Network. This is a traffic flow that Zscaler and Netskope don’t see; it goes on different path. We take that traffic up to the Cato cloud [for inspection before it drops into the DC.] By owning the WAN, in short, Cato can strip out security issues right at the branch level before they spread, is the idea. A customer might, he says, typically have “firewalls on prem; cloud-based security; MPLS, and maybe a remote access VPN like Cisco AnyConnect. We can take all of that.”
That also causes friction. As Yovel puts it: “We are competing against incumbents. SASE is a replacement market; every time we come in something comes out, and that something sometimes has a 20+ year history. There’s [work to do on] branding, partners, channel ecosystem…”
Peer referrals have been a big part of Cato’s growth he says and it chimes true (The Stack first encountered Cato some years ago when a COO running IT in a large publisher tangentially connected with our team was hit by ransomware; they subsequently embarked on a major security overhaul, contracted Cato and spoke anecdotally to us highly of the experience, suggesting we have a chat; years later, here we are, educating ourselves in public.)
SASE, in brief, for us, without the jargon? Handing off network and a tonne of pick-and-mix security options like EDR, incident detection, firewalls, secure web gateways etc. all to one managed services provider that can come, in Cato’s example, right down to your branch or DC network level.
What are your thoughts about/experiences of SASE and network management more broadly? Get in touch.





