Ransomware earned criminals over $1 billion in 2023, according to an analysis published Wednesday by a cryptocurrency analytics firm.
That’s ransom payments alone – a record high – and does not include the economic impact of productivity loss and repair costs, Chainalysis said.
(By way of two recent examples: Capita said a 2023 ransomware attack will cost it £20 million in incident response fees and remediation; shipping firm Expeditors reported $60 million in remediation and lost business.)
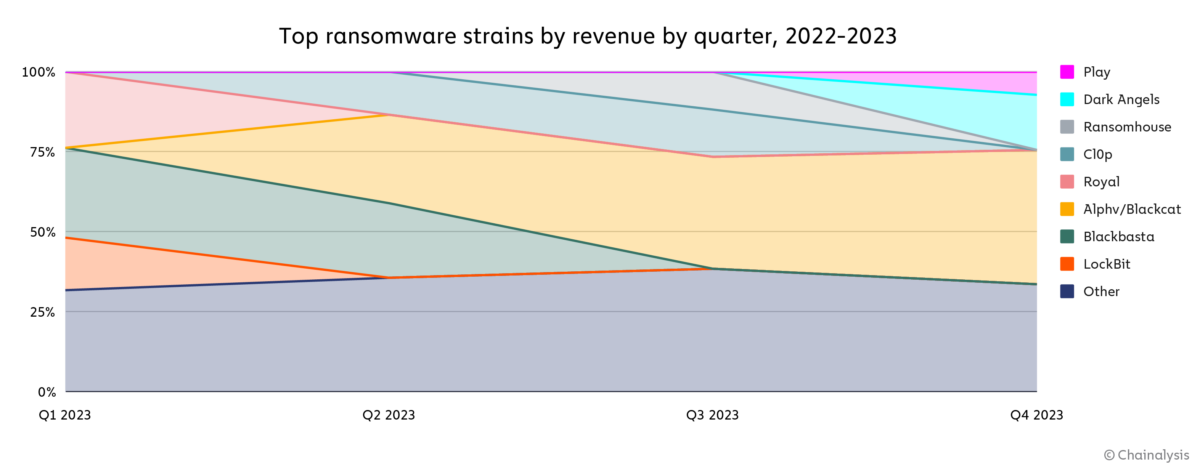
Chainalysis said it tracked numerous new ransomware group entrants and offshoots in 2023, “who... often reuse existing strains’ code.”
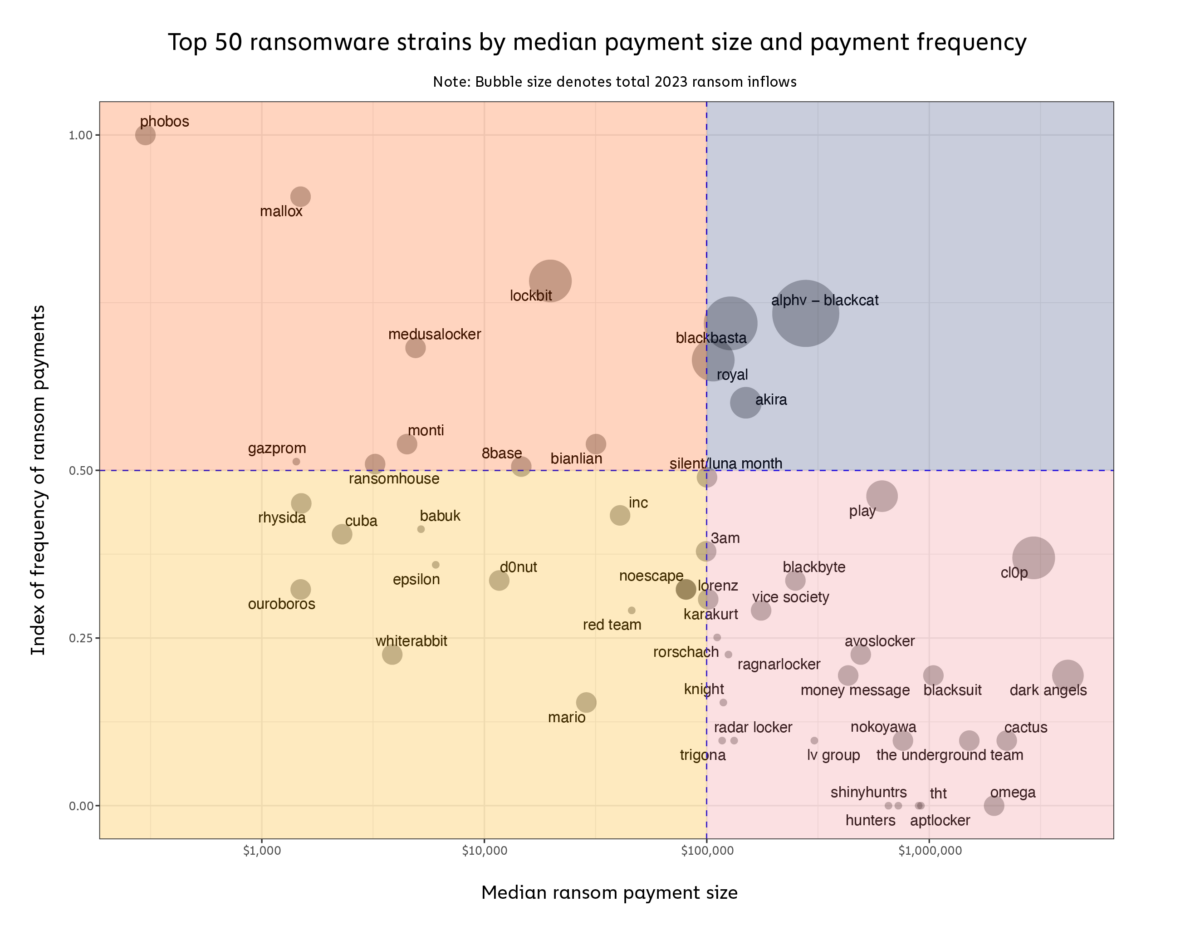
The New York-headquartered crypto-forensics company said in a February 7 report that “this suggests an increasing number of new players, attracted by the potential for high profits and lower barriers to entry.”
From Boeing to the MGM Grand, Estée Lauder to the world’s biggest bank, ICBC, some big targets were hit by criminals in 2023: “Big game hunting has become the dominant strategy over the last few years, with a bigger and bigger share of all ransomware payment volume being made up of payments of $1 million or more,” Chainalysis noted of the trend.
See also: Boeing shares ransomware incident TTPs as Citrix Bleed attacks ramp up
Critically, with resources growing as cash flows in, threat groups have been able to exploit not just social engineering techniques or the kind of low-hanging-fruit poor cyber hygiene often leaves dangling at the end of a branch (weak passwords, exposed RDP, no MFA…) but zero days as well.
A zero day, CVE-2023-34362 in the MOVEIt file transfer was a case in point, allowing the Cl0p ransomware group to harvest $100 million in ransom payments in June and July alone, Chainalysis said. Exploitation of one Citrix vulnerability meanwhile, CVE-2023-3519, triggered “13 separate nationally significant incidents” in 2023 that required the intervention of the UK’s National Cyber Security Centre, it has noted.
(Google's Threat Analysis Group meanwhile this week said that "if governments ever claimed to have a monopoly on the most advanced cyber capabilities, that era is over. The private sector is now responsible for a significant portion of the most sophisticated tools we detect...")
Recovering swiftly from a ransomware attack requires not just reliable, segmented backups but well-rehearsed incident response plans.
Attackers tend to vigorously aim to seek and destroy (or at least encrypt) backups too – something that triggered one 2022 victim to promise a massive overhaul of its cold storage strategy. Easily accessed/recovered backups are often trashed and access to the offline ones is much slower and can require convoluted manual processes (like accessing decryption keys in a safe plus physical data centre access, or restoration from tape…)
As SecureWorks Alex Papadopolous has earlier put it in The Stack: “If you have a fully bricked system you will need to start by reinstalling the operating system first, then applications and services, before being ready to restore any data from backups – what we call a bare metal restore.
(Chainalysis's figures were for 2023. Signs so far suggest this year will be equally bad, with incidents like an attack on one of the most critical securities lending trading platforms hitting financial markets – and industry firms warning that two companies per day were hit with ransomware in December.)
See also: EquiLend confirms ransomware attack has crippled $2.4 trillion NGT trading platform
In one incident response engagement Papadopolous recalled “the impacted organisation had backups which survived the intrusion and ransomware. What didn’t survive was the victim’s Active Directory. Functionally, they couldn’t even start the process of restoring because their backup solution required AD to log in. They needed to authenticate, and nothing worked.”
He added: "To build resilience and be capable of recovering from ransomware, businesses must plan for failure, which means you need good backups but you should also ask the following questions:
- Have you taken the time to consider, test and document how you can recover under all the scenarios [you've] looked at?
- How many systems do you have to potentially recover? What are the complexities? How quickly can you do it?
- Do you have an alternative infrastructure in place, or the means to secure such infrastructure quickly, to keep the business running while you do the full restoration?
- Have you tested and do you have the capability to restore your Active Directory or whatever identity and access management (IAM) technology you use?
"Ransomware remains a very real and potentially very costly threat to businesses. It’s crucial to have solid cyber hygiene. Prevention will always better than cure, so make sure you have best in class detection and prevention in place. But attacks happen, so invest in, understand and test your entire recovery strategy."








