UPDATED August 13, 2021 with fresh Shodan figures
A week after security researcher Orange Tsai demonstrated a new threat vector against Microsoft Exchange servers in a Blackhat USA 2021 talk, over 200,000 servers globally are still unpatched against one of key trio of bugs that can be chained to give a remote, unauthenticated attacker the ability to take over as Exchange administrator -- an attack dubbed ProxyShell. Attackers are now actively attacking vulnerable boxes.
That's according to a Shodan scan, which comes after Tsai detailed the complex but powerful attack, illustrated in this comprehensive blog post published August 6. (Their presentation slides on ProxyShell are here [pdf]. The finding tops a torrid first half for Exchange users, with abuse of the earlier ProxyLogon attacks among the key causes of incident response callouts this year, according to a recent Cisco Talos report.
See also: First malware found escaping Windows containers to attack Kubernetes clusters
Threat actors meanwhile are actively scanning for the Microsoft Exchange ProxyShell vulnerabilities after Tsai's Blackhat talk revealed exploit details. Commodity style attacks are likely to follow in short order and, as security researcher Kevin Beaumont flagged on Friday 13 August, antivirus products are typically not yet picking up the webshells attackers are dropping.
https://twitter.com/GossiTheDog/status/1426142213025714177
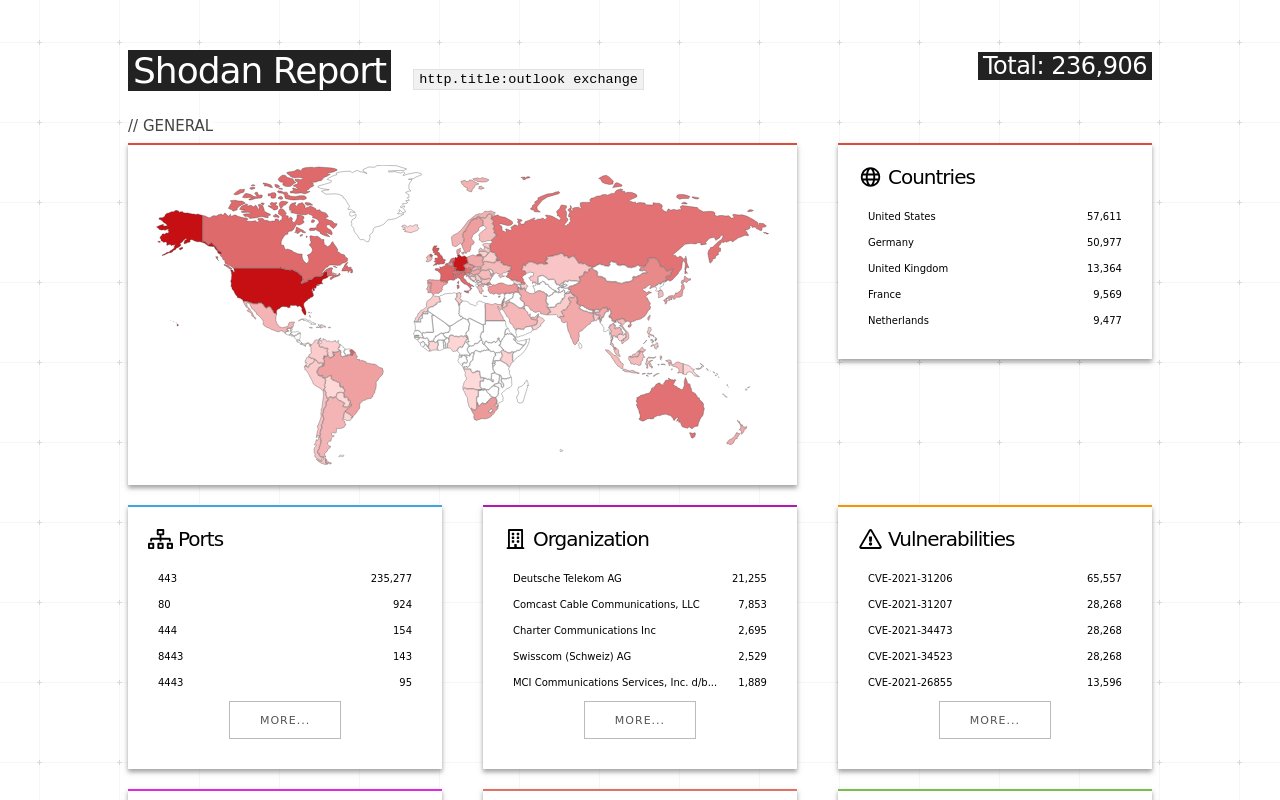
The US, Germany, and the UK are most exposed, Shodan says.
(On the offensive side, security researchers PeterJson and Jang have successfully replicated exploiting the trio of bugs to get RCE in a public post here. For Blue Teams, security researcher Florian Roth meanwhile has provided a YARA rule to detect ProxyShell exploitation in log files that is available here. Patches are available... )
Tsai was among those who reported the so-called ProxyLogon bugs to Microsoft earlier this year, dubbing it "the most severe and impactful vulnerability in the Exchange history ever" in their August write-up.
Multiple threat actors ranging from financially motivated cybercriminals to state-sponsored groups went on to exploit ProxyLogon, Redmond said in March — with the smorgasbord of exposed servers such a compelling target that more advanced attackers acted to remove rival black hats from the systems, and used multiple persistence points to maintain access.
See also: Hackers are using the Slack API, queued print jobs for C2.
The ProxyLogon bugs (CVE-2021-26855, CVE-2021-26857, CVE-2021-26858, and CVE-2021-27065) as reported in January were widely exploited in the wild. But looking at the on-premises mail server's architecture, Tsai said they found "at least" eight vulnerabilities that can be chained into three distinct attacks.
These comprise ProxyLogon; ProxyOracle (which lets an attacker recover any Exchange user's password in plaintext format); and now ProxyShell -- which comprises three chained bugs: CVE-2021-34473; CVE-2021-34523; and CVE-2021-31207 to get RCE. Just under 2,000 UK organisations are vulnerable, a Shodan search suggests.
| Report Time | Name | CVE | Patch Time | CAS[1] | Reported By |
|---|---|---|---|---|---|
| Jan 05, 2021 | ProxyLogon | CVE-2021-26855 | Mar 02, 2021 | Yes | Orange Tsai, Volexity and MSTIC |
| Jan 05, 2021 | ProxyLogon | CVE-2021-27065 | Mar 02, 2021 | - | Orange Tsai, Volexity and MSTIC |
| Jan 17, 2021 | ProxyOracle | CVE-2021-31196 | Jul 13, 2021 | Yes | Orange Tsai |
| Jan 17, 2021 | ProxyOracle | CVE-2021-31195 | May 11, 2021 | - | Orange Tsai |
| Apr 02, 2021 | ProxyShell[2] | CVE-2021-34473 | Apr 13, 2021 | Yes | Orange Tsai working with ZDI |
| Apr 02, 2021 | ProxyShell[2] | CVE-2021-34523 | Apr 13, 2021 | Yes | Orange Tsai working with ZDI |
| Apr 02, 2021 | ProxyShell[2] | CVE-2021-31207 | May 11, 2021 | - | Orange Tsai working with ZDI |
| Jun 02, 2021 | - | - | - | Yes | Orange Tsai |
| Jun 02, 2021 | - | CVE-2021-33768 | Jul 13, 2021 | - | Orange Tsai and Dlive |
Credit, Orange Tsai.
What is ProxyShell?
The three ProxyShell bugs are exploited remotely through Microsoft Exchange's Client Access Service (which Tsai describes as "a well-written HTTP Proxy") running on port 443 in IIS. Microsoft actually patched this CAS frontend in issue in its April 2021 cumulative update, stripping out the "pre-auth" element of the attack, but many users have not updated their servers. The three-step attack is summarised by Tsai simply as:
1: "Deliver [an] encoded WebShell payload by SMTP
2. Launch the native PowerShell and intercept the WinRM protocol
• Rewrite the /PowerShell/ to /Autodiscover/ to trigger [a] Path Confusion bug
• Add query string X-Rps-CAT with corresponding Exchange Admin Access Token
3. Execute commands inside the established PowerShell session
• New-ManagementRoleAssignment to grant ourself Mailbox Import Export Role
• New-MailboxExportRequest to write ASPX file into the local UNC path
4. Enjoy the shell"
(A detailed look at this process and the nature of the vulns is here).
Users, as ever, should endeavour to keep their software updated.
As the NCSC notes, "patching remains the single most important thing you can do to secure your technology". The issue remains, of course, that a failed patch roll-out (not uncommon, as many will attest) is painful for small companies and as the NCSC notes, "for large organisations, it can cause as much impact as a cyber attack, stop thousands of people from working, and require massive resources to fix."
Per NCSC guidance, IT folks who have the time and resource can work to:
- Reduce ways to exploit attacks through architecture and configuration
- Manage your assets well
- Improve operational risk management
- Back up business-critical data
- Have a security monitoring capability
- Create and practise incident response/business continuity plans








