
Phishing was the most common entry point for the cybersecurity incidents that Unit 42 responded to in 2024 – above credential theft.
Nearly a quarter (23%) of attacks that Palo Alto Network’s incident response arm investigated last year started with phishing, it said.
Its 2025 Global Incident Response Report reveals the extent to which the persistently reliable (for attackers) approach of a compelling email and a malicious hyperlink continue to be for those with bad intentions.
Unit 42 said the stats should prompt defenders to continue using “defense-in-depth strategies” to minimise the impact of phishing.
The advice is similar to that of UK’s National Cyber Security Centre, which encourages a “multi-layered approach”. (CISA says focus on four categories to reduce phishing impact: 1) Secure email gateway capabilities 2) Outbound web-browsing protections 3) Harden user endpoints 4) Endpoint protections.)
IT teams should also always “Employ the principle of least privilege.”
Palo Alto Networks meanwhile recommends that security “training should go beyond phishing” with device loss best practice, insider threat indicators, deepfake signs, and help desk red flagsincluded in employee training.
See also: The new face of an old threat: GenAI fuels record-breaking phishing boom
While many, often mistakenly, think of themselves as immune to falling for phishing attempts, use of Generative AI to create more sophisticated campaigns has helped it become highly effective, including for non-native speaker threat groups crafting emails.
(Organisations running phishing simulations to keep awareness high and spot “weak spots” among personnel regularly lament the response from staff, as captured in this Reddit discussion; there will always be someone who clicks…)
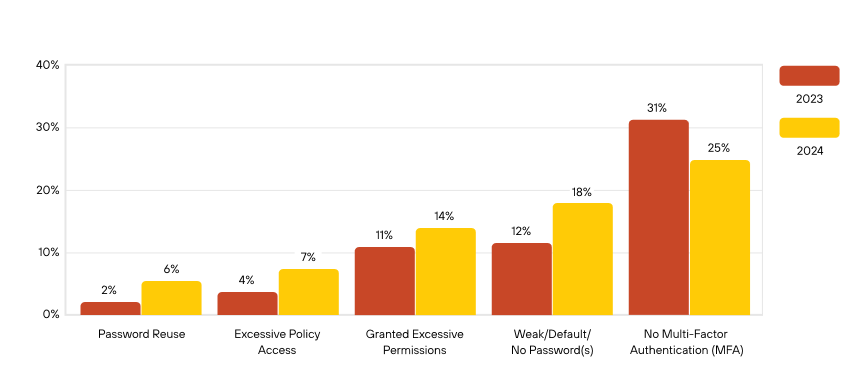
Unit 42 also noted in this week’s report that although MFA use appears to have improved, password hygiene has not: “Other identity and access management issues are trending in the wrong direction. Excessive policy access, excessive permissions and password issues all became more prevalent in 2024” it said.
It highlighted one extortion campaign in 2024 that targeted “exposed environment variables, the use of long-lived credentials and the absence of least-privilege architecture” saying an initial cloud environment breach resulted in the attacker “scanning more than 230 million unique targets for additional exposed API endpoints. As a result, the threat actor was able to target exposed files from at least 110,000 domains, collecting more than 90,000 unique leaked variables. Of these variables, 7,000 were associated with cloud services and 1,500 with social media accounts, often including account names in addition to information needed for authentication.”
Sign up for The Stack
Interviews, Insight, Intelligence for Digital Leaders
No spam. Unsubscribe anytime.
