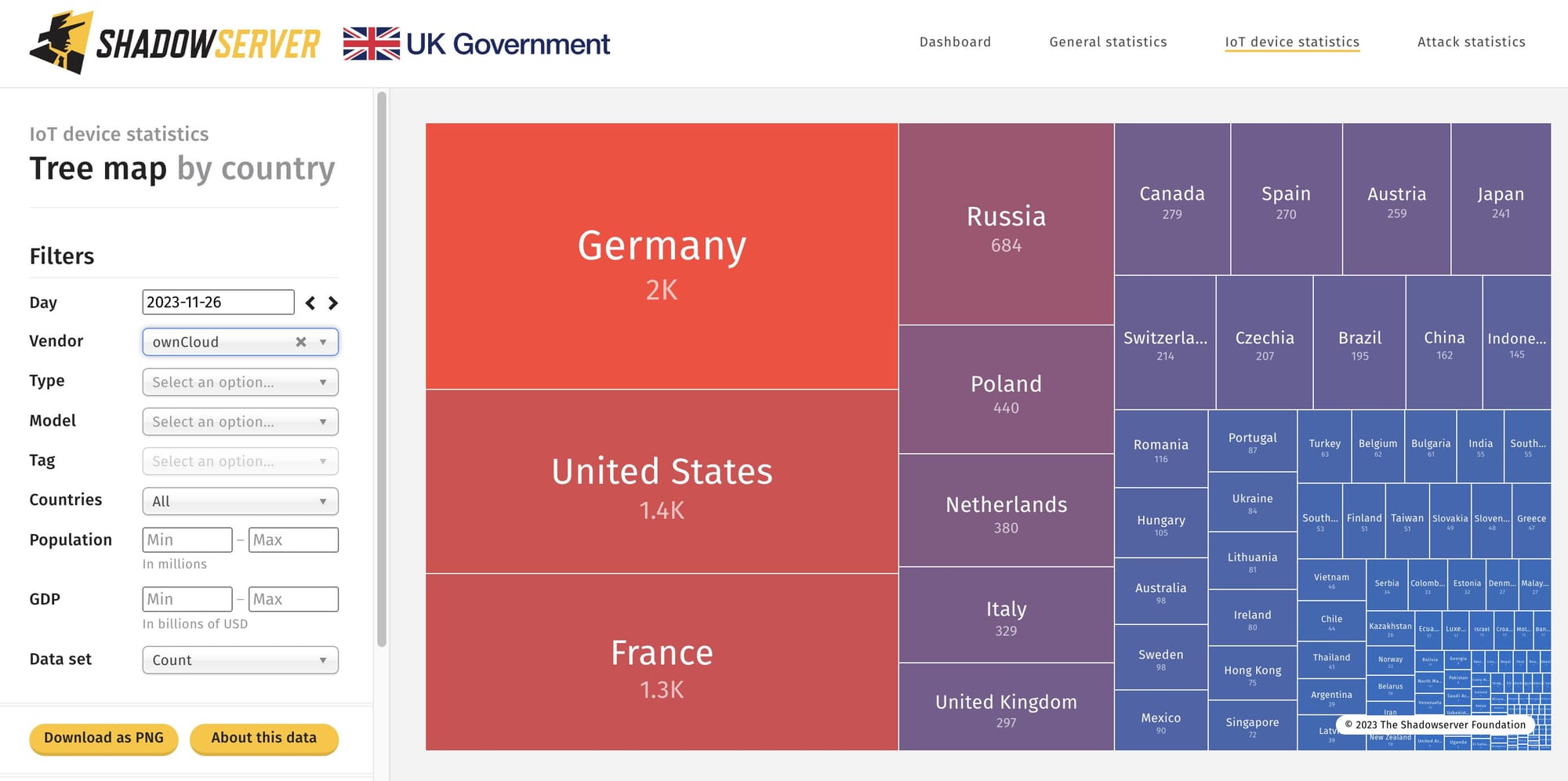
Security firms say mass exploitation has begun of a CVSS 10 bug in open-source file sharing tool ownCloud. The bug has been allocated CVE-2023-49103. Some 11,000 ownCloud instances are internet-exposed.
Proof-of-concept exploits are now widely available.
ownCloud, which claims 200,000 installations, 600 enterprise customers, and 200 million users, issued an advisory and mitigations on November 21. The company names enterprise customers like ETH Zürich, European Investment Bank, European Commission, Wind River, CERN, Banco de Portugal, as well as “as multiple Fortune 500 companies” in its collateral.
(The 11,000 number is from scans by ShadowServer for general publicly available ownCloud instances. It does not assume that they are vulnerable versions; the internet intelligence company is adding further fingerprints.)
ownCloud warned users this week: “The ‘graphapi’ app relies on a third-party library that provides a URL. When this URL is accessed, it reveals the configuration details of the PHP environment (phpinfo).
“This information includes all the environment variables of the webserver. In containerized deployments, these environment variables may include sensitive data such as the ownCloud admin password, mail server credentials, and license key. It’s important to emphasize that simply disabling the graphapi app does not eliminate the vulnerability.
“phpinfo exposes various other potentially sensitive configuration details that could be exploited by an attacker to gather information about the system. Therefore, even if ownCloud is not running in a containerized environment, this vulnerability should still be a cause for concern.”
It also provided mitigations for two other critical vulnerabilities. These include one which makes it possible for an attacker “to access, modify or delete any file without authentication if the username of the victim is known and the victim has no signing-key configured.” (The default).
Organisations should move to mitigate fast and check for compromise.