The NSA has called on businesses to take immediate action to secure Active Directory, a core Microsoft Windows directory it described as "the most widely used authentication and authorisation solution in enterprise information technology (IT) networks globally."
It has joined with other Five Eyes agencies, including the UK's National Cyber Security Centre (NCSC-UK), to issue guidance on how to detect and mitigate attacks on AD. If compromised, AD allows attackers to gain access to all the systems and users it manages.
Critics have long-warned that Microsoft's own native tools to secure AD or identify attack paths are inadequate and the NSA notably points enterprises towards a range of named open-source tools like Bloodhound and Canary tokens to help secure their Active Directory environments, as well as commercial software like Ping Castle or Purple Knight.
Top 10 misconfigurations: NSA checklist for CISOs flags Active Directory Certificate Services
Andy Robbins, Principal Product Architect at SpecterOps and co-creator of BloodHound, told The Stack: "Active Directory has been an adversary's favourite target for decades. Identity Attack Paths in AD let malicious actors move laterally and escalate privilege in ways that are extremely difficult for defenders to detect.
"The security industry has started paying more attention to identity security in the last few years and the size and scope of this problem is becoming more widely understood. More technical guidance, like this report, will be extremely helpful to security and IAM teams. Understanding the techniques used against Active Directory and using approaches like Attack Path Management to remove the most dangerous attack paths will help enterprises and government agencies protect themselves."
When bad actors achieve privileged access to AD, they can bypass controls and access systems to target critical business applications, establish persistent access, bypass MFA during remote login processes, further escalate their privileges and move laterally across enterprise IT networks.
“Like numerous other networks, Active Directory is used in many Department of Defense and Defense Industrial Base networks as a critical component for managing identities and access,” said Dave Luber, NSA Cybersecurity Director.
“This makes it an attractive target for malicious actors to attempt to steal the proverbial ‘keys to the kingdom.’ Taking steps to properly defend AD from these common and advanced techniques will detect and prevent adversary activities and protect sensitive data from determined malicious cyber actors.”
READ MORE: Multiple critical zero day vulnerabilities found in military and filling station fuel tanks
The NSA warned that its vulnerability to compromise is partly due to the permissions granted to each user, which gives them "sufficient permission to enable them to both identify and exploit weaknesses."
"These permissions make Active Directory’s attack surface exceptionally large and difficult to defend against," it advised.
Defending AD is also a challenge due to the "complexity and opaqueness of relationships that exist... between different users and systems."
"It is often these hidden relationships, which are overlooked by organisations, that malicious actors exploit, sometimes in trivial ways, to gain complete control over an organisation’s enterprise IT network," the agencies added.
"Gaining control of Active Directory can enable malicious actors with a range of intentions, whether they be cyber criminals seeking financial gain or nation states conducting cyber espionage, to obtain the access they need to achieve their malicious objectives in the victim’s network."
Once the bad guys have gained access to AD, they are often difficult to evict and can achieve persistence that lasts months or years.
Throwing out the "most determined malicious actors" can "require drastic action" that can prove costly and time-consuming, ranging from resetting all users’ passwords to rebuilding the whole of AD, the Five Eyes partners said.
How to detect and mitigate Microsoft Active Directory compromises
Active Directory consists of thousands of object including users, computers, and groups that interact through complex permissions and configurations.
"Understanding object permissions and the relationships between those objects is critical to securing an Active Directory environment," the NSA advised.
After gaining initial access, malicious actors often enumerate Active Directory to gather information about its structure and configurations. This allows them to exploit vulnerabilities, escalate privileges, and gain control over the domain.
Organisations can enhance their security by thoroughly understanding their own Active Directory setup using tools such as BloodHound, PingCastle, and Purple Knight, which assist in identifying weaknesses and misconfigurations.
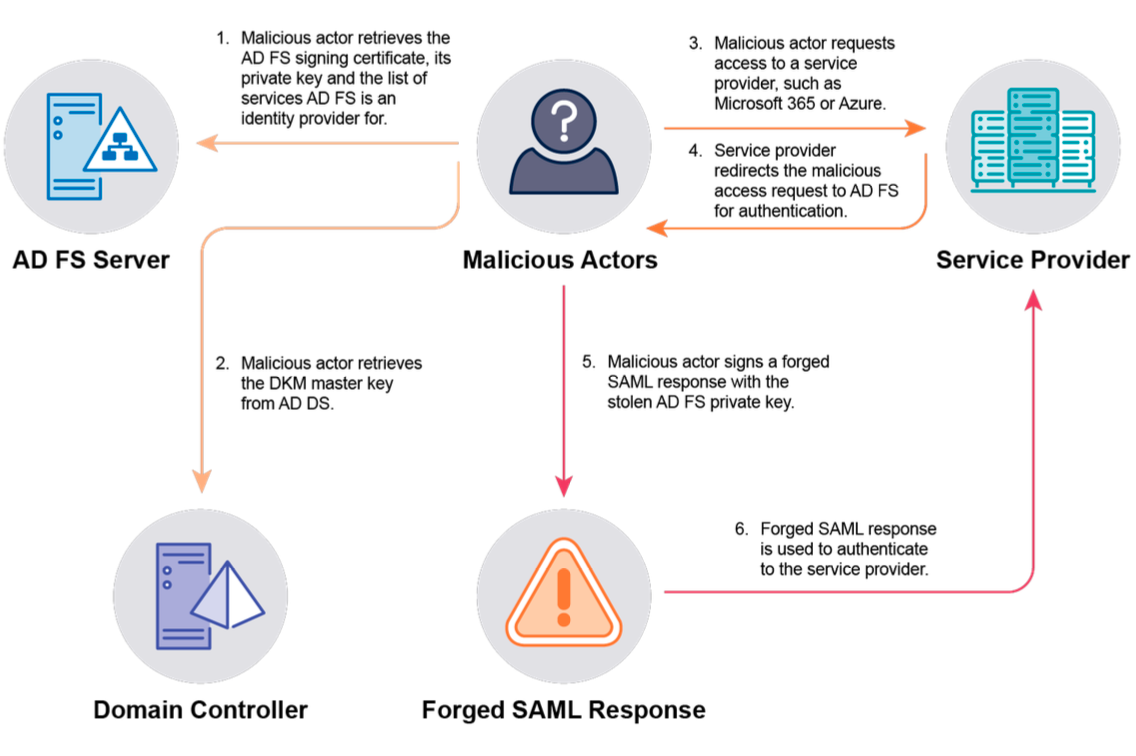
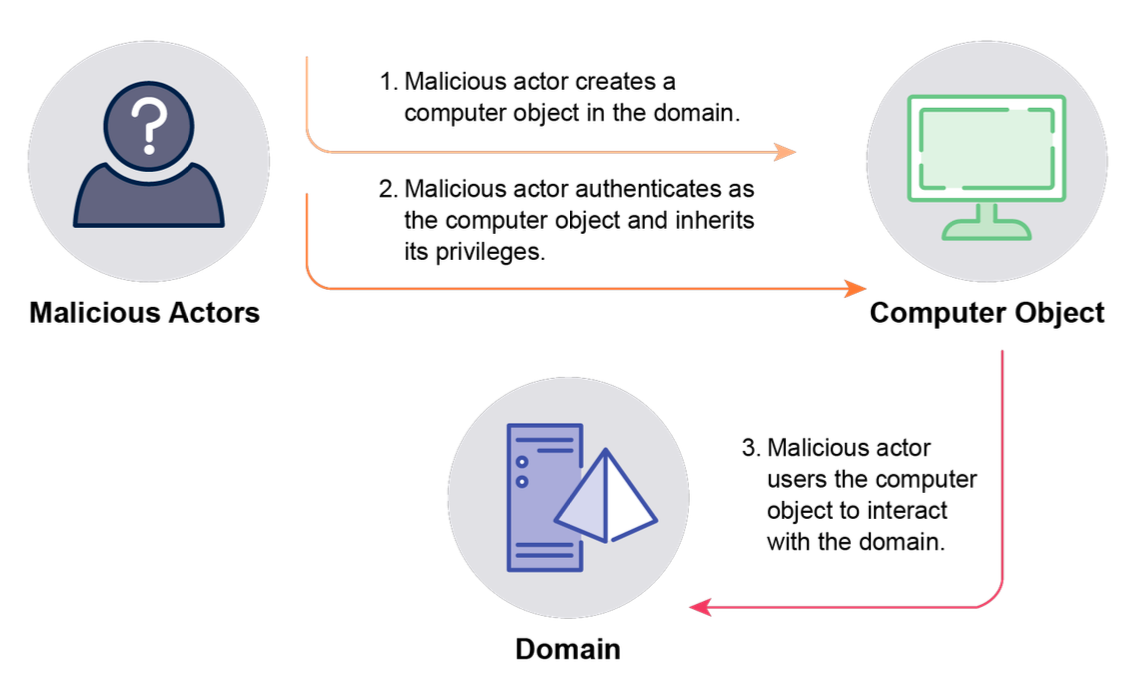
The NSA and its partners provided guidance on how to address 17 common techniques, including Kerberoasting, Authentication Server Response (AS-REP) Roasting, Password spraying, MachineAccountQuota compromise, Unconstrained delegation, Password in Group Policy Preferences (GPP) compromise, Active Directory Certificate Services (AD CS) compromise, Golden Certificate, DCSync, Dumping ntds.dit, Golden Ticket, Silver Ticket, Golden Security Assertion Markup Language (SAML), Microsoft Entra Connect Compromise, One-way domain trust bypass, Security Identifier (SID) History compromise, Skeleton Key.
It also set out details of how to spot AD attacks using "canaries".
"Detecting Active Directory compromises can be difficult, time-consuming and resource intensive, even for organisations with mature security information and event management (SIEM) and security operations centre (SOC) capabilities," the NSA continued.
"This is because many Active Directory compromises exploit legitimate functionality and generate the same events that are generated by normal activity. Distinguishing malicious activity from normal activity often requires correlating different events, sometimes from different sources, and analysing these events for discrepancies."
Canary objects in Active Directory can be configured to deny read access to all users through the “Everyone” security group. When paired with a Directory Service Access audit policy set to track both ‘Success’ and ‘Failure’, any attempt to read these canary object properties generates a failure audit event (event 4662).
By configuring a SIEM system to monitor for this event using the specific Globally Unique Identifier (GUID) of the canary objects, organisations can receive high-value alerts. These alerts indicate attempts to enumerate these canary objects, which may signal a potential compromise of the Active Directory environment.







