There was a time when the National Security Agency (NSA) was seen as the Bad Guy of the cybersecurity world – castigated by Microsoft’s President for the “stockpiling of vulnerabilities” after the NSA’s EternalBlue and EternalRomance exploits were stolen and weaponised in 2017’s WannaCrypt attacks, and seen as a backdoor-maker-in-chief rather than a credible partner for defenders. How the times have changed.
Post-Snowden leaks, post-Shadowbrokers breach, the NSA has worked hard to cultivate a more collegiate approach with cybersecurity providers, and a more public approach to sharing threat intelligence with enterprise partners – e.g. streamlining the release of indicators of compromise (IOCs) associated with various types of malware through “automated Network Defense Notice (NDN) reporting” – as well as open-sourcing tools like software reverse engineering framework Ghidra (a CVSS 9.8 command injection vulnerability found in 2023 not, presumably, part of the plan), sharing swag at conferences, and cultivating friends amongst the hacker community with greater transparency and effective use of memes.

See also: Not an "act of war" rules US judge over Merck ransomware hit
A big driver and public face of that shift has been outgoing Director of Cybersecurity Rob Joyce, a regular face at infosec conferences and approachable meme-wielder, who this week handed the reins to Dave Luber – an NSA veteran who earlier in his career ran the agency’s Remote Operations Center and Tailored Access Operations (TAO) hacking group; later being appointed Executive Director, United States Cyber Command.
(“Welcome to cyber” someone posted on X to the news of Luber's appointment; we hope entirely unironically. Welcome indeed…)
"Honored to take this role..."
“Thanks to Rob Joyce for his exceptional leadership of @NSACyber over the last few years! I’m honored to take on this role as the new Director of Cybersecurity at NSA. Cyber is a team sport – I’m looking forward to working with partners across the community,” Luber said on X, where he was welcomed but also swiftly told he has “big boots to fill”.
Luber's appointment comes amid broader change at the NSA with General Timothy D. Haugh, assuming command from General Paul M. Nakasone – who "greatly expanded the cybersecurity mission" on February 2, 2024.
It also comes amid a rapidly evolving threat landscape...
Get yo'self subscribed to The Stack: It's free and easy.
As well as coming under immediate pressure from the social media chatterati to be immediately amusing and personable and bring his meme A-game, Luber faces other challenges too, some of them less funny.
They include growing threats to operational technology (OT) embedded in critical infrastructure, not least from China, “an adversary that is unique in the scope, scale, and sophistication of the threat it poses” as the NSA’s 2023 “year in review” put it.
The agency warned in February that China’s Volt Typhoon APT is “seeking to pre-position themselves on IT networks for disruptive or destructive cyberattacks against critical infrastructure in the event of a major crisis or conflict…” and has been “maintaining access and footholds within some victim IT environments for at least five years" and other indicators suggest high levels of activity from China, as well as a persistent and sophisticated threat from Russia.
Other challenges?
Getting partners and command centres off "obsolete cryptography", and executing "cybersecurity risk evaluations of DoD’s most critical systems" amid heightened geopolitical risk. That priority, highlighted in the NSA's year in review, comes five years after the agency ended production of punched paper tape cryptographic keys after over 50 years’ use; making its final shift to an electronic cryptographic key production and distribution architecture.
The last such key rolled off its systems on October 2, 2019, as a spokesperson told The Stack’s founder that year. The technology, which uses paper-mylar-paper tape rolls punched with holes to store cryptographic keys – a hole represents a binary 1, and the absence of a hole a binary 0 – remains in use in the UK, particularly by the Ministry of Defence and we suspect there's still a few such keys knocking about some military units, even if they are not being actively produced anymore...
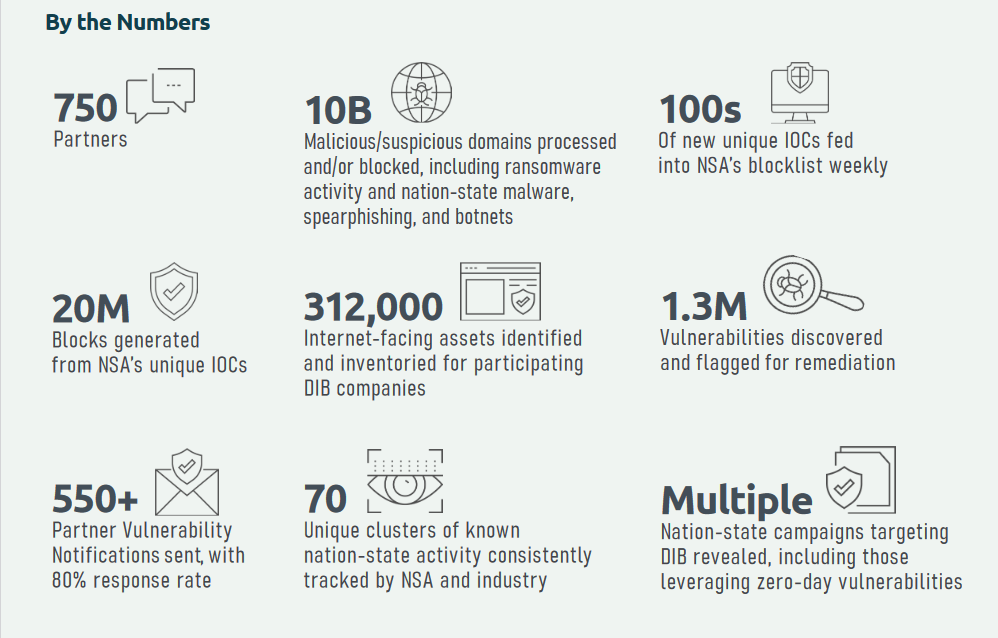
That same year in review highlighted a three-fold increase in partnerships under its Cybersecurity Collaboration Center (which offers free cybersecurity services to “any company that has contracts with DoD or access to non-public DoD information”).
Joyce proudly boasted of a “400% increase in enrollments in our services helps to ensure our critical partners in defense – including small and medium-size businesses – don’t have to secure their systems alone.”
See also: UK’s spy agencies grapple with IT modernisation – as GCHQ ramps up hacking capabilities
More recently, the NSA also recently set up an Artificial Intelligence Security Center as a “new focal point to apply the unique insights from NSA signals intelligence and technological expertise”.
It has also “made progress in the marathon to transition to quantum-resistant cryptography to protect our networks, the technology we rely on, and our weapons platforms” – and completed “cryptographic roadmaps for each U.S. combatant command coalition partner to help our partners identify where they need to invest" – an ongoing task at multiple levels.
The NSA’s traditional offensive work is no-doubt getting harder too.
Security research is significantly more mainstream than it used to be – widespread reverse engineering and analysis efforts globally make it harder to hide zero days for long – nation state and cybercrime adversaries are well-resourced and increasingly savvy, and even sophisticated exploits do not always go unnoticed, ultimately; although they only need to do so for so long…
All in all, big boots to fill at a big agency with a lot on its plate.
There's probably a meme for that.