
The UK government is eying tighter security requirements for managed service providers (MSPs), but its response this week to an earlier consultation by the Department for Digital, Culture, Media and Sport (DCMS) on “enhancing the security of digital supply chains and third party IT services” suggests that plans are inchoate, with policy makers lacking even a working differentiation between cloud service provides and MSPs.
“IT service providers could be required to follow new cyber security rules” [our italics] and “the government will now develop more detailed policy proposals” ministers said, publishing HMG’s response to a consultation that they admitted November 15 “was too narrowly focussed on risks associated with this industry”.
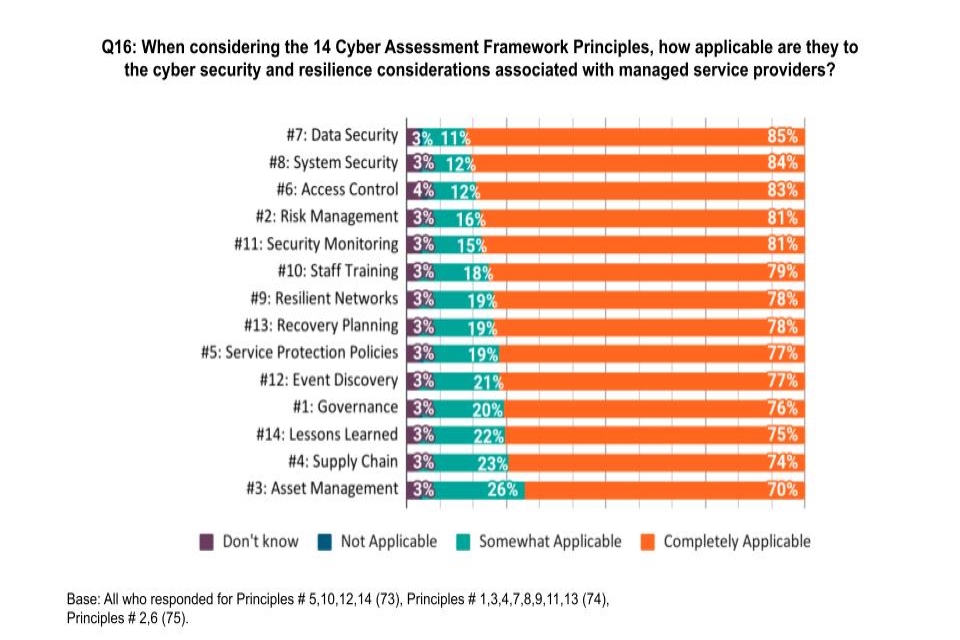
Requirements for formal certification by MSPs under the NCSC’s Cyber Assessment Framework (a set of 14 cyber security & resilience principles) appears one of the most likely outcomes, its response suggests however.
The DCMS consultation -- a “call for views on supply chain cyber security” first published on May 17, 2021 – had identified MSPs as a key supply chain cybersecurity risk, noting that [only] “a small portion of Managed Service Providers that provide cloud computing services on top of their Managed Service offering is captured under the Network & Information Systems Regulations. As currently scoped, cloud computing services are subject to much less stringent regulatory oversight than other entities under the Regulations.”
It added: “For example, the ex-post supervisory regime ensures that regulatory scrutiny applies to cloud service providers only in the aftermath of an incident. However most MSPs are not within scope of the Digital Service Provider definition and are therefore not subject to the Network & Information Systems Regulations.”
Unsurprisingly, among the 214 responses the government received was no shortage from MSPs and cloud service providers fighting their corner and HMG noted somewhat apologetically this week that “the input from the consultation unambiguously emphasises the positive and critical role that cloud and managed service providers play in building the UK economy… public services… cyber security and resilience in the UK.”
MSP cybersecurity consultation comes amid wave of attacks
The consultation was well-intentioned: MSPs have proven an enticing target for hackers and the downstream impact of hitting an organisation delivering IT services for a wide range of organisations is clear and well demonstrated. July’s attack on Kaseya is a powerful case in point. That saw an affiliate of the REvil ransomware syndicate use vulnerabilities in software from Florida-based Kaseya to hack some 50+ MSPs that used its products; piggybacking on that access in turn to hit over 1,500 organisations with ransomware.
(The trend isn’t new: see 2016/2017’s “Cloud Hopper” attacks by China’s ATP10 for example, while earlier in 2020 the US Secret Service was also warning of an ongoing increase in attacks on MSPs.)
Yet as respondents to the MSP cybersecurity consultation noted, its language was imprecise.
This week ministers acknowledged, somewhat worryingly, that it didn’t have a working definition of the difference between a cloud service provider and an MSP, saying “as we seek a common understanding and appropriate language to best represent the diversity of providers of digital technology services, the government will act on consultation feedback and continue work to further refine and distinguish the definitions of cloud and managed service providers” while also looking more closely at the “systemic importance of some cloud, software and MSPs and, therefore, the need for further policy prioritisation.”
It “recognises the close interaction and the frequent business model overlaps between digital technology providers such as managed service providers, cloud service providers and some software vendors. All of these types of suppliers are endemic third-party providers of digital technology services and are an indispensable part of UK and global supply chains” it added in the November 15 response to the DCMS consultation.
“The government therefore agrees that any future policy should consider this broader range of digital technology providers, moving away from an exclusive focus on managed services” it concluded.
So far, so much hand-wringing.
What’s actually pending?
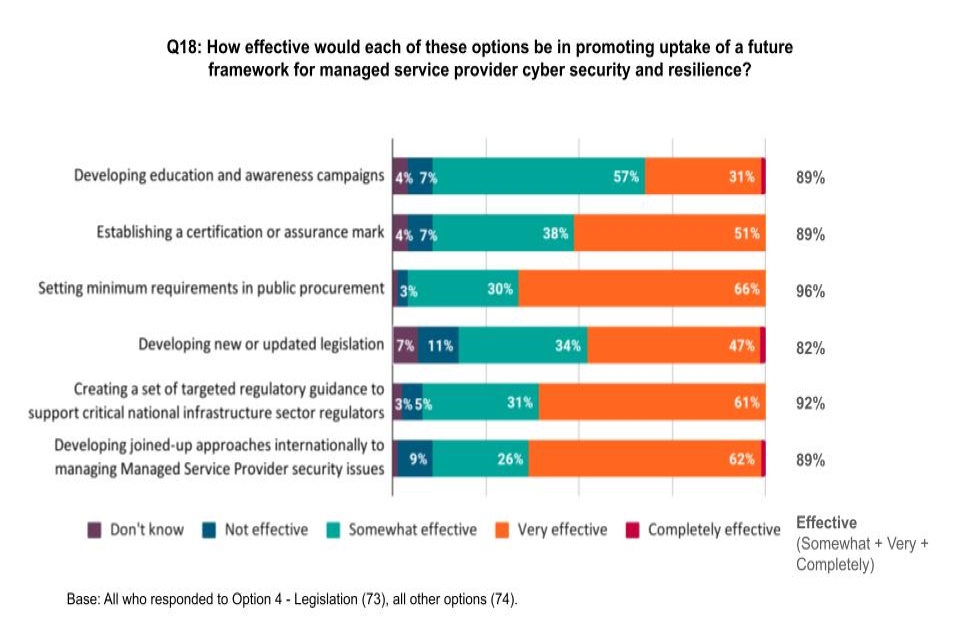
Tighter minimum requirements in public procurement and “legislative work to ensure that managed service providers undertake reasonable and proportionate cyber security measures” both look likely.
Many respondents to the consultation cited lack of expertise and lack of investment that could give their organisations greater insight into supply chain risk and HMG noted pointedly that “is the responsibility of senior management and boards to prioritise and drive investment in this area” saying that as well as regulation, it will “seek to harness influential market agents to drive supply chain cyber security risk management up the agenda, ensuring they have access to appropriate guidance and information about the costs and impact of cyber incidents to strengthen the internal case for investment.”
Supplier engagement and working in close partnership with suppliers for continuous improvement was highlighted by many respondents, with the second most common theme being the need for ongoing monitoring, including “regular reviews and meetings with suppliers” – with some advocating the need to incorporate these strategies for continuous improvement into contractual agreements: certifications like Cyber Essentials, ISO standards (e.g. 270001), PCI DSS, SOC 2 compliance requirements were also flagged.
Is genuinely tighter industry-wide regulation imminent?
It appears unlikely, but some limited government action may be on the cards.
Respondents overwhelming pointed to regulation as the most effective tool for managing supply chain security risk, and HMG noted in its response that “the barriers organisations face in managing supply chain cyber security risk may not be overcome by awareness raising and the provision of new guidance alone.
“Alongside addressing the structural barriers around access to skills and supporting market solutions, DCMS is also exploring more interventionist approaches, but will target these in sectors that are most critical to the resilience of the UK, or which have the potential to pose most supply chain risk across the economy.”
For MSPs, that may be mandatory rules around how they conform with the NCSC’s CAF.
“The government recognises very strong industry support for the application of the Cyber Assessment Framework principles in the context of managed service providers’ cyber resilience” it noted, saying it will commit to “further consideration of the Cyber Assessment Framework principles when establishing any future security baseline or assurance frameworks for the managed services industry or, where appropriate, other providers of digital technology services,” adding that this could include “formal certification with auditing, obligation to report incidents as well as customer transparency and cooperation specification (to help mitigate against the lack of transparency highlighted by respondents as a key barrier to managing suppliers).”
