Cyberattacks that use online advertising to get unsuspecting users to download malware including ransomware are on the rise.
Threat actors are using online ad networks and SEO to push out rogue installers, distributing malware, security firms say.
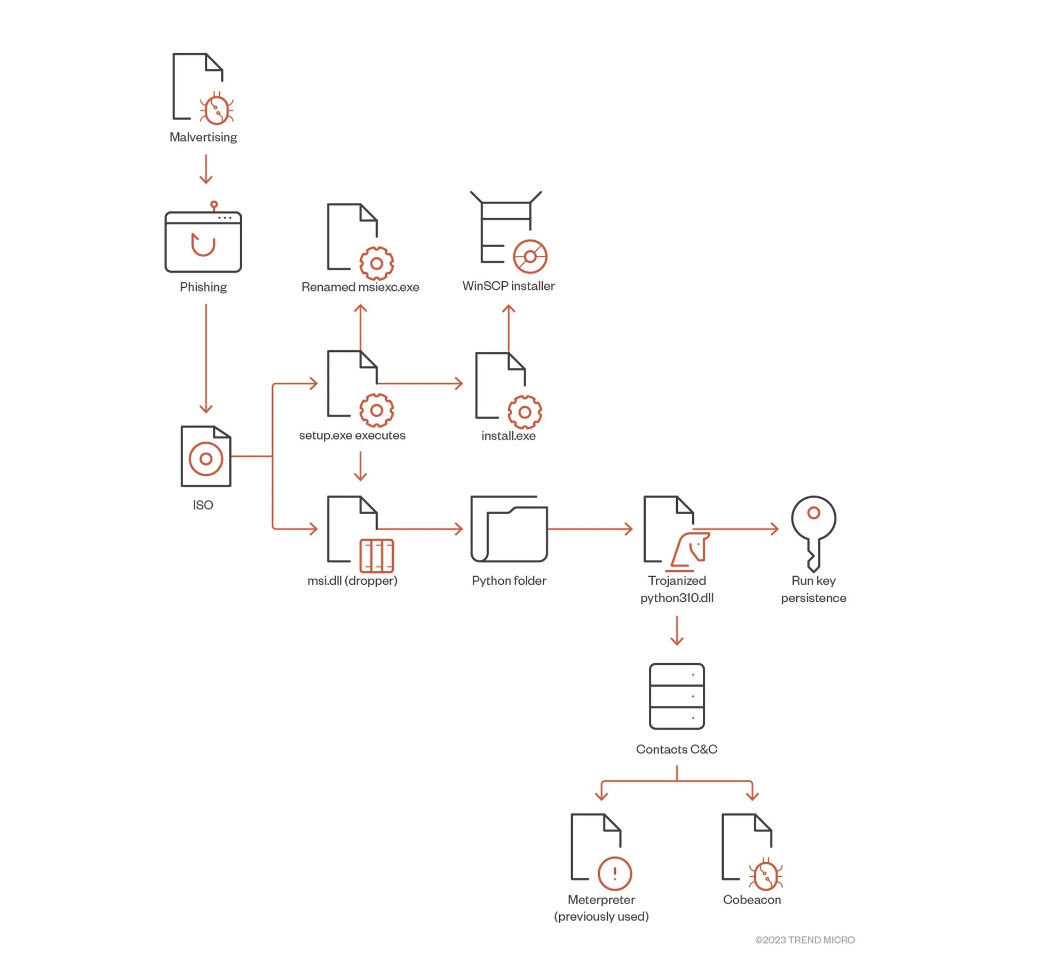
In a recently reported incident, BlackCat threat actors used Google Ads to direct unwitting searchers to a cloned website of the WinSCP Windows application – where a convincingly legitimate-looking download page installs malware instead.
The BlackCat group has a RasS (ransomware as service) model and operates a double extortion scheme, deploying custom data exfiltration tools like ExMatter to siphon sensitive data prior to encryption.
The latest use, examined by Trend Micro, found that targeted organisations were impacted in multiple ways by the malware downloads.
These included BlackCat threat actors stealing top-level administrator privileges and using these privileges to conduct unauthorized activities, along with attempting to establish persistence and backdoor access to the customer environment using remote management tools like AnyDesk.
In this instance, the malware-laden installer allowed for a a backdoor that contains a Cobalt Strike Beacon , which connects to a remote server for follow-on operations.
The Cobalt Strike was the further used to download a number of programs to conduct reconnaissance, enumeration (PowerView), lateral movement (PsExec), bypass antivirus software (KillAV BAT), and exfiltrate customer data (PuTTY Secure Copy client).
The threat actors also attempted to steal passwords and tried to access backup servers and tamper with security software by means of a Bring Your Own Vulnerable Driver (BYOVD) attack , according to the third-party analysis.
According to Logi Point analysis, BlackCat had the fourth-highest number of victims, and has demanded its highest ransom at $14 million.
Given that the BlackCat group is known for attacking high profile targets, the use of SEO poisoning may cause their reach to extend to SMEs and general unsuspecting users.
Sentinel One has also flagged the ongoing use of SEO poisoning techniques, using a Blender 3D (open source 3D graphics software) SEO poisoning case study- where the first three search query results were malware copies of the legitimate webpage.
"SEO poisoning leading to malicious advertisements are the rising star in today’s crimeware malware delivery methods...Attackers are finding a large amount of success in such attack methods, and we can expect to see this method evolving to conceal effort even further," said Tom Hegel, of the cybersecurity platform.







