Fortinet, the steaming gift that keeps giving (to cybercriminals) has hurried out patches for yet MORE critical pre-authentication RCE vulnerabilities – one of which is “potentially” being exploited in the wild.
The vulnerabilities, disclosed February 8, were allocated CVE-2024-21762 and CVE-2024-23113 and allocated CVSS base scores of 9.6 and 9.8.
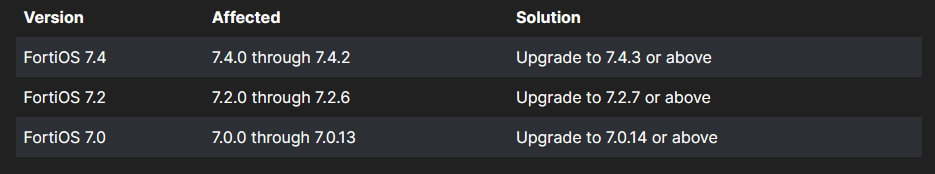
CVE-2024-21762 is an out-of-bounds write vulnerability in FortiOS (the vendor’s operating system for its VPN and other appliances) and “may allow a remote unauthenticated attacker to execute arbitrary code or command via specially crafted HTTP requests” said Fortinet on February 8.
Patches are now available and should be applied urgently. A workaround? “Disable SSL VPN (disable webmode is NOT a valid workaround)” it said.
It did not credit a researcher with the find.
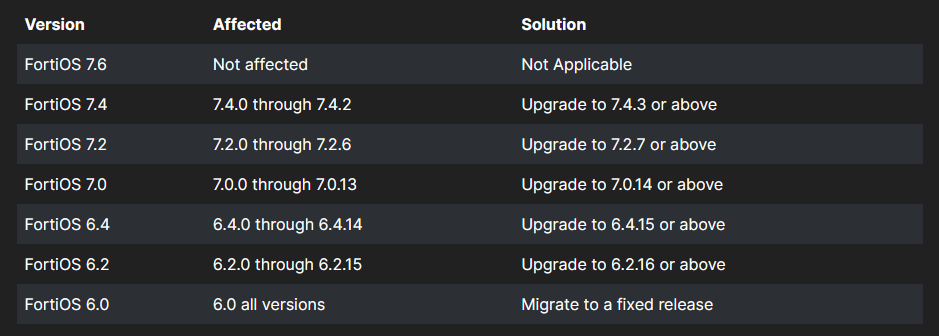
CVE-2024-23113, meanwhile, involves “use of externally-controlled format string vulnerability in FortiOS fgfmd daemon [that] may allow a remote unauthentified attacker to execute arbitrary code or commands via specially crafted requests,” Fortinet said in a short advisory the same day.
It credited its own Fortinet Product Security team with the find.
Fortinet appliances are widely deployed by enterprises – many of which appear to be lax at patching them. A case in point: One of the single most widely exploited CVEs in 2022 was a Fortinet vulnerability patched four years earlier (CVE-2018-13379). Its product security appears troublingly lax: CVE-2022-40684 was also widely exploited and let attackers gain access to “all management API endpoints"; CVE-2023-27997 meanwhile was “reachable pre-authentication (without any login needed), on every [Fortinet] SSL VPN appliance and also used to attack customers. There are well over a million devices running FortiOS on the internet and while certainly not all of those are exposed management interfaces, the number gives an indication of its ubiquity.
VPNs and network edge appliances are a compelling target for attackers and some are moving aggressively to boost product security
Ivanti on February 8, also patched another severe pre-auth RCE bug, allocated CVE-2024-22024. This was found during internal testing.
Its disclosure comes weeks after public disclosure of two critical vulnerabilities (CVE-2023-46805 and CVE-2024-21887) that chained together, let attackers bypass MFA remotely.
Public disclosure of those vulnerabilities in Ivanti Connect Secure VPNs triggered the threat actor to begin mass exploitation before organisations mitigate, with over 1,500 reported breached using the bugs.
Ivanti said this week that it has been "working around the clock to aggressively review all code and is singularly focused on bringing full resolution to the issues affecting Ivanti Connect Secure (formerly Pulse Connect Secure), Ivanti Policy Secure and ZTA gateways.
"We have been following our product incident response process and rigorously assessing our products and code alongside world-class security experts and collaborating with the broader security ecosystem to share intelligence. We are committed to communicating findings openly with customers, consistent with our commitment to security and responsible disclosure."
Organisations reliant on VPNs should, in The Stack's view, urgently reconsider this reliance. We repeat the words of the Department of Defence: "VPNs pose a threat to enterprise security. They create a path in the network perimeter and provide access to network resources after authentication. The conventional approach cannot provide a method to intelligently confirm the identities of users and entities attempting to access the network or provide adaptive policy enforcement based on authentication.”
As one COO told The Stack some years back: “IT's need to manage you on-network is going. Previously, for example, you would have to be on-network for us to manage your device. The rollout many people are doing at the moment [including SASE adoption] moves that management to the cloud. So you can be on-network or off-network and IT can still patch and vuln-test your machine.” [Things like Microsoft’s cloud-based endpoint management tool Intune help].
They added: “That's the same for SaaS apps; more and more people are doing SSO through [X vendor] or whatever so that need for on-premises is really going away. File servers tend to be the sticking point. If you haven't moved terabytes of files to the cloud, then you still have to get onto the networks..."









