A security researcher, possibly trolling hard or possibly looking to pad out their resume, drew amusement from hackers this week for trying to get CVEs (reference codes for software vulnerabilities) allocated against training aid applications specifically designed to be vulnerable.
The unknown security researcher initially managed to get CVE-2023-39848 and CVE-2023-39849 registered with Mitre for Damn Vulnerable Web Application (DVWA) and a similar tool called Pikachu – both of which are designed to have various security weaknesses for training purposes.
(Mitre, along with other organisations, allocates CVEs which are then reviewed by the National Vulnerability Database once published. They can then be marked "reject" if they are clownish, like these. The CVE code still gets added to the NVD; albeit it becomes non-searchable.)
Whilst many were wryly amused after CVEs were initially allocated to the vulnerabilities, if they had not been spotted as problematic it may have undermined the credibility of not-for-profit organisation Mitre and partner NVD which respectively assign and analyse CVE applications.
DVWA, developed by security professional Robin Wood, describes itself in its GitHub as a “ PHP/MySQL web application that is damn vulnerable. Its main goal is to be an aid for security professionals to test their skills and tools in a legal environment, help web developers better understand the processes of securing web applications and to aid both students & teachers to learn about web application security…”
(To really belabour the point for those a little low on coffee or brain cells: It’s a daft thing to have a CVE allocated for a vulnerability in a software application that was designed to be riddled with them…)
NVD rejected the DVWA CVE on August 17.
That decision was welcomed by DVWA’s creator Wood, who said on X, previously Twitter, that an email from the Mitre team was “my first interaction with CVEs and it gives me confidence that there are sensible people behind the program and it isn't just automated and ignored by humans.”
The to 731 people who have DVWA exposed to the internet, I apologise for CVE-2023-39848, I recommend you temporarily remove them from the internet till I can create a patch.https://t.co/bvaU97kvmn
— Robin (@digininja) August 17, 2023
“To the 731 people who have DVWA exposed to the internet, I apologise for CVE-2023-39848, I recommend you temporarily remove them from the internet till I can create a patch” he said meanwhile, sharing a Shodan map of “exposed” versions of the application. (Dear Reader: This was a joke.)
(Shodan is a widely used search tool to track the location and often ownership of vulnerable software or exposed infrastructure.)
The motivations of the “security researcher” in question, who had set up an account on GitHub under the handle KLSEHB just days earlier on August 15, remain unknown. The Stack has endeavoured to reach them and will update this if we hear back. NVD meanwhile notes that CVE-2023-39848 has been marked "REJECT" in the CVE List: “These CVEs are stored in the NVD, but do not show up in search results.”
DVWA SQLi CVE: OK, serious now...
KLSEHB had flagged (intentional) SQL injection vulnerabilities in DVWA.
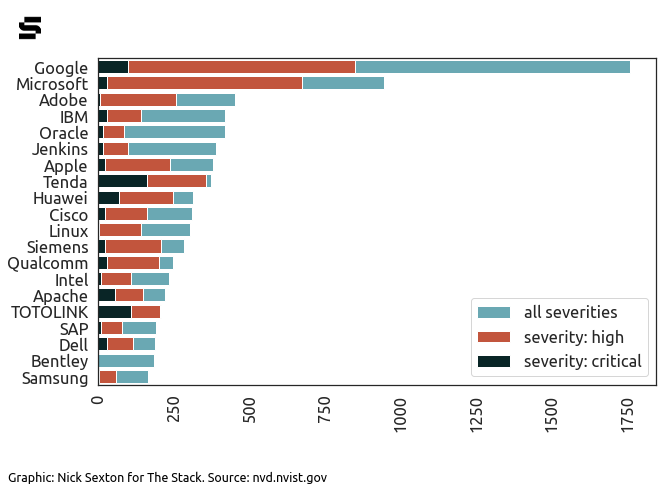
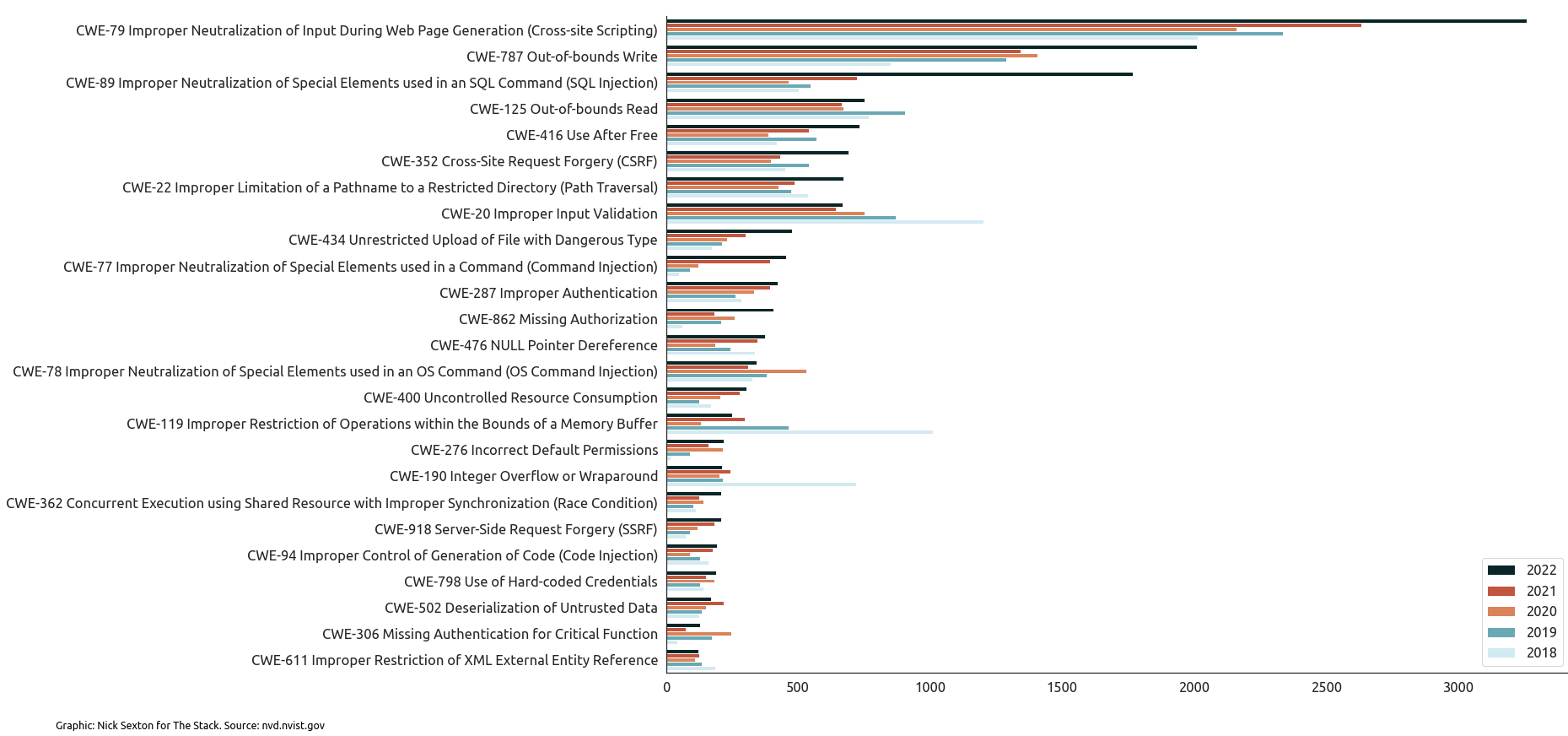
On a more serious note, analysis by The Stack earlier this year of 90,000+ CVEs in the NVD showed that CVEs allocated to SQL injection (SQLi) bugs continue to spike in numbers, as do common cross-site scripting (XSS) and memory corruption vulnerabilities that, in theory, should be easy to catch with some rudimentary fuzzing or testing.
The trend that suggests product security is hardly improving.
As David A. Wheeler, director of open source supply chain security at the non-profit Linux Foundation put it to The Stack in an August 2022 interview: “How did we get to this place where so much software, both open source and closed, has so many vulnerabilities? This is not an open source unique problem, this is a software problem. The short answer is, we're not teaching our developers anything… we have an endemic problem of not enough people knowing how to develop secure software.”
Perhaps DVWA can help. You can find it here. Just, you know, don't...








