In the world of malware, beaconing is the act of sending regular communications from an infected host to an attacker-controlled host to communicate that the infected host malware is alive and ready for instructions. It is often one of the first indications of a botnet malware infection, so it’s important to spot the beaconing behaviour before the infected host can expose data or launch an attack, writes Theresa Lanowitz, director, AT&T Cybersecurity.
Failing to detect beaconing behaviour calling out to command and control servers can lead to high risk malware infections that are much harder to thwart once they take hold of the network. Therefore, it is one of the most effective methods for threat hunting Security Operations Centre (SOC) analysts can use in order to take action quickly and prevent infection.
Investigating Beaconing Behaviour – A Case Study
At the end of 2020, AT&T Cybersecurity SOC analysts investigated an incident for a company in the information management software sector that has approximately 5,000 employees. The investigation began in response to an alarm triggered by outgoing TCP traffic to an IP address that was flagged by the AT&T Alien Labs Open Threat Exchange (OTX) as associated with foreign advanced persistent threat (APT) activity and malware communications.
The team conducted a further review of this IP address using additional open source intelligence (OSINT) sources and verified that the destination IP address had been involved in malicious activity and was considered a high threat. Due to the quick response time, the customer was able to isolate the infected asset and perform remediation before the malware caused any further infection on their network.
Initial Alarm Review
The initial alarm came from an event showing TCP traffic to a known malicious IP address coming from one of the customer’s internal assets. This IP address was correlated with malicious activity that had been found in OTX and from pulses created by AT&T Alien Labs, the threat intelligence team at AT&T Cybersecurity, monitoring active threats. Further review of the customer’s system showed possible beaconing activity had begun recently and was actively being blocked by their intrusion protection system, preventing further communications with the malicious IP address.
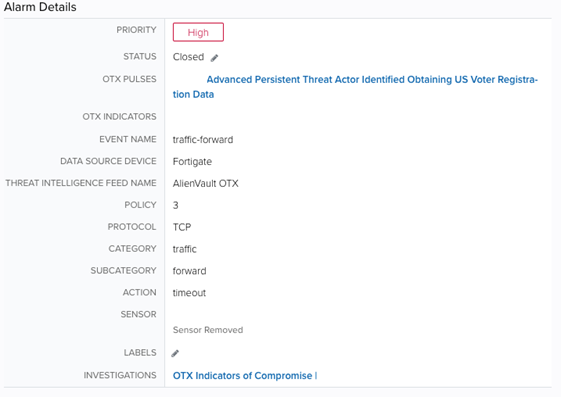
Expanded Investigation
Once this beaconing activity was discovered, the team conducted a 30-day review of the customer’s entire environment to look for signs of further intrusion. The original IP address was then analysed using a variety of OSINT sources to gather related Indicators of Compromise (IOCs) and other IP addresses that would indicate further intrusion had occurred. This review showed that no other assets had traffic involving the malicious IP address or other IOCs related to the APT, and that no other assets were exhibiting beaconing activity or lateral movement.

Response
The customer cited that due to the quick response and phone calls, they were able to identify and isolate the infected system before any further damage was done. This allowed the company to perform a more in-depth investigation without fear of missing other underlying activity that would have been difficult to correlate on its own.
Why Should a CISO Care about Beaconing
CISOs are our cybersecurity leaders – inside of the cybersecurity organisation and cross-functionally to fellow members of the C-suite. It is critically important that CISOs have the knowledge to understand the technical issues of what is happening in the SOC to make informed decisions on courses of action to prevent and manage attacks and breaches. Likewise, it is critically important for CISOs to communicate in business language, how cybersecurity missteps have an impact on the business.
The C-suite is not expected to understand the technical nuances of a cyber attack. However, it is incumbent upon the CISO to be able to explain why something needs to happen to remediate a breach.
For example, in the beaconing instance described in this article, CISOs need to identify the business risk and impact of allowing an infected asset to continue operating as well as what the infected asset means to the business. It is not so much the particular threat, in this case beaconing, rather how CISOs can communicate the business impact of what is going on. Does the infected asset contain formulas to new medications? Does the infected asset contain personal information of all employees? Does the infected asset contain company financial information? All of these are relevant business issues; and the CISO needs to communicate to the C-suite the impact of any business-critical information being stolen, released to the public, or what the adversary can do now that they have gained access to a particular area of information.
Breaches will continue to happen, it is the nature of cybersecurity defense that the adversaries are continuously pushing the boundaries of to identify ways to compromise an organisation - whether for monetary, political, or personal gain. CISOs should make sure their language matches their audience to communicate effectively and be welcomed to the C-suite. We should expect to see CISOs communicating in more relevant business terms as digital transformation journeys are accelerated by the varying phases of the COVID-19 pandemic.
CISOs are much more than the people who ask for money in their budgets for the security of the cyber aspect of a business and the people who bring bad news of an attack. A CISO is a fully fledged member of the C-suite working to help deliver strong business outcomes, while protecting mission-critical assets such as intellectual property, important business data, and sensitive information to maintain business resiliency.







