Two security vulnerabilities in AWS service “Amplify” made IAM roles “assumable by anyone in the world” say security researchers at Datadog.
AWS has now made changes to AWS Security Token Service and also its IAM control plane, to mitigate the bug – allocated CVE-2024-28056.
Although only one CVE has been allocated and the vulnerabilities are closely related, the first security fix did not automatically resolve the second associated bug, so The Stack is referring to them in the plural.
AWS has published a security advisory here.
(Amplify is a suite of tools for app development using cloud services.)
See also: As NVD flatlines amid rumours of borkage, infosec pros call for urgent action
Critically, “an adversary abusing this vulnerability would not only have initial access to the AWS account—they would also have privileges over resources under the purview of those roles… Across Datadog customers, we found vulnerable IAM roles that had a variety of ‘full access’ policies attached, including AmazonS3FullAccess…” Datadog said on April 15.
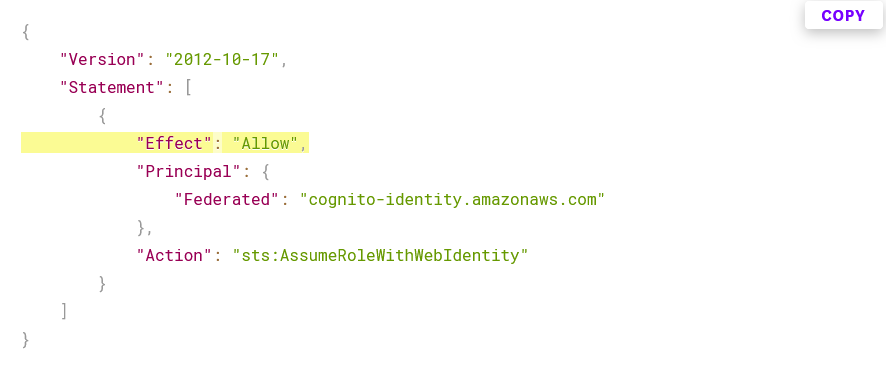
It has urged AWS Amplify customers to perform “an audit of your roles and potential threat activity," adding "if an external adversary attempted to assume a role in your AWS account using this technique, the activity would generate an sts:AssumeRoleWithWebIdentity CloudTrail event."
The AWS Amplify vulnerability, in brief.
A NIST CVE description sums up the bug succinctly:
"Amazon AWS Amplify CLI before 12.10.1 incorrectly configures the role trust policy of IAM roles associated with Amplify projects. When the Authentication component is removed from an Amplify project, a Condition property is removed but "Effect":"Allow" remains present, and consequently sts:AssumeRoleWithWebIdentity would be available to threat actors with no conditions. Thus, if Amplify CLI had been used to remove the Authentication component from a project built between August 2019 and January 2024, an "assume role" may have occurred, and may have been leveraged to obtain unauthorized access to an organization's AWS resources. NOTE: the problem could only occur if an authorized AWS user removed an Authentication component. (The vulnerability did not give a threat actor the ability to remove an Authentication component.) However, in realistic situations, an authorized AWS user may have removed an Authentication component, e.g., if the objective were to stop using built-in Cognito resources, or move to a completely different identity provider."
CVE-2024-28056 affected Amplify CLI versions prior to 12.10.1 and Amplify Studio, which uses Amplify CLI (which AWS describes as “a toolchain for simplifying serverless web and mobile development.”)
The bug was found by security researchers at Datadog and reported to AWS on January 9. The hyperscaler swiftly released a new version of the Amplify CLI the same day to ensure that no future roles will be exposed.
On February 29, it then released a patch to "prevent roles susceptible to the first variant from being created" as Datadog put it.
A second variant of the issue was not patched until April 8, more than a month after Datadog flagged to AWS that it was still exploitable.
AWS Amplify bug: CVE-2024-28056 had two flavours
It had two variants. For the first, under certain user conditions it made Amplify IAM roles “assumable by anyone in the world,” according to security researchers at Datadog. Customers would not have been aware of this. This affected customers between August 2019 and January 2024.
Crudely, if the user removed a certain Amplify authentication component (perhaps because they were moving to a different identity provider) it triggered behind-the-scenes Cognito (an authentication tool) changes that left "no indication that an AWS service or tool was exposing their IAM roles..."
In the second variation of the vulnerability, the “default, out-of-the-box configuration” meant that customers’ Amplify project IAM roles were assumable by anyone in the world. The latter bug affected anyone who created an Amplify project using a version of the Amplify CLI that was built between July 3, 2018 and August 8, 2019, Datadog determined.
CVE-2024-28056’s root was in an upstream open source AWS library. Datadog noted: “One challenge of cloud security research is that the services offered by cloud providers are often opaque. They take inputs and return outputs. Any changes to this are usually invisible to outside observers and researchers. However, this is a rare circumstance in which the vulnerable component is in an open source library, and as a result, we can track down when this vulnerable behavior was introduced.”
Datadog's technical analysis is here.
Earlier this week The Stack also reported on an AWS STS bug that gave read-only users admin access to AWS resources under certain conditions.
The bug was found by researchers at Stedi who admitted it was an “edge case” – but said that they were frustrated in their investigations by an IAM policy simulator that “does not support role trust policy evaluation.”
"“Proving the security of a system to grant federated identities access to IAM roles continues to rely on both positive and negative end-to-end tests with long test cycles. Developing more mature tooling would massively improve the developer experience, and we hope AWS will consider investing in this area moving forward," its team said in a blog on April 9.








