A new zero day -- or previously unknown security vulnerability for which there is no patch available -- was exploited more than once a week in 2021 according to Mandiant, which saw 80 zero days exploited.
Research from the incident response company suggests that zero day exploitation -- previously heavily the preserve of advanced persistent threat (APT) state actors -- is now also the domain of financially motivated crime groups: one third of groups it identified exploiting zero days in 2021 was financially motivated.
Among other incidents the company cited a Russian group attacking critical infrastructure networks with a zero day in a Sophos firewall product and the widely reported and effective use by Chinese espionage groups of the collection of "ProxyLogon" vulnerabilities to attack email servers en masse in January-March 2021.
Google, meanwhile, in its third annual review of zero days exploited in the wild, tracked 58; up dramatically from the 25 detected in 2020. Goog;e's Project Zero noted, however in its report, that "Attackers are having success using the same bug patterns and exploitation techniques and going after the same attack surfaces".
(Google found that when it came to Zero Day exploitation in 2021, 67% of all bugs were memory corruption vulnerabilities; "the standard for attacking software for the last few decades...")
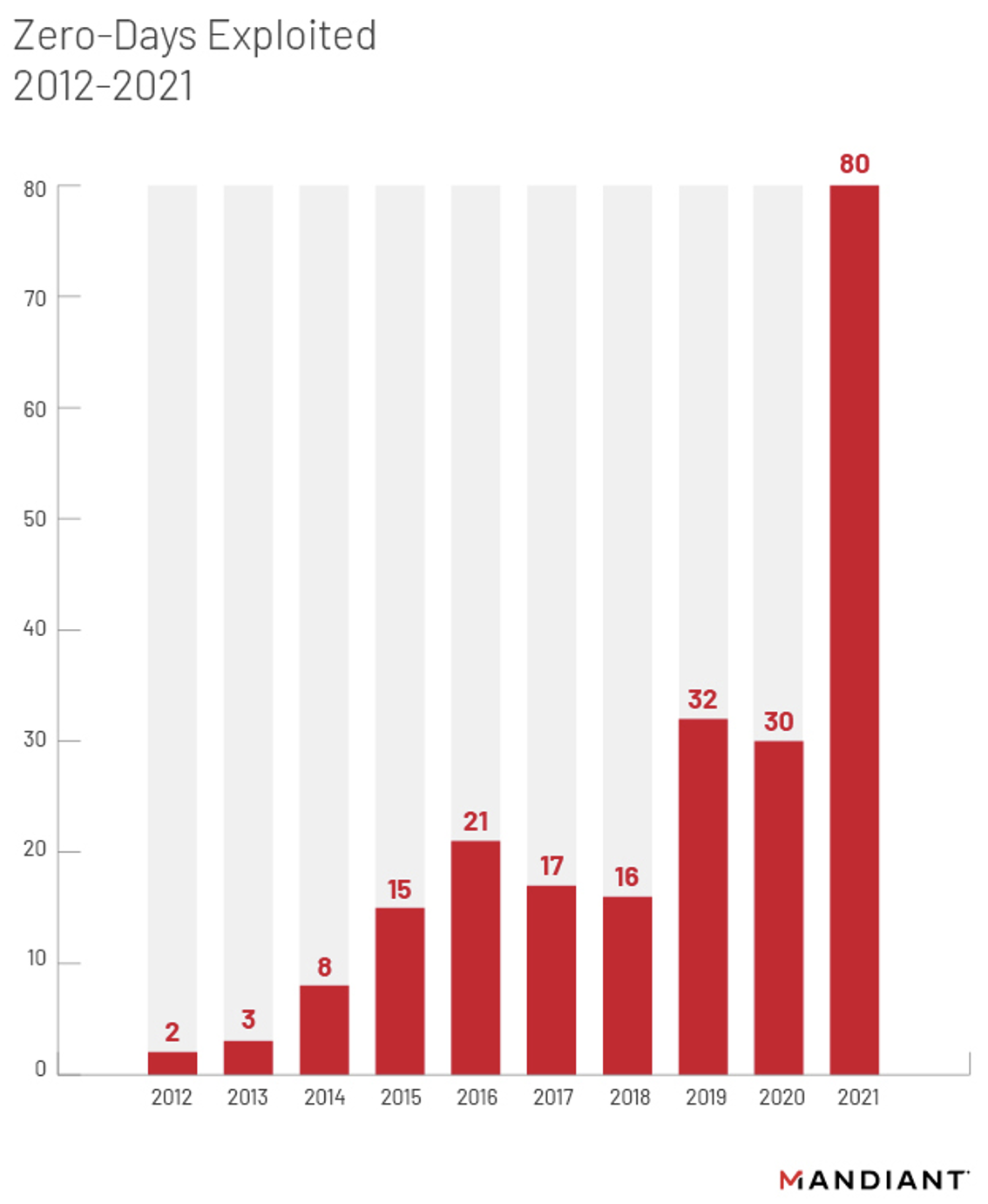
The company noted however that the sharp rise may be down to increased detection capabilities. Zero day use has no doubt been -- when necessary -- widespread among certain groups for years, but it is getting harder to get away with it without being spotted by security researchers as well as vendors operating and analysing their own telemetry to identify exploited bugs in their products.
Google's Maddie Stone said: "Kudos and thank you to Microsoft, Google Chrome, and Adobe who have been annotating their security bulletins for transparency for multiple years now! And thanks to Apache who also annotated their release notes for CVE-2021-41773 this past year.
"In-the-wild 0-days in Qualcomm and ARM products were annotated as in-the-wild in Android security bulletins, but not in the vendor’s own security advisories. It's highly likely that in 2021, there were other 0-days that were exploited in the wild and detected, but vendors did not mention this in their release notes. In 2022, we hope that more vendors start noting when they patch vulnerabilities that have been exploited in-the-wild. Until we’re confident that all vendors are transparently disclosing in-the-wild status, there’s a big question of how many in-the-wild 0-days are discovered, but not labeled publicly by vendors."
Project Zero's more detailed breakdown of Zero Days exploited in 2021 is here.
More broadly the US's Cybersecurity and Infrastructure Agency (CISA) is currently tracking 647 known exploited software vulnerabilities. (Security teams can subscribe to its update bulletin here.)









