
A cybercrime group called Dark Angels has reportedly extorted the world’s largest-ever ransomware payment from an unnamed victim.
Researchers from Zscaler claimed the gang extorted $75 million - nearly double the $40 million previously regarded as the highest publicly known ransomware payout in history.
The Zero Trust-focused security firm's ThreatLabz 2024 Ransomware Report also identified an 18% increase in ransomware attacks year-on-year between April 2023 and April 2024.
Dark Angels is known to use a variant of RagnarLocker to lock VMWare ESXi servers during attacks.
The number of victim companies listed on data leak sites has risen by almost 58% since last year, it found.
Zcaler warned that Dark Angels' success may "drive other ransomware groups to use similar tactics, reinforcing the need for organizations to prioritize protection against rising and ever-more costly ransomware attacks."
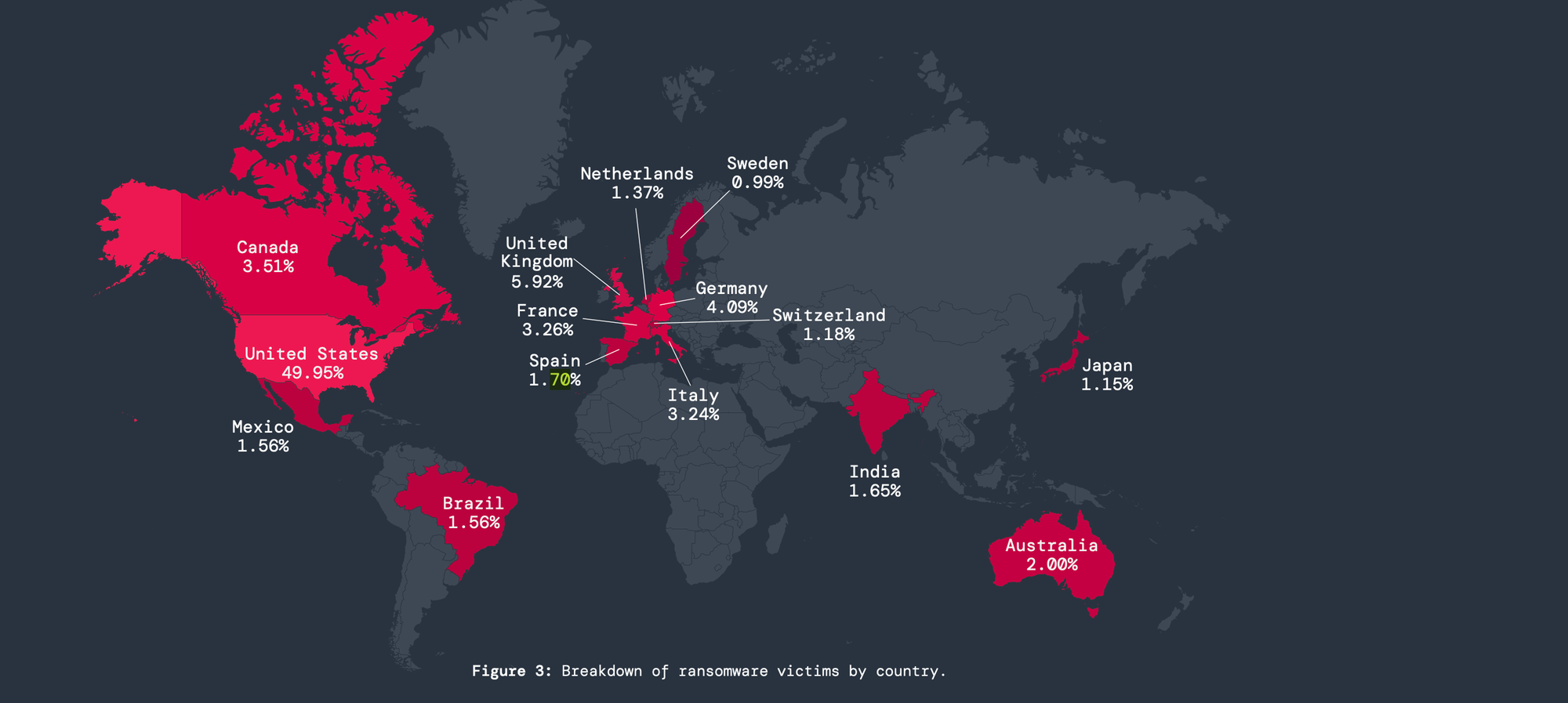
Its study also found that the US, Italy, and Mexico experienced the highest increase in ransomware attacks, with “staggering rises” of 93%, 78%, and 58%, respectively.
Shining a light on Dark Angels
Dark Angels targets various industries, including healthcare, government, finance, and education. More recently, it has been observed launching attacks against large industrial, technology, and telecommunication companies.
Zscaler wrote, "The Dark Angels group employs a highly targeted approach, typically attacking a single large company at a time. This is in stark contrast to most ransomware groups, which target victims indiscriminately and outsource most of the attack to affiliate networks of initial access brokers and penetration testing teams.
"Once Dark Angels have identified and compromised a target, they selectively decide whether to encrypt the company’s files. In most cases, the Dark Angels group steals a vast amount of information, typically in the range of 1-10 TB. For large businesses, the group has exfiltrated between 10-100 TB of data, which can take days to weeks to transfer."
Its "highest-profile attack" took place in September 2023, the security firm continued, when it "breached an international conglomerate that provides solutions for building automation systems" and other services. The group demanded a $51 million ransom, claimed to have stolen more than 27 TB of corporate data, and encrypted the company’s VMware ESXi virtual machines, deploying a RagnarLocker ransomware variant to encrypt the company’s files.
The relationship between RagnarLocker and Dark Angels is "not clear", Zscaler reported, but it is known that the group was using the ransomware prior to the law enforcement action against RagnarLocker, which resulted in the arrest of a key member in October 2023.
The group first emerged in 2022 using a ransomware strain that was "very closely linked" to Babuk - which was often used in double-extortion attacks. It then began using a variant that appears to be similar to RagnarLocker.
"ESXi lockers continue to prove successful for the ransomware groups who use them, yet the overall pool of unique Linux ransomware families remains narrow," wrote SentinelOne in research examining Dark Angels' techniques. "The Linux version of Dark Angels is a very lightly modified, more recent version of the analyzed RagnarLocker binary."
Sign up for The Stack
Interviews, Insight, Intelligence for Digital Leaders
No spam. Unsubscribe anytime.
Deepen Desai, Chief Security Officer at Zscaler, SAID: “Ransomware defence remains a top priority for CISOs in 2024. The increasing use of ransomware-as-a-service models, along with numerous zero-day attacks on legacy systems, a rise in vishing attacks and the emergence of AI-powered attacks, has led to record-breaking ransom payments.”
The most active ransomware "families" are LockBit, accounting for 22% of activity, BlackCat (also known as ALPHV) at 9%, and 8Base at 8%, Zscaler reported.
Zscaler also named Dark Angels, LockBit, BlackCat, Akira, and Black Basta as "the top five ransomware families to watch in 2024-2025."
The most targeted countries for ransomware attacks are the United States, with 49.95% of incidents, followed by the United Kingdom at 5.92%, Germany at 4.09%, Canada at 3.51%, and France at 3.26%.
Manufacturing was the industry "most targeted" by ransomware attacks, followed by healthcare, technology, education, and financial services.
It is worth noting that this alleged ransomware attack will not enter the history books properly until the victim is named - or the attack is verified further.
Do you know which company paid the ransom? Contact jasper@thestack.technology in confidence.