
The World Economic Forum (WEF) has published its first Global Cybersecurity Outlook – a report based on a survey of 120 global cyber leaders from 20 countries. If you are a cybersecurity professional, don’t stay up late reading it. A quick word search gives a flavour of what you are in for: “cyber” shows up a hefty 183 times; “digital” shows up 31 times; “cloud” gets just two mentions; “APIs” get a single aside; “MFA” does not appear at all, nor do “open source”, or "segmentation”. Even "CISO” oddly, does not appear in the report’s main text itself.
The word "Accenture" does, however, crop up 15 times and if we were being unkind, we'd argue that the publication appears aimed firmly at the class of executive who lives for management consultancy buzzword verbiage. A snapshot of the report, published January 18: “Frontier technologies like AI, robotics, quantum computing, the ever-evolving adoption of the internet of things (IoTs), cloud computing, blockchain and remote working/distance learning models represent the future of our digital world” it gushes earnestly.
This seems like a missed opportunity: some talented and respected CISOs were interviewed for the report. (The four co-authors from Accenture also made sure to interview six of their Accenture peers...)
The Stack recommends the NCSC's Board Toolkit.
That's not to say the WEF's first Global Cybersecurity Outlook is all recycled concerns and industry clichés.
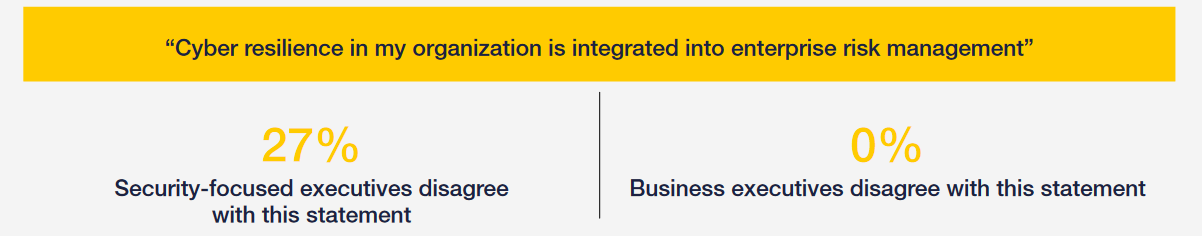
The report drives home the importance of improved understanding and communication between "security-focused leaders" and "business leaders" and points to some telling existing gaps. (See the graphic above.)
Some 92% of business executives surveyed for the report, for example, agreed that cyber resilience is "integrated into enterprise risk-management strategies" it emphasised, but only 55% of security-focused leaders surveyed agree with that statement, with many security leaders lamenting that they are not consulted in business decisions. This gap may have been widely reported but the extent to which it remains is noteworthy.
See also: Hiring a CISO (or want to be one?) Know this...
As BNP Paribas' Global Head of Cyber Risk recently noted to The Stack, that is not always the fault of business leaders. : "I actually feel that there’s been more effort from the business community; CEOs, the board to understand the world of technology… than technologists [trying to understand] what their business context is, and trying to really formulate the adequate architectural strategies to support that”.
The status quo clearly won't do. As Nancy Luquette, Chief Risk and Compliance Officer, S&P Global, USA notes in the WEF's report: “Looking ahead to 2022-2023, cybersecurity must be seen as a strategic business issue that impacts decision-making. To mitigate risks like ransomware and social engineering, organizations must ask not simply how they are protected, but how well – with an eye to strength, sophistication and efficacy.”
So far, so rather predictable, of course. And amid plenty of tired tropes about How Bad Things Are Out There and useless platitudes ("we need to get ransomware under control") about the rising cost of a breach, some generically couched concerns about supply chains and the resources of attackers, the WEF's Global Cybersecurity Outlook contains far too much entirely useless guidance parked alongside images of hooded hackers.
One favourite of ours: "Organizations should also seek out a platform-based cybersecurity solution that stops known ransomware threats across all attack vectors." Sounds great, doesn't it? We'll buy 10,000 seats.
Follow The Stack on LinkedIn
Where the report may prove useful for some is in driving home the importance of "cyber resilience" over "cybersecurity". (The WEF report's authors describe the latter in line with NIST's own definition as "the ability of an organization to transcend (anticipate, withstand, recover from, and adapt to) any stresses, failures, hazards and threats to its cyber resources within the organization and its ecosystem, such that the organization can confidently pursue its mission, enable its culture and maintain its desired way of operating.")
The ability to respond to and recover from an attack and assuming compromise, in short, are critical. While the report is not interested in any guidance on that front, a good disaster recovery strategy is pretty darn important and that includes quite possibly rethinking your backup strategy, as backups increasingly get taken out in attackers on even well-resourced companies. Oscar Arean, Head of Operations at Databarracks, noted to The Stack in the wake of the Kronos ransomware attack that, critically, you need to isolate your backups from your production environment. "You could do that with a physical air-gap, keeping backups on tape, or with network segregation. This is something that does catch out organisations with multiple data centres who backup between sites. If the backups are not sufficiently segregated, the single infection affects both systems."
See also: Kronos attack: backup access was crippled, as the software provider vows a cold storage overhaul
He added: "The other side to this challenge is having a separate environment to recover onto. Historically, for everything but a complete site failure, you would usually restore data back to the production site. With ransomware attacks however, that production environment is compromised and may be being used for investigation by cyber forensic teams. If you need to wait for that investigation to finish and the environment to be sanitised, it significantly delays the recovery (potentially by weeks). If you have a separate, clean environment to recover into, you can do both things concurrently and reduce the downtime. The public cloud is a great use case here because you can spin up the environment quickly and then fail-back and turn those resources off."
Stepping back somewhat from the report's survey percentages and shiny graphics, if there is arguably one key simple takeaway from the World Economic Forum's Global Cybersecurity Outlook for CIOs, CISOs, or any other leader of a technology function with an eye on security, it is this: "Encourage business leaders to take part in tabletop exercises, i.e. practice a cyber incident response. This approach heightens awareness of issues and risks that may jeopardize the operative success of incident response and underscores the importance of teamwork and learning from peers both inside and outside one’s organization or industry.
"Business leaders participating in such inclusive exercises, including tabletop exercises and beyond" the report sensibly suggests, "will acquire broader clarity on the importance of the implemented cybersecurity capabilities as well as on how to measure the effectiveness of incident response capability."
