
Microsoft took three years to patch a zero day dubbed Dogwalk that is now under active attack in the wild.
The remote code execution (RCE) vulnerability in the Microsoft Windows Support Diagnostic Tool (MSDT) was fixed today as one of August’s Patch Tuesday, which saw a bumper 121 new CVEs revealed.
These include numerous RCEs, with 17 of the vulnerabilities rated Critical and 102 rated Important
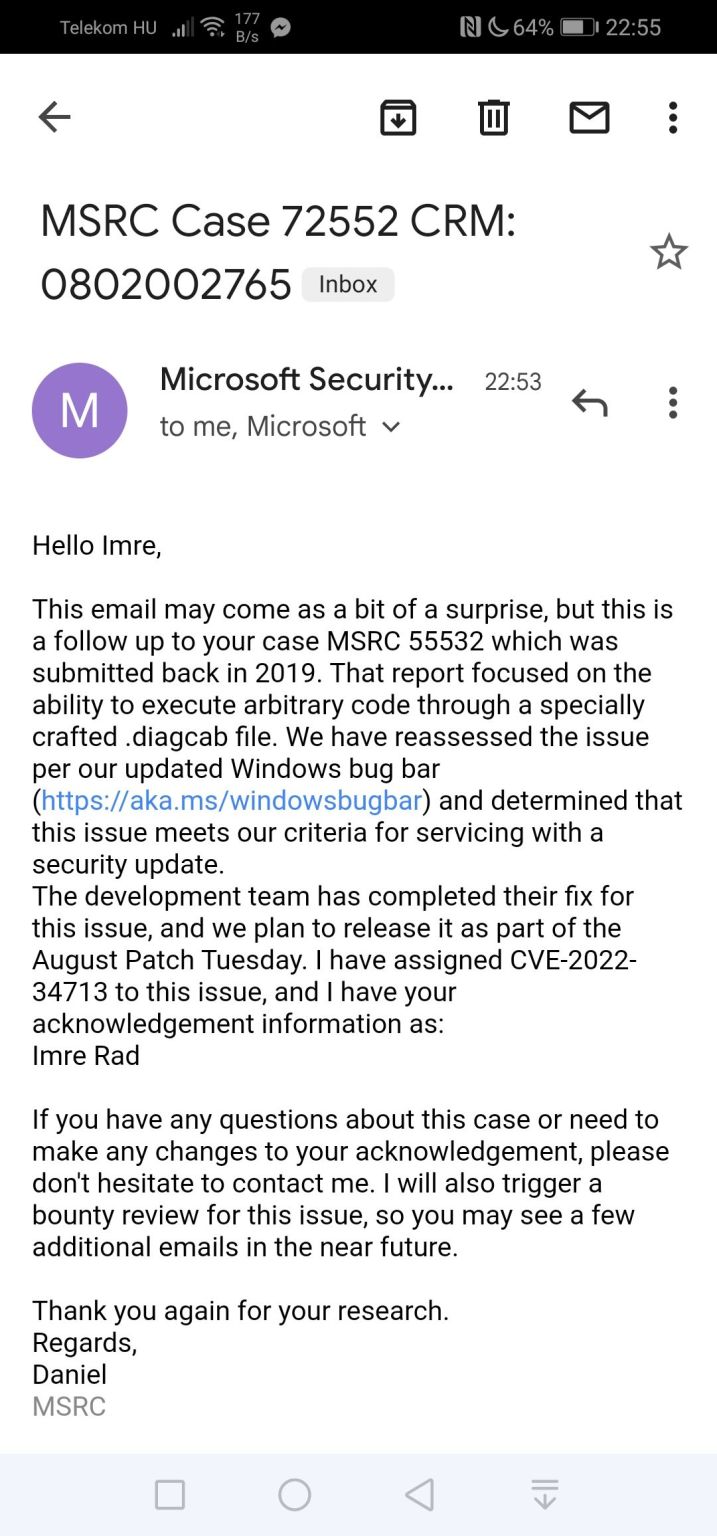
Among those that stands out is CVE-2022-34713.
That’s both for the fact that Microsoft says exploitation has been detected, meaning a prompt patch or mitigation should be a priority, but because Imre Rad, the Hungarian security researcher who reported the vulnerability (or at least a close variation of it), had reported it to Redmond back in December 2019.
https://twitter.com/spoofyroot/status/1557063659498549249
The vulnerability is in the same Windows diagnostic tool that was in the spotlight in May 2022 after another vulnerability – dubbed Follina and belatedly allocated CVE-2022-30190 by Microsoft – was also exploited in the wild. (Microsoft took its own time to respond to reports of that vulnerability too, initially responding to disclosures with the comment that it was “not a security issue” according to email screenshots.)
Hungary-based security researcher Imre Rad told The Stack: “This was/is a typical ‘convince the user to open this file’ type of attack; in other words it requires user interaction. No security warnings were shown (until recently, both Chrome and Edge have rolled out hardening around this). If the victim did open the file, attacker code was executed (in other words, could have access to whatever the victim did)...”
He posted a detailed blog on the vulnerability back in January 2020 after Microsoft said of his initial disclosure that it would not patch the issue and did not consider it a vulnerability. The bug requires an attacker to persuade a target to open a maliciously crafted .diagcab file. Rad in July 2019 had emphasised that “clicking on a non-executable file driven by an official Microsoft technology could save attacker-controlled content to any attacker-controlled location on the file system including shell:startup and thus accomplishing code execution”.
Microsoft initially said of Dogwalk zero day that "no security boundaries were bypassed"
Microsoft had initially responded that “there are a number of file types that can execute code in such a way but aren’t technically ‘executables’.. .diagcab is blocked by default in Outlook on the web and other places. The issue is that to make use of this attack an attacker needs to create what amounts to a virus, convince a user to download the virus, and then run it. Yes, it doesn’t end in .exe, but these days most viruses don’t. Some protections are already put into place, such as standard files extensions to be blocked, of which this is one.
“We are also always seeking to improve these protections. But as written this wouldn’t be considered a vulnerability. No security boundaries are being bypassed, the PoC doesn’t escalate permissions in any way, or do anything the user couldn’t do already” its security team said at the time of his vulnerability report.
For whatever reason, views at Redmond have now changed, perhaps after telemetry suggesting exploitation in the wild and the efforts of security researcher @j00sean who republished Rad’s 2020 research this summer, drawing it renewed attention in the wake of the Follina vulnerability. Rad’s Windows zero day was dubbed Dogwalk by the community over the summer. Microsoft describes today’s patch as for a “a variant of the vulnerability publicly known as Dogwalk” – Rad said he was unclear why, telling us that “this is either bad wording or someone indeed forked/improved my finding and started exploiting it in the wild”.
As ever, the Zero Day Initiative has a good precis of Patch Tuesday priorities here.
A record number of software security vulnerabilities continues to be reported monthly this year meanwhile – with 14,869 CVEs allocated by the end of July and numbers never dipping below 2,000 every month; a fresh record.
Data reviewed by The Stack suggests that 2022 will set new highs for reported security vulnerabilities as a result – if volumes continue at this rate, over 25,000 CVEs will be allocated this year; some 68 daily.
Unpatched software is one of the three most common entry points by cybercriminals to organisations’ IT systems, alongside malicious emails (phishing) and exposed communications protocols like RDP.
There were 21,957 CVEs allocated in 2021, data from US organisation NIST shows.
In 2021 Qualcomm, Zohocorp, Huawei, Google and Microsoft were the five companies with the most CVEs allocated to their products, while security vulnerabilities in the dominant Chrome browser (which has over 60% of global market share) accounted for the most CVEs by individual software product.
