Uber has confirmed that it is investigating a cybersecurity incident. After an initial breach the Uber hacker claims to have found an internal network share that contained Powershell scripts with privileged credentials that let them easily pivot to compromising Uber’s Duo (authentication), OneLogin, AWS, and GSuite environments.
"One of the Powershell scripts contained the username and password for a [sic] admin user in Thycotic (PAM)" they said in one widely shared post. PAM is "privileged access management" -- software that allows discovery of privileged accounts across multiple systems, infrastructure and applications and credentials management.
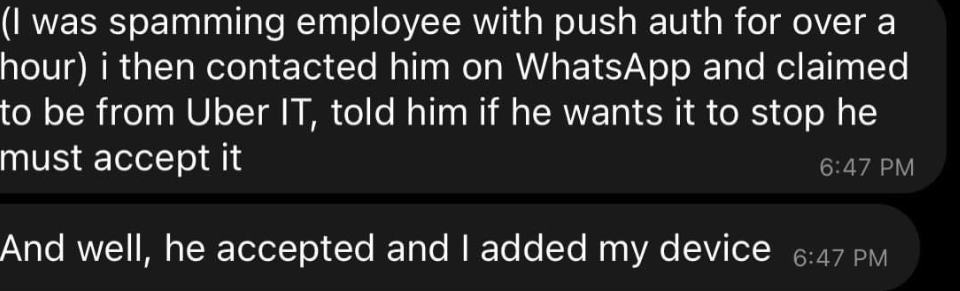
The New York Times, which first broke the story, suggests the initial breach involved a social engineering attack. How they were then able to so easily compromise what appears to have been almost all internal environments is a question that the company will have to answer anon; quite possibly in court as well if customer data is lost.
Follow The Stack on LinkedIn
Demonstrating the apparent extent of the compromise, the Uber hacker has shared several screenshots of Uber's internal environment, including their SentinelOne endpoint detection and response (EDR) portal, GDrive, VMware ESXi VMs and more. They announced the breach on Uber’s internal Slack where it was first seen as a joke.
https://twitter.com/Uber_Comms/status/1570584747071639552
Security researcher Bill Demikarpi noted: "Uber's AWS environment appears to be compromised as well. This screenshot of their IAM portal appears to show that the attacker has administrative access.
"If true, cloud access could not only include Uber's websites, but other critical internal services as well. The fact that [they] appear to have compromised an IR [incident response] team member's account is worrisome.
"EDRs can bake in ‘backdoors’ for IR, such as allowing IR teams to "shell into" employee machines (if enabled), potentially widening the attacker's access", he added.
According to Yuga Labs security engineer Sam Curry, the Uber hacker also had access to the company's HackerOne bug bounty program, where they commented on all of the company's bug bounty tickets. It is possible, as BleepingComputer notes, that they have downloaded all vulnerability reports that have not been fixed, presenting a further severe security risk to Uber, before they lost access to the HackerOne page.
Whilst many details of the incident remain unconfirmed, the attack comes in the wake of a flurry of sophisticated attacks that have begun with social engineering calls, emails or SMS texts. Over the summer Twilio was breached in such an attack and over 70 Cloudflare employees faced similar attempts; these took the form of texts to their cell phones that directed them to a phishing page was designed to look identical to a legitimate Okta login page. The phishing page prompted anyone who visited it for their username and password as well as asking for a Time-based One Time Password (TOTP) code. All of these were relayed to the attackers, who would then use it to (try) and access the company's actual login page, defeating most MFA implementations.
Although three employees fell for the attack, Cloudflare noted that it requires the use FIDO2-compliant hard security keys that are tied to users and implement origin binding, meaning "even a sophisticated, real-time phishing operation like this cannot gather the information necessary to log in to any of our systems."
FIDO2 is a web-authentication mechanism designed to mitigate real-time phishing—an attack that undermines multi-factor authentication by allowing an attacker to relay second-factor one-time tokens from the victim user to the legitimate website in real-time. Converting corporate users from password-based authentication to passwordless authentication using FIDO Authenticators "requires educational outreach" notes the FIDO Alliance, adding that "however, from a technical standpoint, the process is relatively simple." [pdf]
Needless to say if just one breach easily opens the floodgates to lateral movement that allows an attacker to access admin credentials for everything under the sun, there are other problems beside MFA.









