Security researchers at CrowdStrike have added Turkey and Colombia - labelled Wolf and Ocelot respectively - to their list of significant sources of cyber-threats in the 2022 CrowdStrike threat report. The addition “underscores the increase in offensive capabilities outside of governments traditionally associated with cyber operations, and highlights the variety of actor end goals" according to the report.
While it's not a rare occurrence for CrowdStrike to add new states to its list - Vietnam (Buffalo) was added last year - Adam Meyers, senior VP for intelligence at the firm, told The Stack: "I think it speaks to the proliferation of cyber intrusion activity. It's not every day but typically, we don't have a lot of new animals."
Turkey targets telcos
Turkey's operations have a specific named actor in the CrowdStrike threat report: Cosmic Wolf, which is also known as Sea Turtle, among other names. According to Meyers, CrowdStrike has spotted Cosmic Wolf targeting telecoms operations internationally: "That was something that very definitely hit the bar for us."
Meyers said the group has also gone after aviation, energy and government technology, and has targeted organisations in Switzerland, Sweden, Lebanon and within Turkey itself.
"When we see a threat actor like this, that is able to very actively engage in pretty widespread exploitation – there's lots of exploits they've used, some as old as 2009, some as new as last year, custom tooling – and that they're going after telecoms, and they're doing things to collect intelligence information that would be of interest to the target state, that kind of gets our attention," said Meyers.
Colombia goes after neighbours
Regarding Colombia's activity, he said CrowdStrike had tracked it for a number of years without it reaching a threshold where they regarded it as worth reporting, as its targets were mostly within Columbia, including groups such as FARC.
"But as they started branching out, that's when we decided to start to cover them," said Meyers, noting CrowdStrike has seen Colombia target states and organisations across Latin America, including Ecuador, Peru and Paraguay. He said more intel on both Wolf and Ocelot would be forthcoming - and that CrowdStrike planned to add a new state to its list in the near future.
2021 highlighted a shift in some attackers' preferred exploitation methods, according to the CrowdStrike threat report: "For years, Chinese actors relied on exploits that required user interaction, whether by opening malicious documents or other files attached to emails or visiting websites hosting malicious code. In contrast, exploits deployed by these actors in 2021 focused heavily on vulnerabilities in internet-facing devices or services."
The report noted Russia and Iran are also evolving their strategies; Russian actors Fancy Bear and Cozy Bear have both increasingly targeted cloud-based operations using credential-harvesting and authentication cookie theft, while Iranian actors focused on ransomware-based “lock and leak” tactics.
Last year also saw an 82% increase in ransomware-related leaks, and a 45% increase in the number of interactive intrusion campaigns, according to the CrowdStrike threat report. It also noted 62% of attacks don’t involve malware, but use “hands-on-keyboard activity” – including the use of offensive tools such as Cobalt Strike.
Meanwhile a report from Risk Based Security (RBS) said last year saw 28,695 vulnerabilities disclosed, up 23% year-on-year and the highest number recorded to date. RBS also highlighted how many disclosures happened outside the Patch Tuesday routine, with one non-Patch-Tuesday event resulting in information on 287 vulnerabilities being released in a single day.
Log4Shell sees exploits in the wild
Both RBS and CrowdStrike reports also made the scale of the Log4j vulnerability Log4Shell clear, with RBS categorising it as a “mega-vulnerability”, and CrowdStrike noting several real-world exploits involving Log4Shell, mostly by ecrime actors.
“There are too many vulnerabilities for organizations to remediate all of them, and they are being disclosed too quickly for organizations and security teams to keep up with. As usual, this includes CVE / NVD. In a world where issues like Log4Shell can appear at any time, organizations need proper vulnerability intelligence in order to make risk-based decisions,” noted the Risk Based Security 2021 report.
News of a vulnerability in Log4j rocked the world in December 2021, and it’s becoming clear just how significant the Log4Shell issue is. RBS showed how Log4Shell compares to other mega-vulnerabilities such as POODLE or Spectre:
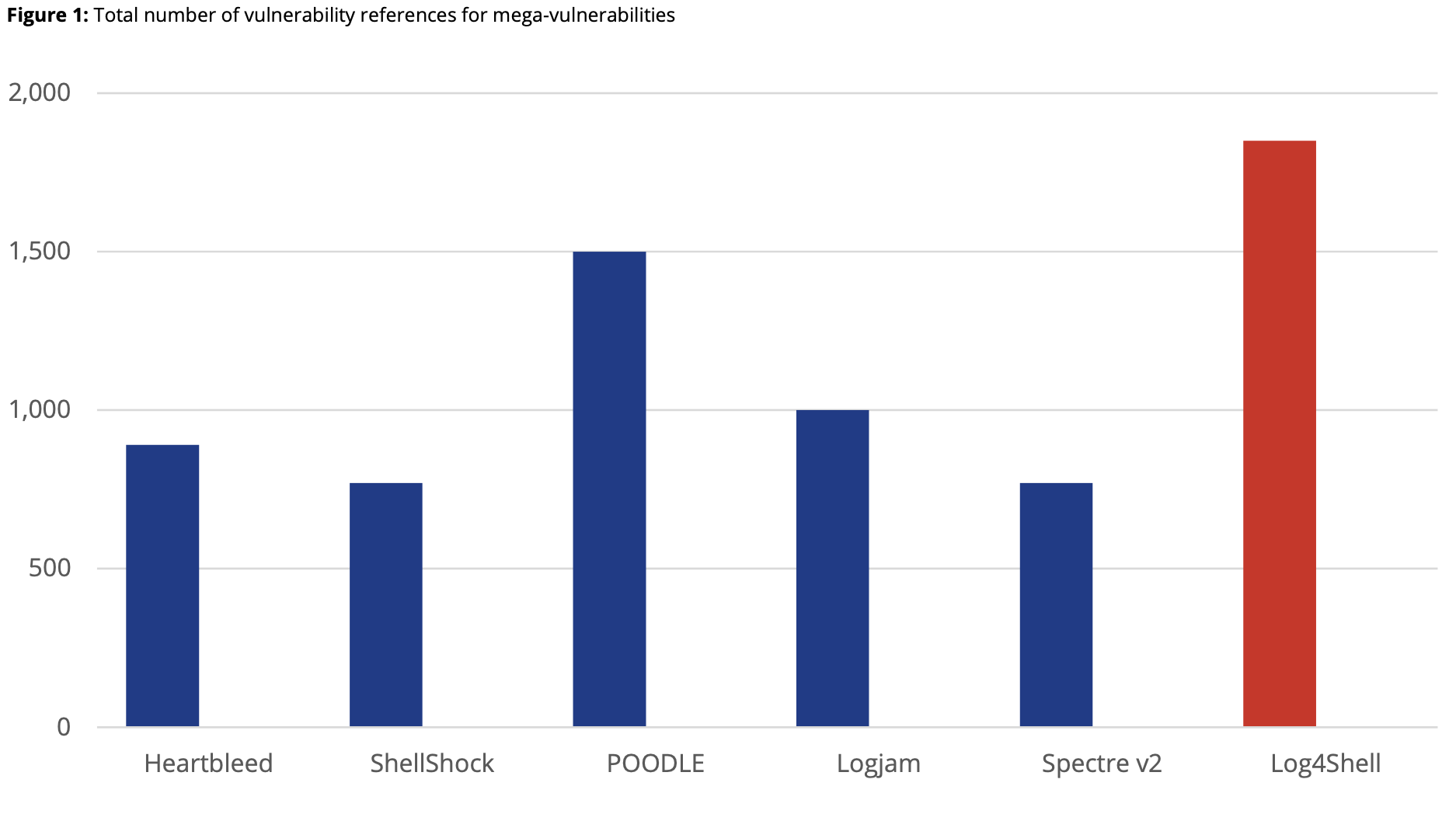
“Most mega-vulnerabilities take years to accumulate references and affected vendors/product information. But in just a month, Log4Shell has surpassed every other mega-vulnerability, except for one. At this time, there are over 1,850 vulnerability references specifically citing Log4Shell and its variants, and they affect over 6,200 vendors/product combinations. Of those, over 275 are unique vendors and 1,677 unique products, meaning that some organizations will likely be impacted several times over,” stated the RBS report.
RBS also noted the proliferation of cloned GitHub repositories containing Log4Shell exploits, even as GitHub tried to remove them.
While real-world exploitation of Log4Shell has not been as dramatic as feared, the CrowdStrike Threat Report detailed some of the attackers making use of the vulnerability: “Between Dec. 9-31, 2021, a variety of groups incorporated Log4Shell exploitation into their arsenal. Opportunistic eCrime actors aggressively engaged in widespread Log4Shell exploitation most commonly affiliated with commodity botnet malware (e.g., Muhstik).
“However, other eCrime-focused actors — including affiliates of DOPPEL SPIDER and WIZARD SPIDER — adopted Log4Shell as an access vector to enable ransomware operations. Additionally, state-nexus actors, including [Iran’s] NEMESIS KITTEN and [China’s] AQUATIC PANDA, were also affiliated with probable Log4Shell exploitation before the end of 2021.”
Vulnerability triage
With so many new vulnerabilities coming to light, organisations cannot hope to deal with them all and need to prioritise, said RBS: “4,108 vulnerabilities disclosed in 2021 were remotely exploitable, with both a public exploit and documented solution information. By focusing on these issues first, organizations can potentially reduce their risk and immediate workload by nearly 86%.”
They also noted a substantial number of new vulnerabilities aren’t recorded in CVE or NVD, or have a “reserved” ID: “CVE / NVD’s inability to report on 33% of 2021’s vulnerabilities results in a loss of visibility for organizations seeking to replicate the best practice of focusing on remotely exploitable vulnerabilities that have a public exploit and also a documented solution.”









