
Attacks on the software supply chain have surged 650% in a year, according to a new report by Sonatype that tracked 12,000 software supply chain attacks over the past year, compared to just 929 in 2019-2020.
Sonatype (a software supply chain management platform provider)'s seventh State of the Software Supply Chain Report tracked the attacks alongside a broader growth in open source activity: it projects that in 2021, developers around the world will borrow more than 2.2 trillion open source packages or components.
Their report comes as Microsoft pushes out a hugely critical patch for an alarming (CVSS 9.8) vulnerability in Azure -- unauthenticated RCE as root, no less -- that has its roots in an open source component.
The alarming security vulnerability was one of four related bugs reported by the research team at Israeli cloud security specialist Wiz. Allocated CVE-2021-38647 and dubbed "OMIGOD" it has its roots in an open source component, Open Management Infrastructure (OMI) that is used extensively by Azure services, including Open Management Suite (OMS), Azure Insights, and Azure Automation. (Wiz notes that "when [Azure] users enable any of these popular services, OMI is silently installed on their Virtual Machine... as root with the highest privileges.
"Any user can communicate with it using a UNIX socket or via an HTTP API when configured to allow external access. As a result, the vulnerabilities we found would allow external users or low-privileged users to remotely execute code on target machines or escalate privileges... Some Azure products, including Configuration Management, expose an HTTPS port (port 5986) for interacting with OMI. That’s what makes RCE possible. Note that most Azure services that use OMI deploy it without exposing the HTTPS port." (Read Wiz's write-up here).
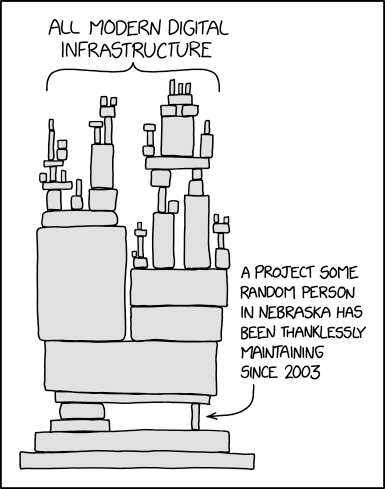
"The million-dollar question", Wiz asks...
"... Is how does an open source component with only 20 contributors on GitHub affect the security of large portions of Azure?
"The ease of exploitation and the simplicity of the vulnerabilities makes us wonder if the OMI project is mature enough to be used so widely. Yet this scenario is more common than you might think and certainly not unique to Microsoft. One of the benefits of open source is that it’s easy for developers to grab code from different projects and mix it with other open source and proprietary software. As a result, bad open source code can wind up in an enormous range of products and services – inadvertently becoming a 'single point of failure.'
Software supply chain attacks: analysis reveals depth of challenge
That's a point Sonatype also drives home -- noting that 29% of the top 10% (stay with us) of the most popular Java, JavaScript, Python, and .NET projects contain at least one known security vulnerability. Some 356,808 Java packages, 81,731 Python packages, 27,288 .NET packages and 250,002 JavaScript packages (in the Maven Central, PyPI, NuGet Gallery and npm package managers respectively) have a critical CVSS 9.0 or higher vulnerability, Sonatype found.
Houston, we have a clear problem.
The report comes after another report by security firm BlueVoyant earlier this year (based on a survey of more than 1,500 CISOs, CIOs, and Chief Procurement Officers from the US, UK, Singapore, Switzerland and Mexico) found 77% had "limited visibility around their third-party vendors" (let alone the components they were using) and 80% having suffered a third-party related breach in the past 12 months.
“This year’s State of the Software Supply Chain report demonstrates, yet again, how open source is both critical fuel for digital innovation and a ripe target for software supply chain attacks,” said Matt Howard, EVP of Sonatype. “While developer demand for open source continues to grow exponentially, our research shows for the first time just how little of the overall supply is actually being utilized. Further, we now know that popular projects contain disproportionately more vulnerabilities. This stark reality highlights both a critical responsibility, and opportunity, for engineering leaders to embrace intelligent automation so they can standardize on the best open source suppliers and simultaneously help developers keep third-party libraries fresh and up to date with optimal versions.”
