
Story updated 10:15 March 18 with response from GitHub
A supply chain attack potentially leaking secrets at thousands of organisations though a compromised GitHub action has been flagged by the platform.
Changes to the tj-actions/changed-files GitHub Action, used in more than 20,000 repositories, had injected malicious code to print credentials for systems running the action into build logs.
StepSecurity, which spotted the bad commit, said: “The compromised Action prints CI/CD secrets in GitHub Actions build logs.
“If the workflow logs are publicly accessible (such as in public repositories), anyone could potentially read these logs and obtain exposed secrets.”
CVE-2025-30066 emerged around 4pm UTC on March 14th and was spotted in most versions of the changed-files action before the commit was reversed by GitHub by the evening of March 15th.
The affected code is part of the GitHub Actions CI/CD platform, which allows users to reduce repeated code by using an action to complete a "complex but frequently repeated task."
Despite the flaw now being fixed, GitHub advised those running the code to review their workflows for unexpected output under the changed-files section and update them accordingly.
Those running the action have also been prompted to rotate any secrets that may have been exposed while the malicious code was running, with Open Source security platform Sysdig advising even private repositories to do the same.
Sysdig's Michael Clark said: "Although the exposure risk is slightly lower, any private repository using the affected action should treat its secrets as potentially compromised."
When working normally, the changed-files action is used to "track all changed files and directories relative to a target branch, the current branch (preceding commit or the last remote commit), multiple branches, or custom commits returning relative paths from the project root."
The changed-filed attack follows a similar template to other GitHub-based attacks, using popular code pulled into a wide range of repositories to extract confidential information through public code often not given a second thought.
See also: Mike Hanley, CSO, GitHub on “guns, gates, guards”, AI, ignoring the “flashy stuff”
It was a busy weekend for GitHub attackers with a phishing campaign also affecting the platform’s users, sending thousands a message warning of a “Security Alert” linked to a supposed login attempt in Iceland.
Those sent the alert were prompted to click one of several links purported to lead to security fixes but instead prompting users to allow account access by a fake “gitsecurityapp” OAuth app with a wide range of permissions.
If approved, the attackers would have had full access to a user's repositories, profile, gists, workflows and discussions, as well as read-only access for organisation and team memberships.
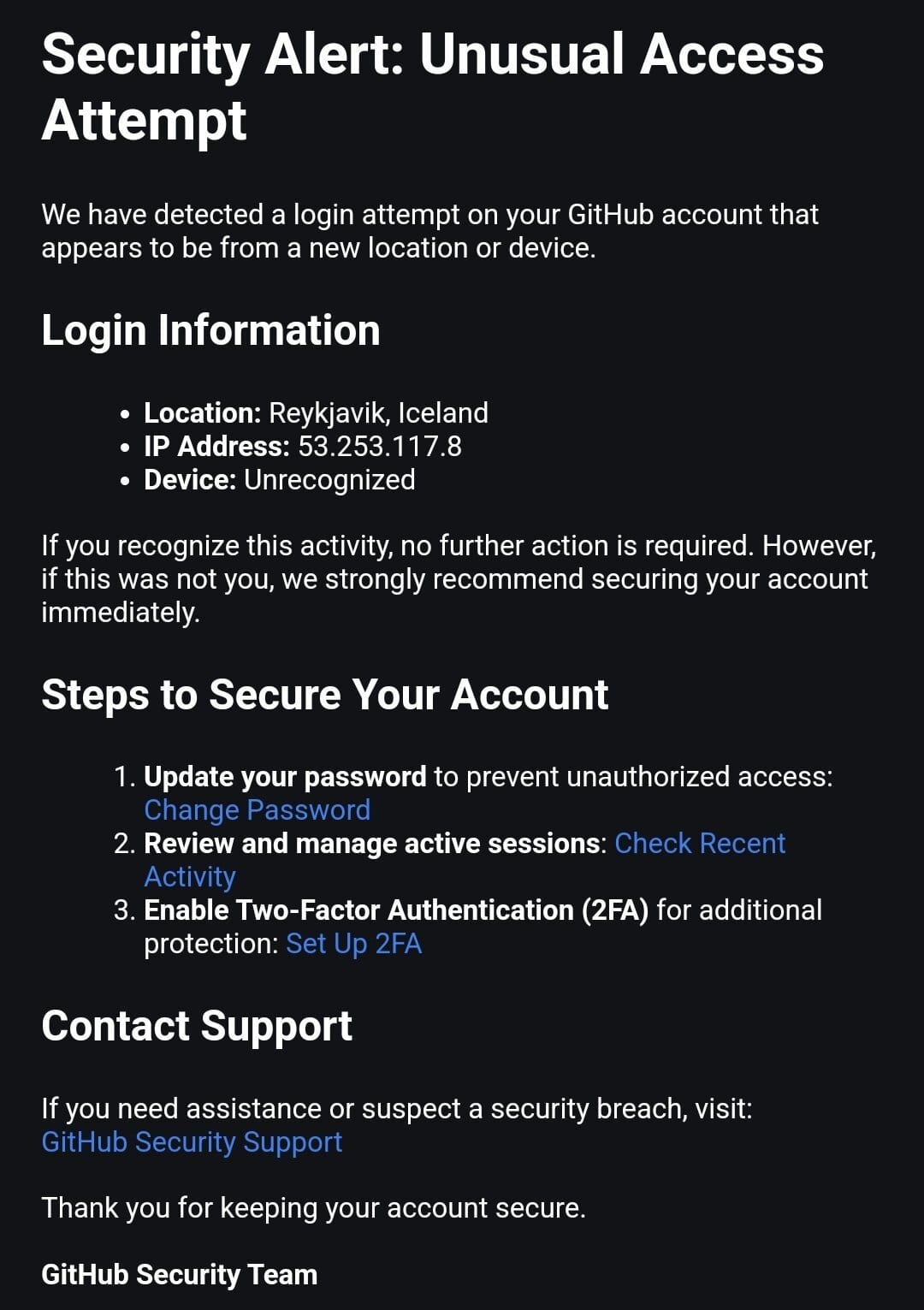
The campaign, spotted by cybersecurity researcher lc4m and first reported by Bleeping Computer, appeared to reach at least 8,000 accounts.
GitHub told The Stack: "GitHub is committed to investigating reported security issues. We are aware of this activity and are actively investigating. There is currently no evidence to suggest a compromise of GitHub or its systems.
"As our investigation continues, we recommend users review their authorised OAuth apps and immediately revoke access to any apps that are unfamiliar or suspicious."
Sign up for The Stack
Interviews, Insight, Intelligence for Digital Leaders
No spam. Unsubscribe anytime.
