A US man has been indicted for hacking the SEC’s X (previously Twitter) account and using it to pump up the price of Bitcoin earlier this year.
An indictment suggests that he pretended to be an FBI employee as part of a social engineering campaign to gain access to the X channel.
Eric Council Jr., 25, of Athens, Alabama, was arrested by the FBI on the morning of October 17. He had used his access to the channel to post that the markets watchdog has approved bitcoin Exchange Traded Funds.
The false post sent the price of the cryptocurrency soaring by $1,000.
An indictment by the Department of Justice alleges that Council and his unnamed co-conspirators engaged in a fairly sophisticated social engineering campaign to gain access to the SEC’s X account and bypass two-factor authentication (2FA), using a so-called SIM swapping attack.
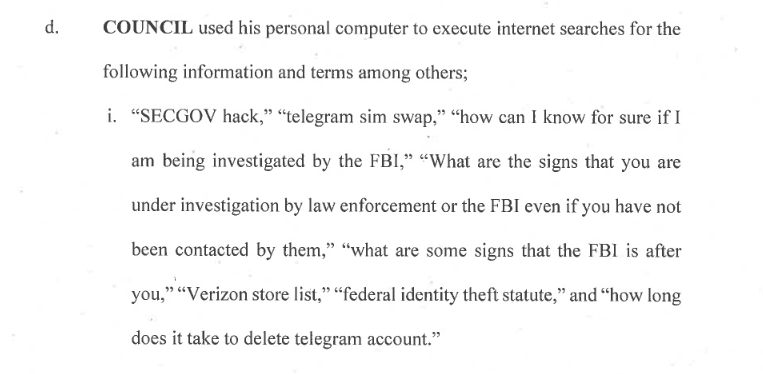
Despite efforts to cover his tracks including the use of encrypted messaging services and a burner phone, Council Jr somewhat let himself down on the operational security front by later searching, from his home computer: “SECGOV hack”; “how can I know for sure if I am being investigated by the FBI?”, “federal identity theft statute” and other gems.
n.b. To be fair, the indictment does not explicitly say that he did this without attempting to cover his tracks; law enforcement access to VPNs is not unknown and questions abound over the opacity of Tor in the face of a potentially aggrieved three letter agency; we’ll imagine a vanilla Google search from the “private” tab of a normal browser, for comedy value.
Social engineering opened the door
Those amused by such things may be somewhat less amused by the lengths Council Jr and his co-defendants allegedly went to gain access to the account, including getting a photograph of a federal employee to add to a fake ID card they created as part of a SIM swapping attack on the SEC.
An unnamed co-conspirator had identified the employee as having “authorized access over the telephone number linked to the SECGov X account” – the indictment does not reveal how they had done this.
They created a fake ID card in this employee’s name and went to an AT&T store where Council Jr pretended to be an FBI employee who had broken his phone and needed the number porting to a new SIM, where they could capture the 2FA code generated when they added the X password.
What’s SIM swapping?
SIM swapping is when little or large scumbags convince a telco that they’re you and you’ve lost your phone, saying ‘oh gosh, pretty please allocate this new SIM card I bought to the number; here’s my fake ID’.*
An investigation by the Cyber Safety Review Board (CSRB) into this tactic by various groups in 2023 suggested limply that telcos were hamstrung in terms of their ability to do anything about this, due to limited verification technology and the need for “low-friction customer experience.”
Lessons from the Lapsus$ attacks
The CSRB report [pdf] was written in the wake of a string of high-profile attacks on organisations including technology vendors by a threat group dubbed Lapsus$. This loosely knit group, the CSRB noted “exploited systemic ecosystem weaknesses to infiltrate and extort organizations, sometimes appearing to do so for nothing more than attention and public notoriety.”
SIM swapping was among the group’s favoured approaches. As the CSRB noted, “If richly resourced cybersecurity programs were so easily breached by a loosely organized threat actor group, which included several juveniles, how can organizations expect their programs to perform against well-resourced cybercrime syndicates and nation-state actors?”
More phishing-resistant MFA please
“A lucrative SIM swap criminal market further enabled this pay-for-access to a target’s mobile phone services. Despite these factors, adopting more advanced MFA capabilities remains a challenge for many organizations… due to workflow and usability issues,” it added.
The board urged organisations to adopt FIDO2-compliant, phishing-resistant MFA methods; something that even major technology vendors like Microsoft have only recently started to roll out at scale.
It also called for regulators to work on “incentivizing better security at telecommunications providers” to reduce SIM swapping attacks: "The Board heard that improving these processes is challenging, as telecommunications providers need to maintain low-friction customer experiences for a wide range of user needs and account for unique and emergent situations, including domestic abuse, loss of identification cards, and global travel. Furthermore, the carriers currently have limited options for identity verification and other solutions may not be scalable."








