
The FBI and Cybersecurity and Infrastructure Security Agency (CISA) have called for satellite communications users to "implement independent encryption across all communications links leased from, or provided by, your SATCOM provider" -- amid what they described as "possible threats" to both US and international satellite communication (SATCOM) networks. The alert comes in the wake of an attack on Viasat's KA-SAT services.
Commercial SATCOM users may find that harder than they would like. As one expert, Dr James Pavur, has noted, "security practices used by terrestrial internet customers, such as end-to-end VPN encryption, were not designed for compatibility with the traffic optimizations used in satellite broadband services... Satellite signals travel immense distances and are subjected to significant packet loss and latency as a result... the use of VPNs and customer-implemented end-to-end encryption results in significant performance reductions."
(The result, Pavur noted in 2021, is that "satellite broadband users have no good options. They (or their ISPs) must purchase expensive and unvetted proprietary applications, accept the substantial performance hit caused by general-purpose VPNs, or transmit sensitive data in clear text over massive satellite footprints.")
Joe Biden: "Lock your digital doors"
US President Joe Biden meanwhile late Monday emphasised "evolving intelligence that the Russian Government is exploring options for potential cyberattacks" and called on "the private sector and critical infrastructure owners and operators" to "accelerate efforts to lock their digital doors" in a brief statement.
The separate call for independent encryption use on March 17 – arguably a landmark one after years of demonisation of E2EE by many senior western policy makers – came in a joint FBI/CISA alert that also urged all SATCOM organisations to "significantly lower their threshold for reporting and sharing indications of malicious cyber activity".
It was not immediately clear if a specific piece of intelligence or incident triggered the alert. On February 24, however, Russia invaded Ukraine. The same day, services from satellite connectivity provider Viasat's KA-SAT – which provided internet connectivity to Ukrainian military and police units – failed for some 30,000 users across Europe after a Russian cyber-attack.
UPDATED: Satellite communications provider Viasat on March 30 published its root cause analysis of the attack – saying a "misconfigured" VPN appliance was used to gain remote access to the trusted management segment of the KA-SAT network. The attackers then sent destructive commands to modems that overwrote key data in flash memory, rendering them inoperable. (They can be restored with a factory reset.) As well as commercial customers KA-SAT was providing internet connectivity to Ukrainian military and police units. Some 30,000 terminals across Europe were affected. The Viasat attack caused over 5,800 wind turbines generating some 11GW to lose remote access and monitoring capabilities in Germany. This incident was "localized to a single consumer-oriented partition of the KA-SAT network that is operated on Viasat’s behalf by a Eutelsat subsidiary, Skylogic" Viasat noted in its report.
CISA SATCOM alert: Use MFA, least privileges, no TELNET please, etc.
The FBI/CISA alert, published March 17 -- which includes some wearily familiar threat mitigation advice that would be pragmatic across any domain, including implementing MFA, looking out for insecure remote access tools/protocols, consistent patching and close scrutiny of existing trust relationships with IT service providers -- comes six weeks after the February 7, 2022 Annual Threat Assessment of the US Intelligence Community.
That report noted: "Russia continues to train its military space elements and field new antisatellite weapons to disrupt and degrade U.S. and allied space capabilities, and it is developing, testing, and fielding an array of nondestructive and destructive counterspace weapons—including jamming and cyberspace capabilities, directed energy weapons, on-orbit capabilities, and ground-based ASAT capabilities—to target U.S. and allied satellites.
"Russia is investing in electronic warfare and directed energy weapons to counter western on-orbit assets. These systems work by disrupting or disabling adversary C4ISR capabilities and by disrupting GPS, tactical and satellite communications, and radars. Russia continues to develop ground-based direct ascent ASAT weapons capable of destroying space targets in low Earth orbit" the annual intelligence community report concluded.
Satellite communications cybersecurity
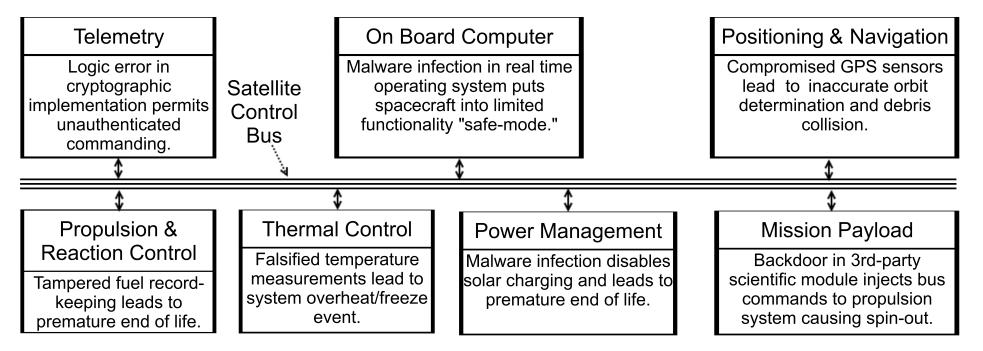
Bleeding edge weapons may not be necessary: satellite communications cybersecurity is notoriously poor. In 2020 an Oxford University-based security researcher used £270 ($300) of home television equipment to capture terabytes of real-world satellite traffic — including sensitive data from “some of the world’s largest organisations”; demonstrating that an attacker can intercept and even modify VSAT connections using standard satellite television equipment and creating a purpose built forensic tool dubbed “GSExtract” designed to “recover sensitive IP traffic from even highly corrupted maritime VSAT feeds collected on consumer-grade equipment.”
As the author of this useful mischief, James Pavur noted at the time, a lack of encryption was among the many reasons grabbing this data was so easy. The Rhodes scholar's recently published doctoral thesis further emphasises that "status quo practices (often enshrouded in layers of governmental and commercial classification) have struggled to keep abreast of growing attacker capabilities and system complexity."
He added: "The security of many keystone aspects of modern space missions have never been assessed... Without robust and open security protocols which consider the unique demands of space, attackers will continue engaging in sophisticated eavesdropping, injection, and spoofing attacks. This goes beyond the academic task of inventing crypto-systems. Many well-studied proposals, such as SatIPSec, have been largely ignored."

See also: A 'cyber sandbox' for hackers in space
As Dr Pavur noted to The Stack this week: "Any customer end-to-end encryption that hides TCP headers will suffer performance issues over GEO unless it's specifically designed to account for that latency. Any end-to-end encryption at the application layer should be alright, but will leak TCP and IP headers over the air."
Pavur has open-sourced a tool called QPEP in a bid to tackle the issue.
Built around the open QUIC transportation protocol and written in Go, the encrypted-by-default "PEP" or Performance Enhancing Proxy reportedly halves average page load times compared to traditional VPNs while concealing traffic from eavesdroppers and ISPs. A peer reviewed paper on QPEP was presented at the Network and Distributed System Security Symposium (NDSS 2021), February 2021 and can be seen here.
QPEP does not yet appear to have been deployed in commercial or other production.
SATCOM folks may want to take a closer look. Paging Elon Musk...
