
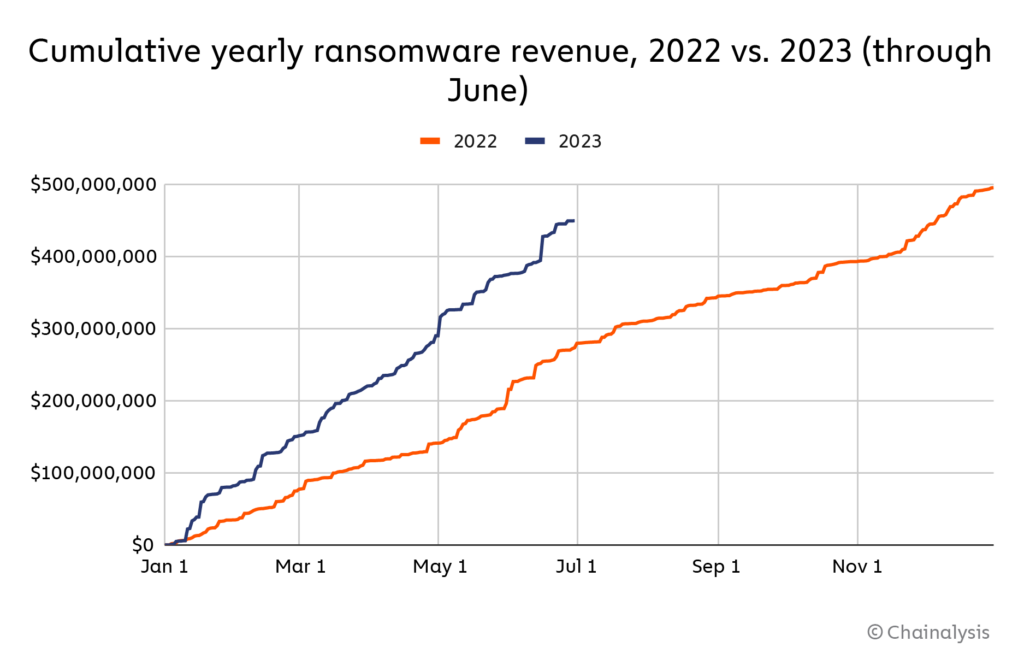
Ransomware is on track to deliver criminals $898.6 million this year according to Chainalysis, a specialist in blockchain data; earning attackers over $3 million every single working day in the first half of 2023.
With ransomware payments in 2023 already hitting $449.1 million in the first half, the figures are on track for the second-highest level ever after 2021’s $939.9 million, with the company attributing the rise – after a lull in 2022 – to the return of “big game hunting” and extreme extortion tactics.
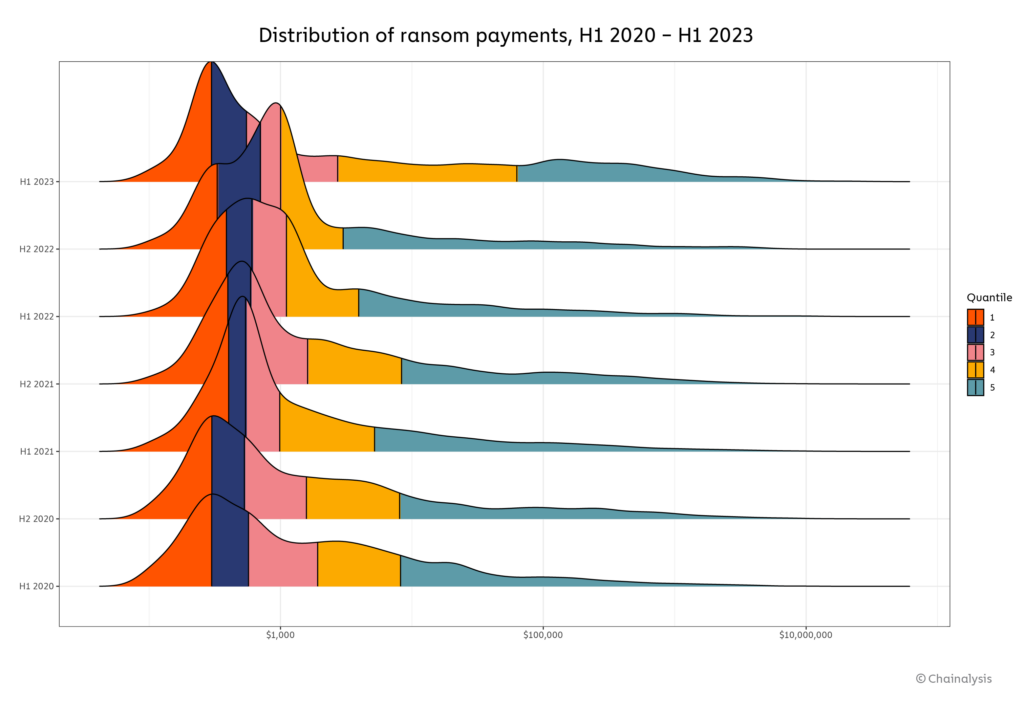
Chainalysis said: “We previously attributed the 2022 decline in average ransom size to improved cybersecurity and data backup practices by large organizations, as well as law enforcement efforts, increased availability of decryptors, and sanctions against services offering cashout services…
“Those developments… enabled many victims to weather ransomware attacks without paying. That still appears to be true to some degree… lots of organizations are still refusing to pay in 2023,” the company said.
See also: Recovering from ransomware: Are your backups enough?
But the combination of operational disruption leading to significant losses, as well as the harassment of employees from (and customers of) victim firms who have not yet paid, appears to have rewarded criminals.
“The ransomware ecosystem has rebounded in 2023 both in terms of payments and attacks, with record-setting incident numbers… an important reminder that ransomware remains a significant threat, and that businesses should continue to shore up their cybersecurity and data backup procedures for added protection” Chainalysis said on July 12.
Ryan McConechy, CTO at MSP Barrier Networks, added: “These figures highlight the profitable machine that ransomware is for criminals today… However, when organisations pay demands, this only fuels the industry…
“Organisations [should] take the average ransomware sum likely to be demanded from them in the event of a compromise – then use that figure as their budget for investing in adequate tooling” he said. (One can hope.)
As Alex Papodopoulous, an IR director at Secureworks, has earlier emphasised in The Stack: To build resilience.. businesses must plan for failure, which means you need good backups but you should also ask:
- Have you taken the time to consider, test and document how you can recover under all the scenarios we’ve just looked at?
- How many systems do you have to potentially recover? What are the complexities? How quickly can you do it?
- Do you have an alternative infrastructure in place, or the means to secure such infrastructure quickly, to keep the business running while you do the full restoration?
- Have you tested and do you have the capability to restore your Active Directory or whatever IAM technology you use?
Among those badly affected this year was outsourcer Capita, which said on May 10 that a ransomware attack will cost it up to £20 million in “specialist professional fees, recovery and remediation costs and investment to reinforce [its] cyber security environment” – that's before any potential legal action by customers and/or regulators over data loss.
