
UPDATED 16:00 BST, July 2, 2021.
Microsoft has acknowledged the existence of the vulnerability circulating known as Printnightmare and confirmed that it is seeing exploitation, three days after a security researcher published a proof-of-concept (POC) that demonstrated exploitation of the 0day, then promptly deleted it -- but not before it had spawned a host of forked and adapted POCs. The bug has been assigned CVE-2021-34527.
Microsoft said: "A remote code execution vulnerability exists when the Windows Print Spooler service improperly performs privileged file operations. An attacker who successfully exploited this vulnerability could run arbitrary code with SYSTEM privileges. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. An attack must involve an authenticated user calling RpcAddPrinterDriverEx()."
The vulnerability affects all versions of Windows.
By abusing this bug, threat actors with any non-admin user and credential (password or NTLM hash) can rapidly gain full access to a domain controller and take over a whole domain, meaning an initial foothold gained through a credentials leak, phishing attack or other technique can rapidly be used move laterally.
One Reddit user posting in the Managed Services Provider (MSP) sub-Reddit said they had already seen it being abused days before the POC dropped noting: "Ran into this at a client already when someone’s vpn account got compromised… Luckily we caught the threat actor when they were spreading and still uploading data to a server of theirs, they’d rate limited their rclome to stay under the radar, we secured that users account right away, cut internet access on all servers minus the required ports to the required hosts on our firewall, cleaned up the malicious dlls before they realized it etc. We didn’t realized this was their vector for spreading until reading about it today, they were still using a rogue workstation our rmm must not have an agent on, but after disabling spooler on all but the print servers it looks like we’re clean server-wise.
Printnightmare mitigation
Run the following as a Domain Admin:
Get-Service -Name Spooler
If the Print Spooler is running or if the service is not set to disabled, select one of the following options to either disable the Print Spooler service, or to Disable inbound remote printing through Group Policy:
Option 1 - Disable the Print Spooler service:
Stop-Service -Name Spooler -Force
Set-Service -Name Spooler -StartupType Disabled
Impact: This will kill your ability to print both locally and remotely.
Option 2 - Disable inbound remote printing through Group Policy
Computer Configuration / Administrative Templates / Printers. Disable the “Allow Print Spooler to accept client connections:” policy to block remote attacks.
Impact:This will block the remote attack vector by preventing inbound remote printing operations. Local printing to a directly attached device will still be possible. For more information see: Use Group Policy settings to control printers.
First Tweeted by Zhiniang "Edward" Peng of Chinese security company Sangfor, then rapidly deleted, the POC was ostensibly for a bug previously also reported by Zhipeng Huo, Piotr Madej and Yunhai Zhang and tracked as CVE-2021-1675. Microsoft's June 8 patch for that CVE has not fixed the bug Peng detailed however. (On June 21, Microsoft upped the bug's classification to remote-code execution.)
Confusion continues to reign over what precisely has happened here and why the POC for a Windows 0day is now circulating for a bug many thought was patched, but the original reporter of CVE-2021-1675, Yunhai Zhang said on Twitter on July 1: "I waste[d] time on miscommunication. I did not verify the patch thoroughly until yesterday. I think the one who post the POC did not known that the patch is incomplete too. It is an confusing case that almost impossible to identify by code review."
Peng meanwhile in the since-deleted (but cached and widely available original post and POC) said: "There are more hidden bombs in Spooler, which is not public known. We will share more RCE and LPE vulnerabilities in Windows Spooler, please stay tuned and wait our Blackhat talks ‘Diving Into Spooler: Discovering LPE and RCE Vulnerabilities in Windows Printer."
Microsoft said on July 2: "This vulnerability is similar but distinct from the vulnerability that is assigned CVE-2021-1675, which addresses a different vulnerability in RpcAddPrinterDriverEx(). The attack vector is different as well. CVE-2021-1675 was addressed by the June 2021 security update."
One of the other original CVE-2021-1675 finders, Zhipeng Huo, said on Twitter that Microsoft's response to the original disclosure had been dire, with MSFT taking over a year to issue a fix that didn't work.
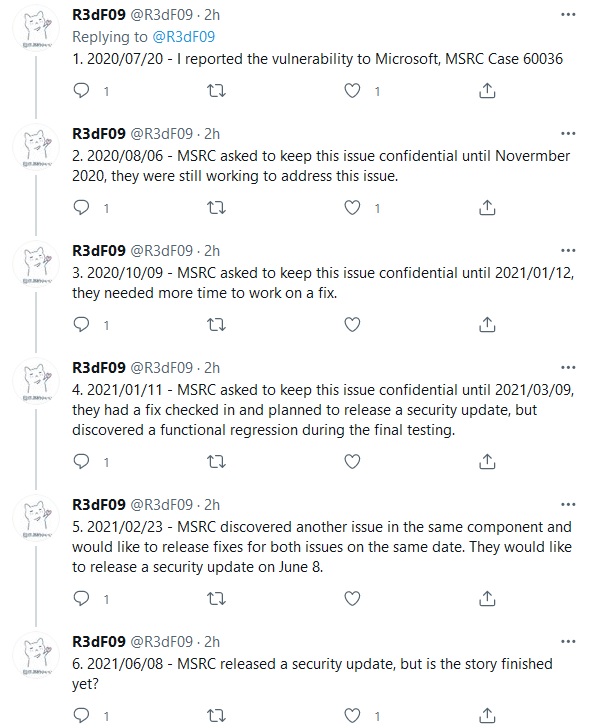
https://twitter.com/R3dF09/status/1410533078112432131
Security researchers at Orange Cyber Defense said: "We managed to exploit this vulnerability on a patched system", adding that it is "necessary to be an authenticated user to elevate privileges and gain Domain Controller's full control." Trusted Security' Dave Kennedy agreed, saying: "The PoC needed modifications but not substantially hard to get working. Will be actively exploited soon. We've tested at TrustedSec and have it working."
As security researcher Kevin Beaumont notes in his own write-up: "The flaw is in RpcAddPrinterDriver, a legit function designed to allow remote printing scenarios and driver installation. The function is designed to allow users with SeLoadDriverPrivilege — by default Administrators and Print Operators — to add drivers to a remote Print Spooler. So, for example, your IT admins to install new printer drivers for users.
A workaround fix can be applied by disabling the printer spooler service. Here's how to do it on both GPO and PowerShell.
A generic way to hunt for Print Spooler exploitation is looking for errosr generated by print spooler due to loading of the payload DLL, says Blue Teamer Andy Gill: "This can be done either through looking for spawning of WerFault.exe by spoolsv.exe or generation of Event ID 7031 showing unexpected termination of print spooler service."
Orange's team added: "Truesec has example published a measure to "limit" the vulnerability. The exploitation of PrintNightmare drops a DLL in a Windows subdirectory. It is possible to restrict the Access Control List (ACL) of this subdirectory, in order to prevent the introduction of such malicious DLLs. Truesec provides a script to perform this restriction. Event logs can detect both successful and non-successful exploit attempts. According to French cybersecurity agency ANSSI, the print spooler service is enabled by default on Active Directory domain controllers. But a known best practice is to disable it. And most AD security auditing tools, such as ORADAD from ANSSI, do try to determine if a DC is indeed configured that way. So this might not be as big an issue in many mature organizations.
Paul Baird, Chief Technical Security Officer UK at Qualys told The Stack: "First of all, releasing the exploit example ahead of MS being able to patch the vulnerability is a train wreck. This is the problem when formal processes for bugs and vulnerability hunting are not being followed. Many organisations struggle to keep up with regular patch management as it is. Having every version and type of Windows - client and server - being affected, this is going to be difficult to rollout at speed when the fix does become available.
He added: "This is a nightmare vulnerability as IT teams can’t just stop the print spooler nor can they wait for the patch to be released. Having a robust monitoring system is the only chance teams have at the moment - they can detect rogue processes spawned from the spooler service - but even that is not an easy task. You have to know the system in the first place and understand if it should or should not have new print drivers, as you can’t just detect a good or bad spawn."
Not everyone agrees things are that dire. One security researcher told us: "The ‘RCE’ looks like it needs access to a file share, so doubtful that it’s exploitable over the Internet. Honestly, doesn’t seem like such a big deal to me…"
