
PowerShell was used in 76% of ransomware incidents in April 2023, according to new data from cybersecurity company BlackFog – a sharp reminder of the extent to which attackers are deploying legitimate tools and platforms to achieve their aims without triggering alarms from many endpoint protection platforms.
PowerShell is a task automation suite from Microsoft made up of a command-line shell, a scripting language, and a configuration management framework. It was originally Windows only, but is now cross-platform and was open-sourced in 2016. PowerShell is built on the .NET Common Language Runtime (CLR).
PowerShell is used in ransomware campaigns in a number of different ways.
In April 2023, for example, incident responders at Palo Alto Networks saw the Vice Society threat group using a custom built and completely automated Microsoft PowerShell script to exfiltrate data from a victim’s network – and although it provided YARA rules to help with detections, noted that “unfortunately, the nature of PowerShell scripting within the Windows environment makes this type of threat difficult to prevent outright…”
PowerShell in ransomware attacks is also used to identify other IP addresses in the victim’s network using the PowerShell Get-NetNeighbor cmdlet and Get-NetworkRange() function and in some campaigns to execute PowerShell on a remote host it uses the Invoke-WmiMethod cmdlet say researchers at VMware, while Red Canary notes that PowerShell’s versatility is “on display in many of the phishing campaigns we see. Adversaries commonly send their victims email messages that include malicious attachments containing embedded code intended to launch a payload. In many cases, this payload executes encoded or obfuscated PowerShell commands that download and execute additional code or a malicious binary from a remote resource…”
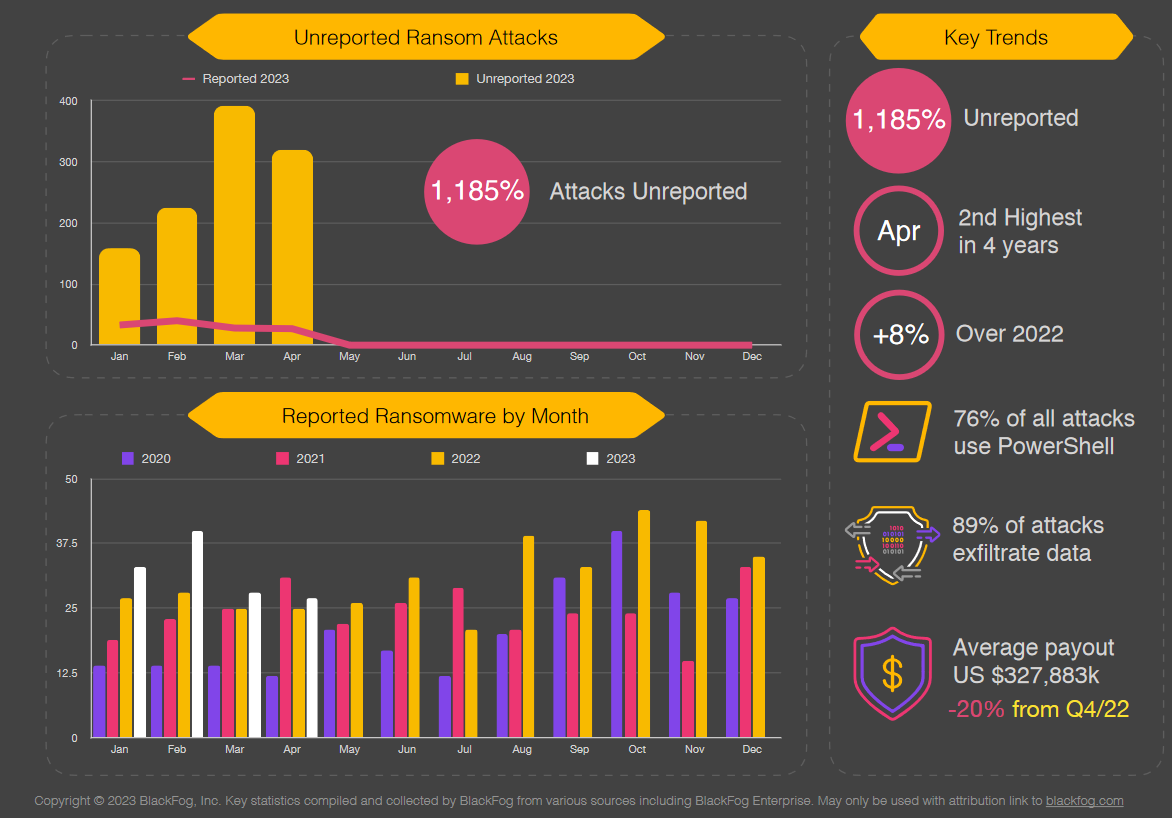
Unreported ransomware attacks...
BlackFog’s April 2023 ransomware report also shows that unreported ransomware attacks now outnumber reported attacks by 10 to 1, with continued growth in attacks on the education, government and healthcare sectors (up 19%, 20% and 24% respectively) and the tech sector seeing the biggest growth of 40% this month.
There were 31 attacks on educational organisations in April, more than one a day, suggesting that they may be low-hanging fruit for attackers – with many operating large fleets of irregularly updated machines and struggling to build a strong security culture. (The Stack noted one university’s lecturers strongly resisting efforts by corporate IT to install (well-known) endpoint protection software on laptops issued by the institution last month, saying it was “spyware” and would impact their academic freedom in a debate on social channels…)
Security company Emsisoft also says it has seen high levels of attacks on educational organisations in 2022.
Last year in the US alone, 89 education sector organizations were impacted by ransomware. Many of them oversee large networks of schools: "In 2022, this almost doubled to 1,981 schools [affected]" it said.
"The most significant incident of the year was the attack on Los Angeles Unified School District which, with more than 1,300 schools and 500,000 students, is the second largest district in the US" Emisoft said this week.
In its monthly ransomware report, Cheyenne, WY-based BlackFog meanwhile said that according to its data, the Lockbit crime group continues to dominate with 20% of reported and 41% of unreported ransomware attacks: “This month we have also seen a high volume of attacks from Bast News” the company added: “Lastly, we see that exfiltration is now involved in 89% of all attacks with more than 41% going to China and 10% to Russia.”
