
The Pentagon has admitted strikingly bluntly that both state hackers and individual malicious actors “often breach the Department’s defensive perimeter and roam freely within our information systems.”
The comments came in the Department of Defense's new “Zero Trust” strategy.
The Department of Defense, which had a 2022 budget of $1.64 trillion, added in the cybersecurity roadmap: “Our adversaries are in our networks, exfiltrating our data, and exploiting the Department’s users.”
Cybersecurity for the Pentagon is rendered challenging by the scale and complexity of its infrastructure.
The Army alone, for example, operates 2,370 on-premises systems and applications; 40,000+ different analytics products; 150 different system interfaces for its 72,000 IT staff – overseeing 1.4 million users – and spends $1.5 billion on IT hardware and early double that for software annually, according to one slide seen by The Stack.
10 key insights into the UK’s bullish new cybersecurity strategy
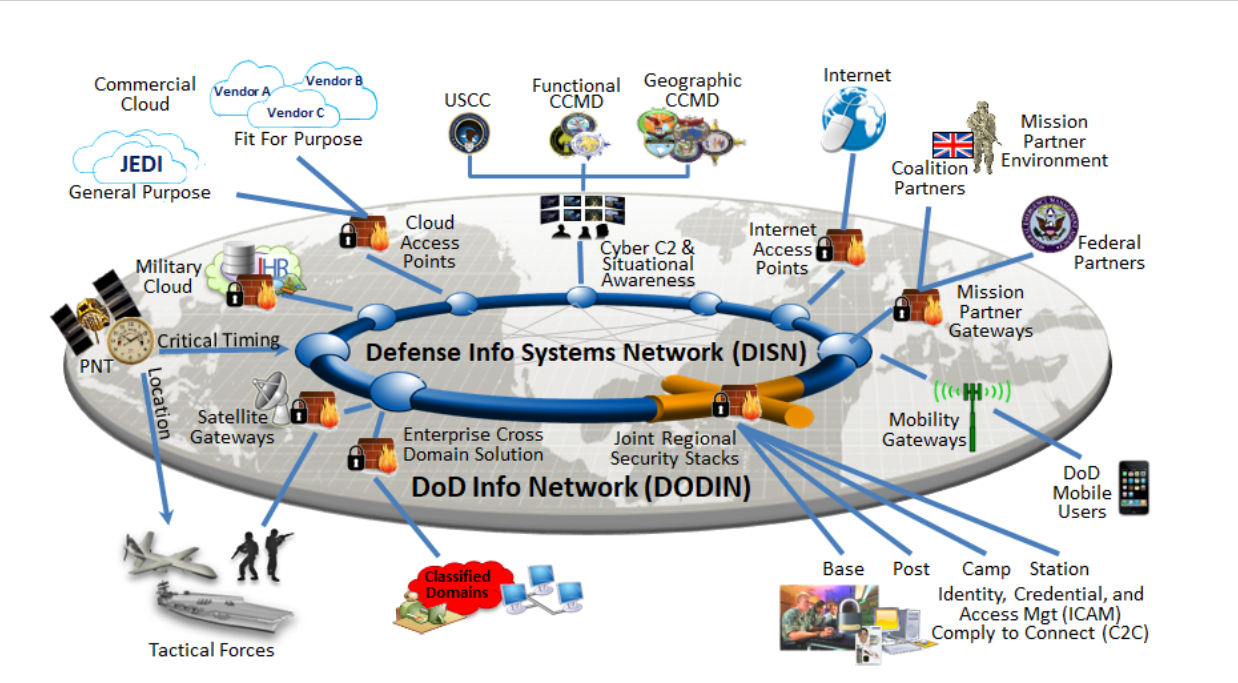
The DoD now admits that a traditional approach of trying to protect this colossal perimeter has failed.
“Previous deployments of application and server stacks have had issues involving implicit trust in communication between systems. This trust has allowed malicious users and devices the ability to traverse through the environment with relative ease. Once through the perimeter controls malicious users and software can move laterally across to infect or attack systems and data within the area of influence,” it notes.
Instead it is trying to shift to a “Zero Trust” model (arguably one of the cybersecurity world’s most overused buzzwords). That involves swapping moat-and-castle network access for conditional user access at the application level and which approaches all traffic — including traffic already inside the perimeter — as hostile.
Most simply, that can involve moving away from firewalls and VPNs to regulate access, to approving sign-on by location, time, device state, etc., with segmentation by application, not network.
The Pentagon is building its Zero Trust approach around seven pillars: user, devices, applications, data, network, visibility, automation, as illustrated in the graphic below (sourced from its strategy.)
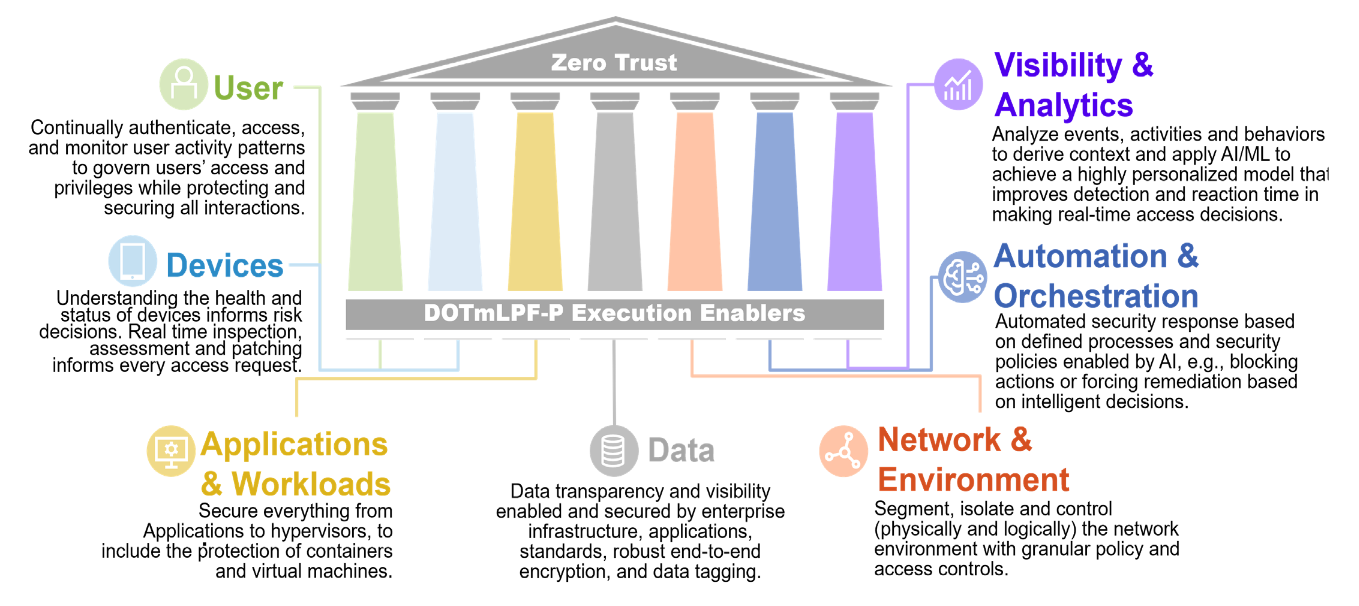
The Pentagon’s now trying to execute this vision. In January 2022 it set up a dedicated Zero Trust Portfolio Management Office within the office of its Chief Information Officer (CIO) to orchestrate efforts.
That work, says the Pentagon, will be led by Randy Resnick, who heads up the DOD CIO’s new Zero Trust office. His focus, he said this week, is to ensure that “through recurring user authentication and authorization, we will thwart and frustrate an adversary from moving through a network and also quickly identify them and mitigate damage and the vulnerability they may have exploited." He has a formidable task ahead.
See also: Azure's CTO touts "S2C2F": CISOs should be paying attention
The Pentagon's Zero Trust reference architecture is here. It includes implementation detail for 45 separate capabilities and 152 total activities, with an outcomes-focused rather than compliance-focused methodology.
