
Palo Alto Networks said it has seen a “claim of a remote code execution vulnerability via the PAN-OS management interface” but does not have details yet; nor has it yet seen evidence of exploitation. The advisory comes after an alleged PAN-OS 0day was advertised in an exploit forum.
“At this time we believe devices whose access to the Management Interface is not secured as per our recommended best practice deployment guidelines are at increased risk” Palo Alto Networks said.
PAN-OS is the software that runs Palo Alto Networks firewalls.

It urged customers to ensure access “is possible only from trusted internal IPs and not from the Internet. The vast majority of firewalls already follow this Palo Alto Networks and industry best practice” it claimed.
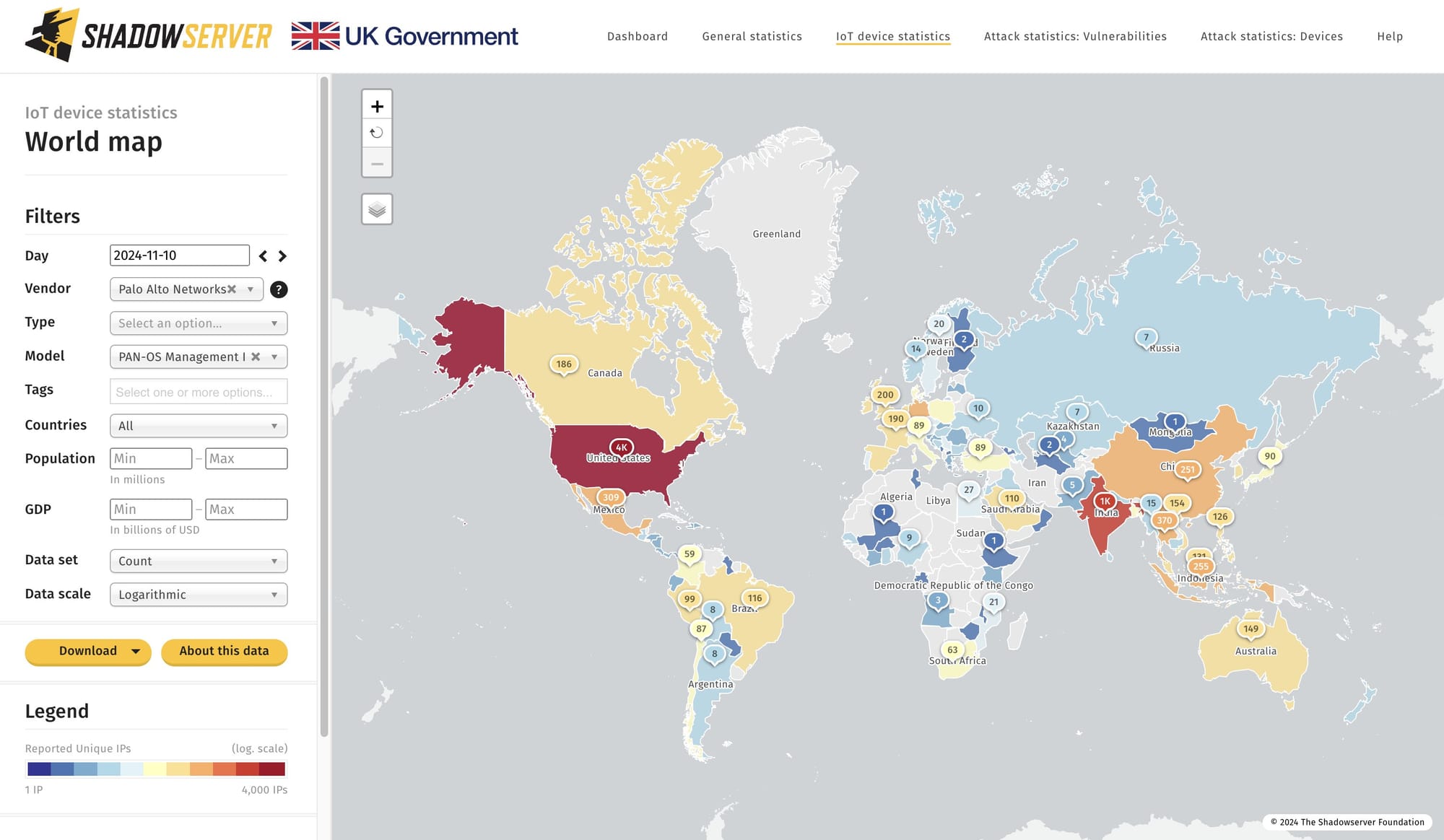
A search by the Shadowserver Foundation however showed some 11,000 PAN-OS management interfaces publicly exposed to the internet. The majority are in the US (4,000) and India (1,000) with 200 in the UK.
The advisory comes six months after a CVSS 10 PAN-OS vulnerability (allocated CVE-2024-3400) was widely exploited in the wild, with botched initial guidance from Palo Alto Networks drawing industry frustration. That bug gave a remote and unauthenticated attacker root privileges.
(Scans around April’s PAN-OS vulnerability attacks showed 40,000 interfaces publicly exposed. If Shadowserver’s scans are correct, some 30,000 customers have improved their default posture since…)
Palo Alto Networks said in its initial advisory: “The list of your devices with an internet-facing management interface discovered in our scans are tagged with PAN-SA-2024-0015” (it has conducted its own internet scanning and said that exposed devices discovered this way in the past few days are listed for customers in their “Remediation Required list.”
(One customer noted on a Reddit thread discussing the advisory that “I just got pinged with this because I set up a new VM firewall, and the default configuration decided to use the only interface configured so far, the public one in Azure. Since there is no option to configure a logical management interface on the VM series, I had to go into the services section and manually change each entry to use the internal interface instead. The default option was straight on the outside interface. Good timing I guess since the firewall had only been on for a few hours so far.”)
The advisory comes a week after CISA warned separately of ongoing exploitation of a Palo Alto Networks Expedition vulnerability tracked as CVE-2024-5910 that was patched in July. Attackers can use it to remotely reset application admin credentials on exposed Expedition servers. (That is a product that is EOL as of January 2025.
Firewalls and other network endpoints are being targeted widely by advanced attackers looking to pivot from these black boxes onto the enterprise networks they are meant to help protect – with significant success helped by the fact that so many are built on ageing code bases.
