Common operational technology (OT) systems from major vendors like Honeywell, Motorola, Schneider Electric and Siemens are riddled with basic security flaws like undocumented hardcoded root credentials, controllers that transmit PINs, usernames and passwords in plaintext, and unsigned firmware images.
That's according to security researchers at Forescout's Vedere Labs -- which today reported over 56 OT vulnerabilities, many of them critical -- across hardware and software that is widely deployed in the oil and gas, chemical, nuclear, power generation, manufacturing, water treatment and mining sectors.

Troublingly, the vast majority of these insecure products -- thousands of which are exposed to the public internet -- are actually certified as secure, including under standards like IEC 62443-4-2 (a security standard for industrial automation and control systems).
"Considering the vulnerabilities discussed in this research are either the result of insecure-by-design or often-trivial failures of security design, these findings point to some serious issues with security standards and certifications for OT" Vedere Labs' researchers noted pointedly, adding that among the causes is a widespread reliance on "functional testing."
In other words, features are verified to be present by many security certification processes, but not checked for robustness. For example, a confirmation that a communication is encrypted will fail to catch that said encryption is broken or weak; or a thumbs-up to user credential configurability will miss that they're transmitted in plaintext.
"In order to avoid standards and certifications from prepping up Potemkin security, products with insecure-by- design features nullifying security mechanisms that are part of the ToE [target of evaluation] ought to be uncertifiable and all parties involved ought to settle on a common understanding of the meaning of being conformant or compliant," Forescout said in a report that may yet prove to be an industry wake-up call.
(The report covers security certification issues in more detail in section 3.6: it deserves a read)
Who's affected by the OT vulnerabilities?
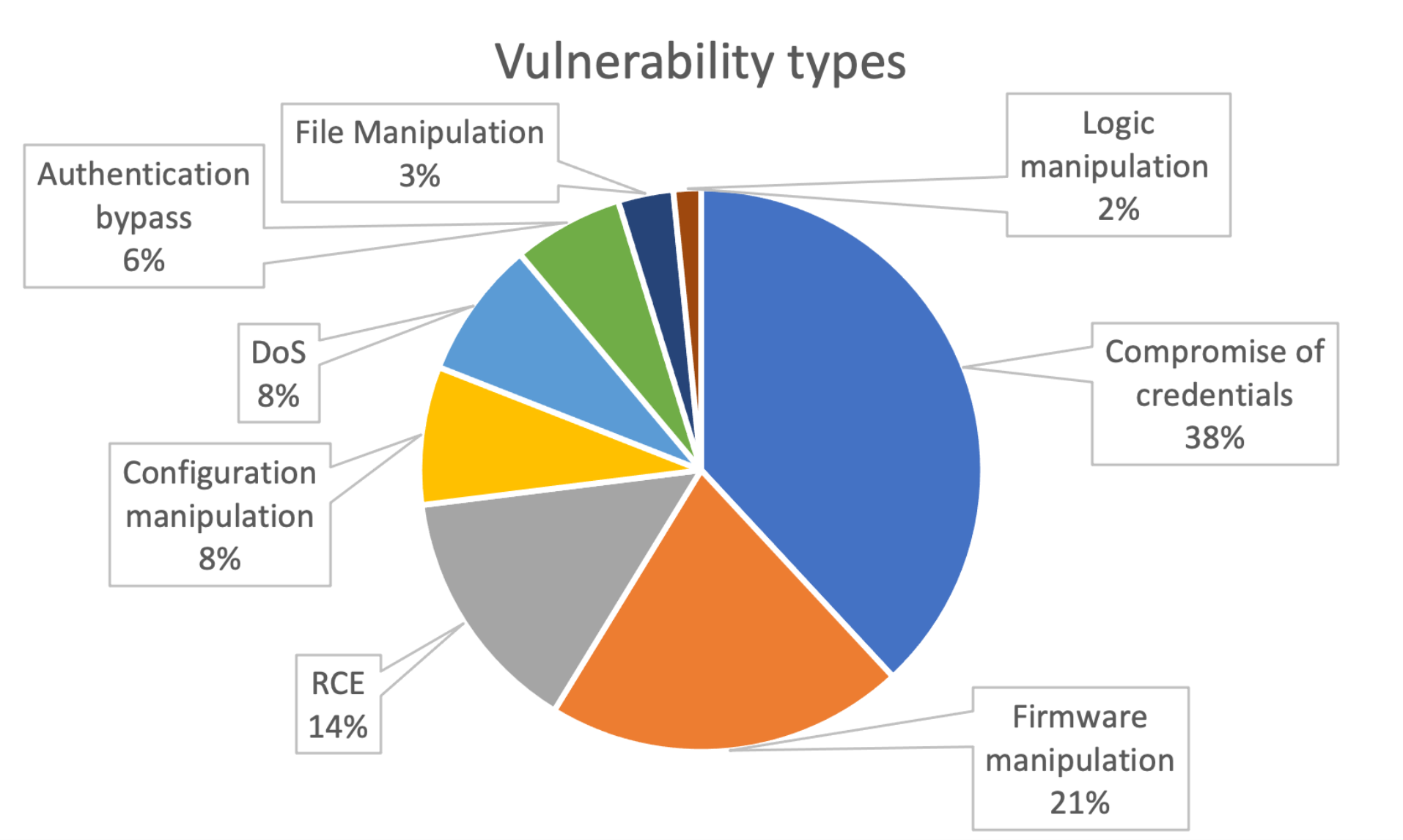
The report, dubbed OT:Icefall, provided information on OT vulnerabilities across 10 different equipment manufacturers: Emerson, Honeywell, Motorola, Omron, Siemens, Yokogawa, Phoenix Contact, JTEKT, Stardom and Schneider Electric. More than a third (38%) of vulnerabilities related to compromise of credentials, with 21% allowing firmware manipulation, and 14% remote code execution (RCE) with CVSS cores as high as 9.8.
Affected devices include supervisory control and data acquisition (SCADA) systems and distributed control systems (DCS). The most affected manufacturer was Emerson, with products including the Ovation DCS for power and water plant control, and the ControlWave process automation controller, among many others.
The report comes as amid (largely futile) pressure* on European policy makers to hold such vendors accountable for upstream security failings under a revised infrastructure security directive, NIS2.
(The 2018 NIS, largely focussed on the cybersecurity of critical infrastructure that is often underpinned by the kind of OT featured in this report, has been criticised for its narrow scope and fragmented implementation; a revised text for NIS2 has been agreed by its co-legislators and is set to be voted on within months.)
See also: An 800-pound gorilla eyes the OT security space
Thousands of affected devices are discoverable through the Shodan search engine – even though these OT systems are not supposed to be accessible via the internet. The most visible devices are from Honeywell subsidiary Saia Burgess, with 2,924 results via Shodan, almost a third of them from Italy, Forescout said.
The report is likely to alarm digital leaders across often budget-constrained major utilities and beyond -- many of whom say in private conversation that security across their sprawling, legacy technology-riddled estates is what "keeps them up at night" -- even as investment tends to focus on fixing leaking pipes, etc.
The threat intelligence team has not yet disclosed four OT vulnerabilities, and seemingly not named one vendor for responsible disclosure reasons. The vulnerabilities – covering plaintext credential transmission, two counts of firmware manipulation, and RCE via memory write – are included in their figures.
The OT security specialist company's researchers also said they had chosen not to reveal full technical details for many of the OT vulnerabilities affecting core functionality of systems, as they are likely to remain unpatched in production environments for “a significant amount of time” -- even urging users to "make use of native hardening capabilities such as physical mode switches on controllers which require physical interaction before dangerous engineering operations can be performed" (no doubt music to the ear of many of this industry's veterans who are often intrinsically sceptical of gauche "connect-everything" digital transformation efforts).
Almost three-quarters of the affected product families have some type of security certification – but most of the issues Vedere Labs found should be possible to discover “relatively quickly” during in-depth vulnerability discovery: “With OT:ICEFALL, we wanted to disclose and provide a quantitative overview of OT insecure-by-design vulnerabilities rather than rely on the periodic bursts of CVEs for a single product or a small set of public real- world incidents that are often brushed off as particular vendor or asset owner being at fault,” said the report.
“These issues range from persistent insecure-by-design practices in security-certified products to subpar attempts to move away from them. The goal is to illustrate how the opaque and proprietary nature of these systems, the suboptimal vulnerability management surrounding them and the often-false sense of security offered by certifications significantly complicate OT risk management efforts.”
The report also suggests there is a shift towards recognising the importance of identifying and dealing with these types of OT vulnerabilities – not least because they are increasingly being targeted by malicious actors. Examples of attacks include Industroyer2, TRITON and INCONTROLLER.
See also: German oil supplier Oiltanking confirms cyber-attack
“Only a few years back, well-known vulnerabilities like some that can be found in OT:ICEFALL would not get assigned a CVE ID because there was the assumption that everyone knew OT protocols were insecure. On the contrary, we believe a CVE is a community-recognized marker that aids in vulnerability visibility and actionability by helping push vendors to fix issues and asset owners to assess risks and apply patches,” said the report.
Vedere Labs also goes through several attack scenarios making use of the disclosed OT vulnerabilities, including access and control of natural gas pipelines, wind turbines and beverage production.
Organisations should, among other practices, work toward consequence reduction by following Cyber-PHA and CCE methodologies Forescout added. Meanwhile: "We renew the call to action for device manufacturers to properly secure OT devices and protocols, for asset owners to actively procure for secure-by-design products and for the wider security community to ensure that security controls are robust rather than merely functional.”
* "One of our biggest concerns is that the NIS Directive doesn’t include hardware and software providers. That is asignificant weakness,” as Jon France, Head of Industry Security for the GSMA put it during consultation in late 2020. “Hardware and software suppliers currently have no legal responsibility regarding the security issues generated by their equipment as part of a network. Yet, these actors are fundamental to ensuring a secure and resilient digital infrastructure within the European Union. Software will play an increasingly important role in our future digitalised society and in telecommunications networks. Hardware and software can contain design or implementation vulnerabilities, which increases the attack surface that adversaries seek to exploit.”







