
A major UK gas distribution network’s “extreme urgency” in contracting an operational technology security vendor for three years without competitive tender was driven by regulatory pressure, it told The Stack.
Wales & West Utilities – one of the UK’s five main gas distribution network providers – has signed a three-year operational technology (OT) discovery contract with Claroty, which was negotiated without a prior call for competition, owing to “extreme urgency brought about by events unforeseeable for the contracting entity.”
The tender was not in response to a security incident, Wales & West Utilities – which operates 35,000km of gas pipes running from North Wales to Cornwall – told The Stack, in response to a series of emailed questions.
See also: Flurry of cybersecurity contracts show CNI focus mounting
“Putting robust operational technology in place to secure and protect the gas network across Wales and the South West of England is a key priority for us. While there has not been a cyber security incident, we have moved at pace in this area, not only to mitigate risk from a rapidly changing threat environment but also to comply with the tight deadlines and requirements of OFGEM and the NCSC Cyber Assessment Framework" the utility said.
A spokesperson added: “After engaging with market-leading suppliers of operational technology asset discovery tooling and undertaking proof of concept exercises, we have selected Claroty as our partner of choice. As a niche area, it is important for us to get the right technology in place as quickly as possible and we are confident that Claroty’s offering aligns strongly with our functional and non-functional requirements.”
Energy regulator OFGEM in December 2022 published updated enforcement guidelines on what it expects from industry under the NIS Directive that guides CNI cybersecurity.
The OFGEM enforcement guidelines aimed to “provide greater clarity, consistency and transparency to our enforcement policies and processes, and to describe the framework we have in place to maximise the impact and efficiency of our enforcement work under the NIS Regulations” the watchdog said.
Unlike more public GDPR breaches and enforcements, OFGEM’s NIS demands do not always see the light of public disclosure. As it notes: “We also place importance on concerns around confidentiality, any potential impact on our ability to investigate and other concerns such as security. Security is likely to be a particularly relevant factor for NIS enforcement work given the issues involved. Before making any public disclosure of NIS enforcement action we will consider national security, alongside any other relevant matters, carefully…”
See Potemkin standards prop up “insecure by design” OT
OT security and visibility remain a huge challenge for utilities, due both to modernisation – increased automation and networked infrastructure – and the opposite: legacy technologies that are hard-to-reach and hard-to-patch. SCADA systems et al meanwhile are increasingly coming into hackers’ crosshairs. For example a Delta Electronics industrial control system (ICS) software package is being actively targeted by threat actors according to the US’s CISA. CVE-2021-38406, affecting Delta’s DOPSoft 2 software, was reported in April 2021.
The recent hack of South Staffs Water by ransomware group also urgently focused minds at the highest levels of government. (While the company claimed its SCADA systems were unaffected, security researcher Kevin Beaumont’s analysis of the Clop data dump suggests, worryingly, that they did access control systems.
Part of the problem is upstream on the OT vendor side, where products from major vendors like Honeywell, Motorola, Schneider Electric and Siemens have been found riddled with basic security flaws like undocumented hardcoded root credentials, controllers that transmit PINs, usernames and passwords in plaintext, and unsigned firmware images according to security researchers at Forescout’s Vedere Labs last summer, when the company reported over 56 OT vulnerabilities, many of them critical — across hardware and software that is widely deployed in the oil and gas, chemical, nuclear, power generation, manufacturing, water treatment and mining sectors.
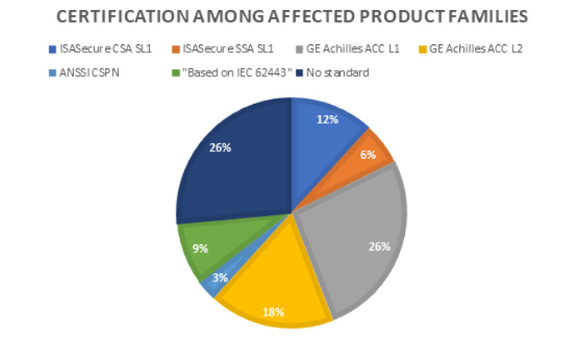
Troublingly, the vast majority of these insecure products (thousands of which are exposed to the public internet) are actually certified as secure, including under standards like IEC 62443-4-2; a security standard for industrial automation and control systems: "In order to avoid standards and certifications from prepping up Potemkin security, products with insecure-by- design features nullifying security mechanisms that are part of the ToE [target of evaluation] ought to be uncertifiable and all parties involved ought to settle on a common understanding of the meaning of being conformant or compliant,” Forescout said at the time; a complaint that did not meet the reception it should have.
