
A critical Oracle Fusion Middleware vulnerability, that sat unpatched for six months after disclosure, exposed companies including Starbucks, BestBuy and Dell to potential pre-auth RCE attacks, said the finders of the Oracle exploit.
The Oracle exploit was found and reported by security researchers "peterjson" and "Jang" in October 2021. But the Oracle middleware vulnerability, which they named “Miracle”, did not receive a patch until April 2022 under Oracle's often-overlooked patch cycle. The two have now posted further details about the vulnerability, allocated CVE-2022–21445 with a critical CVSS score of 9.8 and urged rapid patching.
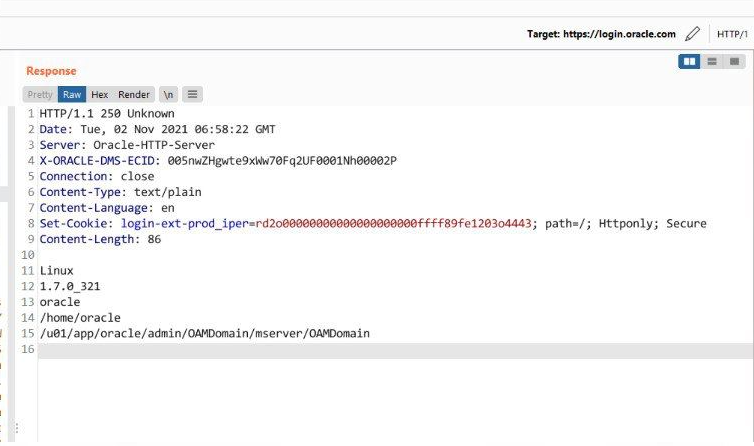
The two, working from Vietnam under the Zero Day Initiative (ZDI) bug bounty programme, said they also popped login.oracle.com "which is play [sic] an important role in oracle’s online services" in a bid to emphasise the severity of the flaw after Oracle took longer than they had expected to patch the vulnerability.
The Miracle exploit is enabled by an ADF Faces vulnerability (CVE-2022–21445), and an Oracle Web Services Manager flaw (CVE-2022–21497, rated 8.1). Both Oracle middleware vulnerability patches are covered by the vendor’s April 2022 critical patch update.
“After [we] disclosed this bug with Oracle, Oracle took almost 6 months to patch this vulnerability in each product inside Oracle Fusion Middleware. We also reported pre-auth RCEs to BestBuy, Starbucks, USAA, NAB Group, Regions Bank, Dell, … via their bug bounty program after the patch was released,” said the researchers’ post.
(Update 25 June 2022: The researchers subsequently removed the names of the affected companies from the post, but the original can be seen via the Wayback Machine.)
Any unauthenticated attacker with network access via HTTP can abuse the vulnerability. Whilst Oracle users are typically less exposed than Microsoft customers -- one of the reasons its often critical vulnerability-rich quarterly patch update gets less attention -- the researchers said in this instance they found scores of blue chips that were vulnerable to attack via the bug, with peterjson confirmed to The Stack that Starbucks and the other companies had publicly-exposed systems.
He declined to give a hard number for total potentially exposed instances but said “we believe it's huge” as the vulnerability in theory affects Oracle online services, Oracle Cloud Infrastructure and on-prem instances. The white hat emphasised that he had only contacted Starbucks and each affected company they found after the Oracle patch was available, and only if that company had so far failed to apply the patch.
See also: Oracle’s “HeatWave” is going multicloud: How hot will things get for MySQL?
Jang and peterjson started researching the Oracle middleware vulnerability issues after working with the ZDI on Oracle Business Intelligence bugs. Their initial find that led to the exploit was a deserialization of untrusted data bug within ADF Faces, a component within Oracle Fusion Middleware for building web interfaces for Java EE applications.
Any product which uses ADF Faces becomes vulnerable to attack, and the researchers were able to use the Oracle exploit to get at least some access to products including Business Intelligence, Enterprise Manager, Identity Management, SOA Suite, WebCentre Portal, Application Testing Suite and Transportation Management.
But for Oracle Access Manager (OAM), they found two ways to achieve pre-auth RCE: “We want to focus on this because OAM plays an important role on each company infrastructure. Also, many Oracle’s online services / cloud services run OAM as SSO service for users" -- detailing the technical attack chain here.
In a separate post on a different but related Oracle middleware vulnerability, Jang listed users of OAM as including Huawei, VMware and Qualcomm. (In that post, published in March, Jang mentions a “mega-0day” which was not fixed – referring to the Oracle middleware vulnerability fixed the following month.)
Follow The Stack on LinkedIn
By combining the ADF Faces deserialization vulnerability with a flaw in the Oracle Web Services Manager, the researchers were able to gain access to Oracle servers. These included edelivery.oracle.com , businessnetwork.oracle.com – as well as login.oracle.com.
“Why we hack some Oracle’s sites? Because we want to demonstrate the impact to Oracle and let them know this vulnerability is super dangerous , it affects Oracle system and Oracle’s customers. That’s why we want Oracle take an action ASAP. But as you can see, 6 months for Oracle to patch it, I don’t know why, but we have to accept it and follow Oracle’s policy,” said peterjson in the blog post.
The reserchers’ blog post contains a very detailed explanation of how they uncovered the Oracle middleware vulnerability, which is worth a read – and given it exists, the time is ripe to patch the Oracle exploit as fast as possible.