
Oracle made a flurry of announcements on day one of its CloudWorld summit in Las Vegas – spanning network security, meaningful improvements to its Heatwave MySQL managed service, new RAG agents, partnerships with fellow cloud providers, defense contractors, and more.
The event has a uniquely different flavour to AWS’s re:Invent, with more of a “buy it” rather than “build it” feel and less of a developer presence.
Oracle has played aggressive cloud-catch-up however, and in breakout sessions attended by The Stack customers spoke largely positively – and without an apparent gun to their heads – of its cloud’s security and ability to handle enterprise-scale, mission-critical workloads.
Security was a firm focus, with the CIA’s CIO and MGM’s CEO among Tuesday’s high-profile, if revelation-free keynote guests.
At a breakout session on “digital deterrence” attended by The Stack (picture men in boxy grey suits backslapping each other in a manly fashion; a DJ playing incongruous Backstreet Boys hits; partner booths showing LEO satellites swarming the globe and precision missiles striking AI-identified targets) Oracle touted its heritage building for air-gapped environments and ability to offer applications at the military “edge”.
(Defence contractor Anduril has baked Oracle’s “Roving Edge” infrastructure into its Menace family of “expeditionary hardware C4 solutions” for example to, quote, give “warfighters real-time understanding, automated decision advantage, dynamic machine tasking, and human-on-the-loop automation” via Oracle Distributed Cloud.)
As the owner of one of the world’s most widely deployed relational databases, case studies from Oracle’s customary stronghold were not hard to find and suggested that Oracle Database remains hard to dislodge.
At a breakout session with the European Central Bank (ECB), for example, a senior database platform team lead, Carsten Tibke, said the central bank’s data “simply does not fit on RDS” (Amazon’s Relational Database Service) as it comes in far above the latter’s 64 TiB instance storage limit.
With “extreme cases” like an ECB project that saw it migrate complex tables with “500k+ partitions and sub-partitions” onto the cloud Oracle was its go-to choice (here, its Autonomous Database or “ADB”) he said.
(The ECB uses AWS as a “general” cloud landing zone, with more specialist workloads running on Azure and OCI, he added. It plans to have all workloads not categorised as “secret” in the cloud in the next 24 months.)
Tibke praised ADB’s security, performance and cost-effectiveness out-of-the box, whilst suggesting support for complex deployments needed improvement. ADB is “not yet designed for DevOps scale-out”; and it currently lacks the ability to craft sophisticated custom security zone policies and IAM “deny” as well as “grant” policies, he said.
Nobody’s perfect.
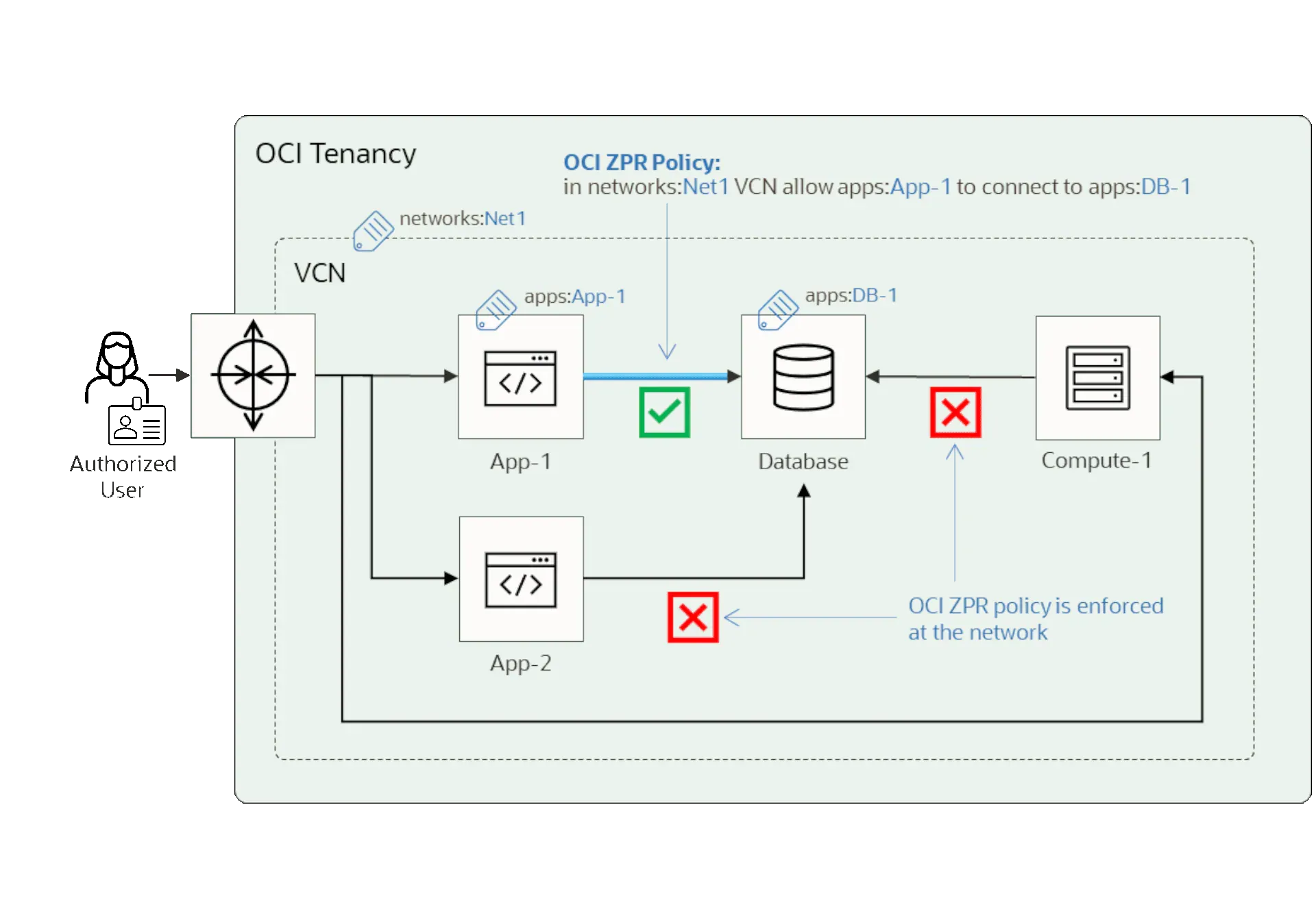
The availability of “Oracle Cloud Infrastructure Zero Trust Packet Routing” (not quite the snappy moniker that it could have been; try ZPR) as built into the “network fabric” of OCI arguably deserved more attention.
This entails the use of a technology and approach that the company Applied Invention is working to get adopted as an international standard. (ZPR can be implemented at the hardware or software levels, Oracle said.)
Oracle described it as enabling “organizations to set security attributes on resources and write natural language policies that limit network traffic based on the resources and data services accessed.” (It had teased the offering in early 2023 and said that it is now generally available.)
In a technical blog, Pradeep Vincent, SVP and Chief Technical Architect, OCI, said it “works with the following features at its core:
- Intent-based security policies: With OCI ZPR, customers define human-readable security policies, called OCI ZPR policies, that capture the intention of how data should flow within their network. These policies are independent of IP addresses or network topology.
- Decoupling security from network configuration: OCI ZPR policies are managed separately from network policies. So, network administrators can change the network configuration without inadvertently changing security positions.
- Enforcement at the network layer: OCI ZPR policies are enforced at the network layer, helping ensure that all traffic complies with the defined security intentions.
- Continuous monitoring: OCI ZPR continuously monitors the system for any changes that might impact security intentions, helping ensure that the security posture remains robust.”
Learn more here.
The Stack's on the ground for another day, albeit mostly in conversation with CIOs and not in breakout sessions. Expect some more write-ups in coming days. As ever, we love to hear from our readers with tips, gripes, or just to shoot the breeze. Pop a DM to Ed Targett on LinkedIn or drop us an email.
See also: CIA CIO La’Naia Jones on AI and the spy agency's tech priorities
