
Microsoft says a native English-speaking cybercriminal group it dubs “Octo Tempest” is using SMS phishing, SIM swapping, and “advanced social engineering techniques” – as well as sometimes blunt threats to life – to breach a growing range of companies across industry verticals.
The threat actor performs research on the organization “mimicking idiolect on phone calls and understanding personal identifiable information to trick technical administrators into performing password resets and resetting multifactor authentication (MFA) methods.”
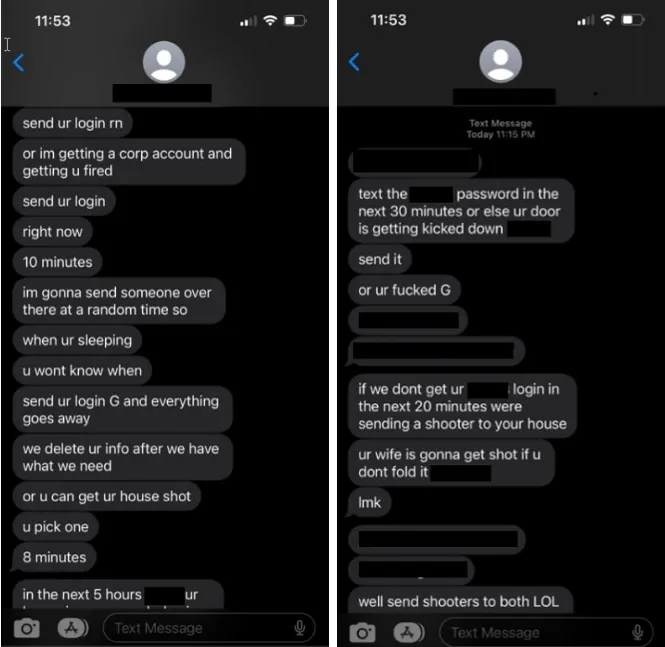
The group showcases “extensive technical depth and multiple hands-on-keyboard operators” but is also not averse to threatening targets where impersonation does not work; Microsoft threat intelligence shared screenshots attributed to one victim in which the group threaten to “send a shooter to your house” and kill his wife. (See below.)
The financially motivated threat group typically steals data and then detonates ransomware in a double-extortion, using some unusual methods for data exfiltration, including data movement platform Azure Data Factory and automated pipelines to extract data to Octo Tempest-hosted SFTP servers, aiming to blend in with typical big data operations.
“The threat actor commonly registers legitimate Microsoft 365 backup solutions such as Veeam, AFI Backup, and CommVault to export the contents of SharePoint document libraries and expedite data exfiltration.”
The group often ultimately detonates ransomware on VMWare ESXi servers – “a unique technique Octo Tempest uses is compromising VMware ESXi infrastructure, installing the open-source Linux backdoor Bedevil, and then launching VMware Python scripts to run arbitrary commands against housed virtual machines” Microsoft said this week.
Follow The Stack on LinkedIn
The threat group earlier been seen using PingCastle and ADRecon to perform reconnaissance of Active Directory; Advanced IP Scanner to probe victim networks; Govmomi Go library to enumerate vCenter APIs; a PureStorage FlashArray PowerShell module to enumerate storage arrays and conducting AAD bulk downloads of user, groups, devices.
After gaining initial access via social engineering, Octo Tempest “leverages publicly available security tools to establish persistence within victim organizations, largely using account manipulation techniques and implants on hosts. For identity-based persistence, Octo Tempest targets federated identity providers using tools like AADInternals to federate existing domains, or spoof legitimate domains by adding and then federating new domains,” said Microsoft this week.
“The threat actor then abuses this federation to generate forged valid security assertion markup language (SAML) tokens for any user of the target tenant with claims that have MFA satisfied, a technique known as Golden SAML. Similar techniques have also been observed using Okta as their source of truth identity provider, leveraging Okta Org2Org functionality to impersonate any desired user account,” it said.
What can I do?
The group’s advanced combination of social engineering, living-off-the land techniques, and diverse toolsets “could make hunting slightly unorthodox” admits Microsoft – saying that the group has expanded beyond tech and telco companies to target natural resources, gaming, hospitality, consumer products, retail, managed service providers, manufacturing, law, technology, and financial services.
In terms of defence, it recommends that for help desk administrators specifically, organisations should “ensure to scope privilege to exclude administrative operations over Global Administrators” (i.e. don't give help desk Global Admin powers, you fool!) and reiterates that requiring MFA “for all privileged roles with the use of authentication strengths to enforce phish-resistant MFA methods such as FIDO2 security keys” and phishing-resistant MFA for administrators should be table-stakes.
