
The European Commission (EC) plans to completely repeal and replace its NIS Directive, saying a new NIS 2 will have broader scope, require better information sharing and demand more robust enforcement -- with the "systemic and structural change" to the cybersecurity legislation set to include strict new rules on incident response, vulnerability disclosure, penetration testing, encryption and more across a sweeping range sectors.
The proposed legislation suggests a significantly more proactive approach by European authorities, with several EU bodies including security agency ENISA empowered to carry out "coordinated security risk assessments of specific critical ICT services, systems or products supply chains, taking into account technical and, where relevant,non-technical risk factors."
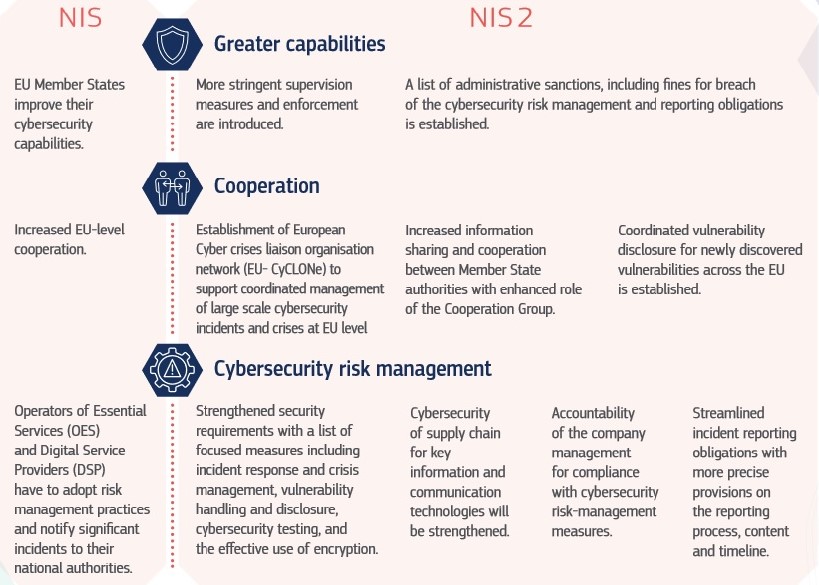
The NIS Directive was the first piece of EU-wide legislation on cybersecurity. Adopted in 2016 (it came into force in the UK in 2018) it required that member states have an national incident response team, a cybersecurity strategy, and a "competent authority" to identity "Operators of Essential Services" (OES) -- which should take "appropriate and proportionate security measures". It was not prescriptive about these measures or the OES impacted. Member states took it with a mixed degree of seriousness.
NIS 2: What you need to know
Under the initial NIS, which came into force in the UK in 2018, those covered by the legislation had to adopt risk management practices and notify national authorities about "significant incidents". The replacement legislation will mandate a much more robust package of requirements spanning incident response and crisis management, vulnerability handling and disclosure, cybersecurity testing, and effective use of encryption. (It is too early to say if the UK will mirror them in local legislation).
NIS 2 will cover banking; chemicals; digital infrastructure (from cloud providers to DNS service providers, co-location data centre providers and beyond), drinking water; energy; financial market infrastructure; food production, processing and distribution; health; manufacturing; postal services; public administration and space; transport; and waste water.
Read this: Fresh warning to businesses over rising “Egregor” ransomware threat.
Adam Brady, Director, Systems Engineering, EMEA at Illumio noted to The Stack: "The updated guidance is part of a trifecta of existing and upcoming cybersecurity directives that has been brought forward due to the impact of COVID-19. NIS2.0 (or the new NIS-replacing mandate) is one part of the updated guidance, covering the security of critical infrastructure, and is joined by a specific piece on telecoms and communications (Directive (EU) 2018/1972 establishing the European Electronic Communications Code), and a third update concerning Financial systems with a regulation on digital operational reliance for the financial sector (COM (2020) 595 final)). There are also related updates on physical security."
He added: "From a technology perspective, this pragmatic approach is welcome... The stress-testing of systems and infrastructure that the accelerated digital transformation and service-lead changes to the industry show that widespread improvements are necessary."
A key focus of NIS 2 is member state communication. Under the legislation a new European Cyber Crises Liaison Organisation Network ("EU - CyCLONe") is being set up to "support the coordinated management of large-scale cybersecurity incidents and crises at operational level", for example; a new network of CSIRTs is also being established. It will also see (within 18 months) the establishment of a peer-review system for assessing the effectiveness of member states’ cybersecurity policies.
Industry experts have largely welcomed the updates. Chris Strand, Chief Compliance Officer at IntSights told The Stack: "This is a needed addition as with the growth of cybersecurity-related data protection laws, escalating targeted attacks, and an ever-growing threat surface, risk-based security analysis and prioritisation has become a critical component of how cybersecurity controls need to be applied for entities regardless of size."

NIS 2: What are the precise requirements?
Under Article 18, meanwhile, entities covered by the legislation will need to take "appropriate and proportionate technical and organisational measures to manage the risks posed to the security of network and information systems which those entities use in the provision of their services". This will span risk analysis and ICT security policies; incident handling and continuity plans; supply chain security "including security-related aspects concerning the relationships between each entity and its suppliers or service providers such as providers of data storage and processing services or managed security services"; vulnerability handling and disclosure; testing and auditing; use of encryption.
Precisely what are the requirements? Hold that thought, the Commission says, noting it "may adopt implementing acts in order to lay down the technical and the methodological specifications of the elements referred to in paragraph 2 [the above]... and follow, to the greatest extent possible, international and European standards, as well as relevant technical specifications." In short, there's no clear-cut requirements yet.
And as Scott Nicholson, director of cybersecurity consultancy, Bridewell Consulting notes to The Stack: "On the whole, the proposed changes for both the NIS Directive and UK NIS Regulations appear positive, however the challenge will be how that moves from legislative changes, through to practical implementation across each industry, all of which are at varying stages of maturity", He adds: "Whilst Brexit may add a spanner into the mix, I still believe the UK will align to a European approach.”
NIS2 and the UK, post-Brexit.
The NIS is set out in UK law and continues to apply after Brexit. Whether the UK will mirror NIS2 is an open question. As Mark Nicholls, Chief Technology Officer at Redscan, the UK based ethical hacking and threat detection business tells the Stack: "In the UK, the National Cyber Security Centre has a framework to help providers of critical national infrastructure and services achieve NIS compliance, but this is based on its own interpretation of the Directive’s 14 key principals.
"The NCSC has no role in enforcing NIS and its recommendations aren’t necessarily in line with those published by other countries. Also, now that the UK has left the European Union, it remains to be seen whether the government will update its requirements under the NIS Regulations, or whether there will be future divergence.
“Given the inconsistencies in approach, it’s quite right that the European Commission is taking time to consider and propose improvements to the next iteration of the directive.
Altaz Valani, Research Directorat Security Compass added: "If different systems do not conform to a defined reference architecture, that will make integration difficult and lead to challenges with rapid reporting and resolution. In the spirit of openness, it would be helpful to also see the emergence of a common reference architecture and integration maps with existing knowledge bases.
