
Two new cybersecurity tools “OSV-Scanner” and “Peach” that landed this week deserve attention – whether you are a CISO, Blue Team, or just trying to tighten up your application development or cloud practices.
OSV-Scanner was released under an Apache 2.0 licence by Google. Peach is an open framework from Wiz to model the threat of unauthorised cross-tenant access to cloud workloads during your threat modelling process.
What is OSV-Scanner?
OSV-Scanner, a free tool from Google, matches your code and dependencies against lists of known vulnerabilities in a rapidly growing open source vulnerability database, in OSV.dev, that launched in 2021.
Google says: “Running OSV-Scanner on your project will first find all the transitive dependencies that are being used by analyzing manifests, SBOMs, and commit hashes. The scanner then connects this information with the OSV database and displays the vulnerabilities relevant to your project” for more secure development.
(A good example of the challenges here: 12 months after the Log4J vulnerability triggered massive attacks, nearly 40% of downloads of the open source java logging library are still the vulnerable version. As Sonatype notes, 96% of vulnerable downloads of open source components actually have a fixed version available.)
See also: 7 free cybersecurity tools CISOs should track
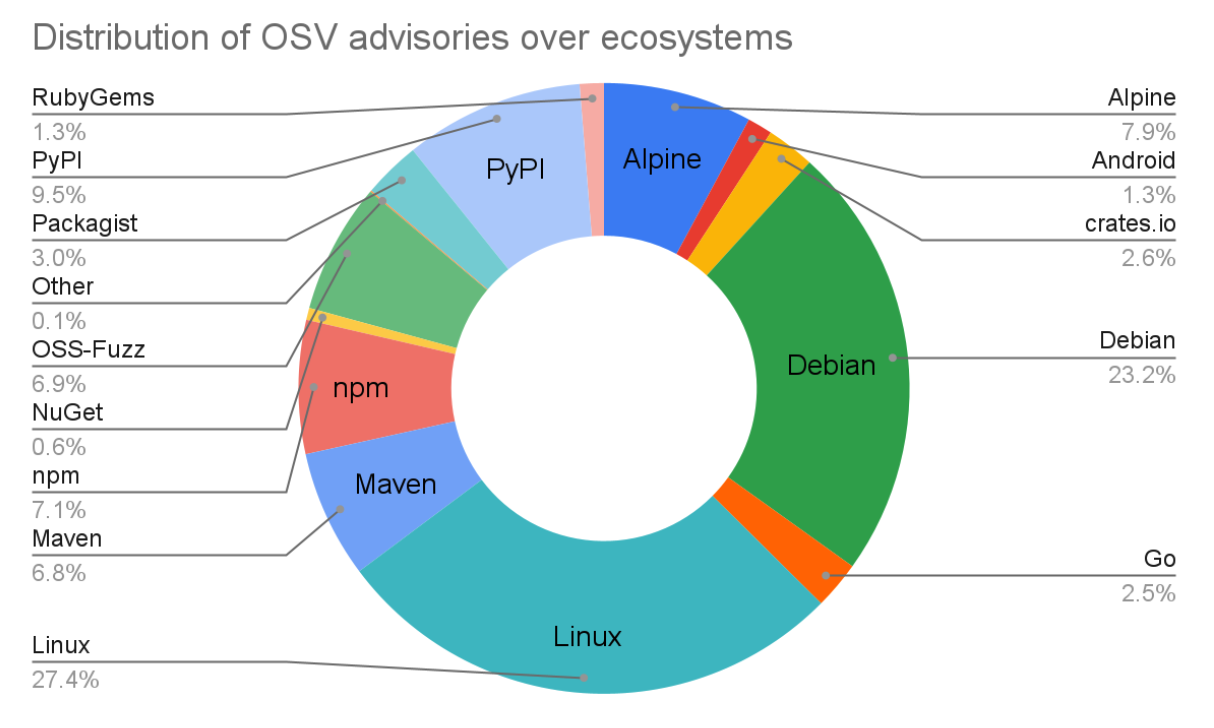
OSV.dev now supports 16 ecosystems, including all major language ecosystems, Linux distributions (Debian and Alpine at this stage), as well as Android, Linux Kernel, and OSS-Fuzz. It is now the biggest open source vulnerability database of its kind, with over 38,000 advisories, up from 15,000 advisories a year ago.
The scanner is not perfect and still being built out but it is undeniably useful, it is free and allied to a free framework like Microsoft’s S2C2F it is another welcome tool in the arsenal of tightening up OSS security.
OSV-Scanner can be found here.
Wiz's Peach framework
The Peach framework was released this week by cloud security company Wiz.
It has been designed to encourage and facilitate the inclusion of an isolation review process for cloud workloads, as part of a broader threat modelling effort for a multi-tenant applications.
Its whitepaper is free to download – mercifully without any data-harvesting forms to fill in either.
Wiz launched Peach after discovering and encountering numerous critical cross design and implementation mistakes that enabled unauthorised cross-tenant access into hyperscaler cloud accounts.
See also: MSFT belatedly hardens Azure as “SynLapse” exploit details released
Peach refers to the hardening of Privilege, Encryption, Authentication and Connectivity, and proper Hygiene.
It was born out of the experience by Wiz’s security researchers that identified “a common root cause in all these cases in the form of bugs in customer-facing interfaces (such as an insecure API permitting tenants to execute code in unexpected ways or escalate their local privileges within their own environment), compounded by insufficient hardening of security boundaries (such as a virtual machine with an overly permissive firewall).
Whilst it is aimed more at cloud providers than cloud customers, to those mindful of cloud security it deserves a close read and comes with the suggestion that those mindful of imperfect trust boundaries should consider using third-party encryption bringing your own trust boundary to place between you and other tenants).
Together with tools like Bloodhound, Infection Monkey, OpenVAS, OpenCTI, the two releases are a reminder that there is a wealth of free and open source resources and guidance available for security professionals and it keeps growing. Such tools are, of course, only as good as those wielding them carefully...
