Five Cisco wireless products are vulnerable to a CVSS 10 critical vulnerability that lets -- in Cisco's own language -- an "unauthenticated, remote attacker bypass authentication controls and log in to the device through the management interface" in the latest example of a severe authentication failure in Cisco products.
Among the tools affected by the critical Cisco vulnerability is its Virtual Wireless Controller (vWLC). This provides wireless configuration and management functions to network managers for up to 32,000 clients.

Allocated CVE-2022-20695, the vulnerability also affects three hardware products: the 3504, 5520 and 8540 wireless controllers.
While all three have been transitioned to "end of sale" status, they are still in wide deployment: two were on the market until end-January 2022; the other (the 3504) until end-January 2021.
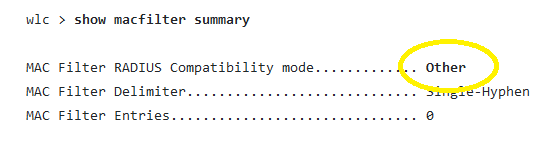
Cisco's "Mobility Express" and vWLC are also vulnerable to the security flaw, if they are running Cisco WLC Software Release 8.10.151.0 or Release 8.10.162.0 and have macfilter radius compatibility configured as Other. (Users can check if that's the case, per Cisco instructions, by deploying the CLI command below).
Cisco attributed the find to French Wi-Fi specialist Bispok and said it has not been seen actively exploited (although it is fairly unlikely that anyone would know at this stage.)
C'mon Cisco, sort it out
Cisco has what we will generously describe as a shitty track record of authentication failures in its products, for example all too regularly issuing security updates to remove hard-coded credentials.
(Hard examples? Check CVE-2019-15977, a vulnerability in the web-based management interface of Cisco DCNM that could allow an unauthenticated, remote attacker to bypass authentication, for example; or CVE-2019-15975, a vulnerability in the REST API endpoint, again, because a “static encryption key is shared between installations"; or CVE-2021-1577, another pre-auth RCE blamed on "improper access control"; or CVE-2021-1497 another pre-auth RCE bug that gives root access to Cisco software used for enterprise-grade data management; or CVEs 2021-1289, 2021-1290, -2021-1291, -2021-1292, -2021-1293, -2021-1294, E-2021-1295 -- yes, more pre-authentication RCEs in VPN routers this time, owing to inproper HTTP request validation.)
It is no doubt hard to produce secure software and other vendors are guilty of shipping products with regular critical vulnerabilities. Two security researchers -- when discussing another earlier set of pre-auth vulnerabilities in Cisco products with The Stack in 2019 -- however described Cisco's run of pre-auth RCEs as the result of "in the most flattering terms... extreme laziness and negligence from a software development and QA point of view [that] could also be viewed with suspicion as it resembles what some might call a ‘backdoor’.
The company told us in 2021 that it is working to "try to reduce the number of vulnerabilities and continuously enhance our products. Unfortunately, despite the best efforts of technology vendors, security vulnerabilities do still occur. We are actively developing new tools and techniques to identify and resolve these issues before they reach our customers, including the use of the Cisco Secure Development Lifecycle.”








