Iran has described a damaging blackout at its underground Natanz nuclear site as an act of "nuclear terrorism", as Israeli media suggested a cyberattack orchestrated by the country caused the incident -- conjuring up shades of 2010's Stuxnet attack. (Unnamed intelligence officials in the US and Israel suggested to the New York Times however that the attack was explosives-based, rather than the result of a cyberattack).
However the apparent sabotage operation was conducted, the incident has once again renewed a focus on nation state cyber activities, amid what HP's Global Head of Security for Personal Systems Ian Pratt describes -- in a report that points to a rate of 10+ publicly attributed nation state cyberattacks a month in 2020 -- as a "a steady upwards trajectory in the severity, openness and variety of Nation State cyber activities."
"Proliferations in cyber-based Nation State struggle mean we may be closer to ‘advanced cyberconflict’ (ACC) than at any point since the inception of the internet," writes Dr Michael McGuire, a senior lecturer in criminology at the University of Surrey, and the lead author of the March 9 report.
"Whether it is the frequency of cyberattacks, the phenomenon of hybridisation (i.e. the growing fusion between cyber and physical/kinetic confrontations), or the role of pre-existing regional conflicts in exacerbating and promoting cyberconflict, the writing on the wall is increasingly hard to ignore", McGuire notes.
(The report comes weeks after the UK's March 16, 2021 "Integrated Review" of defence promised "much more integrated, creative and routine use of the UK’s full spectrum of levers – including the National Cyber Force’s offensive cyber tools – to detect, disrupt and deter our adversaries.”)
Follow The Stack on LinkedIn
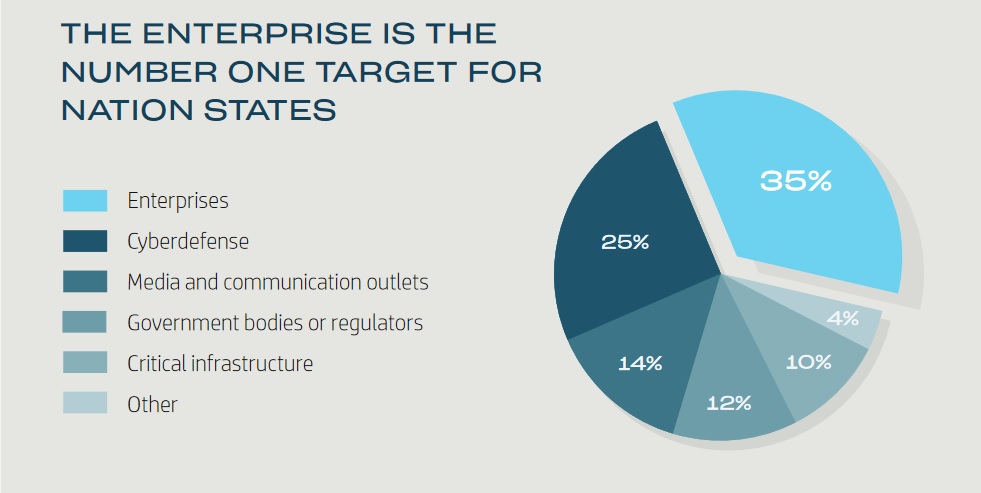
Yet as McGuire's research documents, despite high-profile inter-state incidents, it is enterprises that are the primary target of most nation state activity: whether as a tool to gain further access down their supply chain, or as targets for their IP and other commercial intelligence. (With the boundaries between nation state APTs and advanced cybercriminals increasingly blurred, needless to say, attribution remains a challenging area.
As the report has suggested, the practice of war and the pursuit of crime have become inextricably interwoven in the contemporary world and cyberweaponry has been central to this blurring of boundaries.
Among the precautions enterprises should be taking are not just cybersecurity ones, but physical security ones. Speaking to The Stack's founder last year, one senior cyber crime police officer noted that criminal gangs are planting “sleepers” in cleaning companies so that they can physically access IT infrastructure -- pointing to a “much larger increase in physical breaches”.









