The impregnability of Apple's walled garden is one of the most enduring myths of the digital age.
Now a researcher from Cisco Talos has shown us that even the strongest defences can be compromised after allegedly finding a series of vulnerabilities in Microsoft software for Apple's MacOS.
Francesco Benvenuto claimed to have discovered eight bugs in Microsoft applications for the operating system, including Word, Teams, Excel, OneNote and Outlook.
"The implications are that an untrusted application could steal entitlements and permissions of an application on macOS that is considered trusted," he told The Stack. "Thus potentially bypassing the extra security to access certain resources."
In his research, Benvenuto claimed adversaries could exploit vulnerabilities by injecting malicious libraries into Microsoft's applications.
"Permissions regulate whether an app can access resources such as the microphone, camera, folders, screen recording, user input and more," he said. "So if an adversary were to gain access to these, they could potentially leak sensitive information or, in the worst case, escalate privileges."
None of the eight CVEs identified (which you can find here) have been rated as critical.
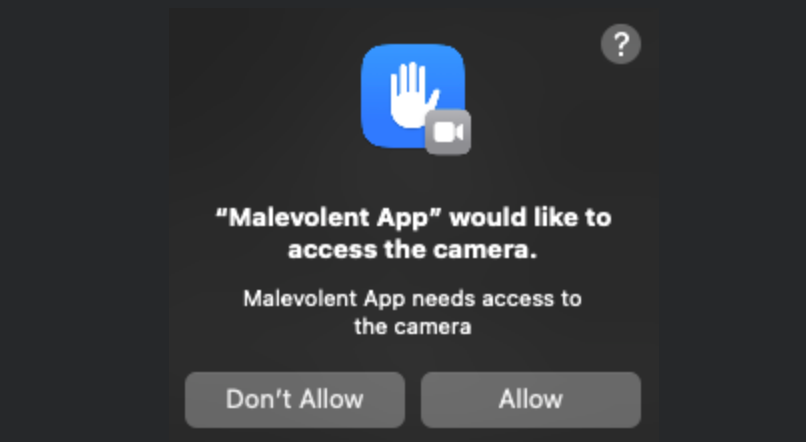
The image above illustrates Apple's permission-based security model, which is focused on a Transparency, Consent, and Control (TCC) framework.
Essentially, users are asked for explicit consent before applications can access protected resources such as contacts, calendars, photos and location, or hardware such as cameras and microphones.
When an application with specific entitlements initially asks for the use of a specific capability, a permission pop-up appears. After users make a decision, their choice is stored in a TCC database and remembered whenever that app requests access in the future.
MacOS includes measures to guard against code injection, including the sandboxing that is required to list on the App Store, which restricts access to data and resources. Apps can also be required to enable hardened runtime to resist exploitation.
Hardened runtime enables "library validation" by default, which restricts the loading of libraries to those that have been signed by the application's developer or Apple.
"Even though hardened runtime guards against library injection attacks and the sandbox secures user data and system resources, a malware might still find ways to exploit certain applications under specific conditions," Benvenuto wrote.
"If successful, this would allow the attacker to assume the application's entitlements and permissions."
The Cisco Talos researcher claimed that the security protection provided by the hardened runtime is disabled in some Microsoft Office apps, which could potentially "permit the loading of unsigned dynamic libraries".
A "library injection" attack could enable an attacker to "access restricted resources without any further user interaction", he alleged.
Teams is "similar to Microsoft Office apps in its vulnerability to library injection", Benvenuto claimed.
"The vulnerable apps leave the door open for adversaries to exploit all of the apps' entitlements and, without any user prompts, reuse all the permissions already granted to the app, effectively serving as a permission broker for the attacker," he continued.
Microsoft has now addressed four of the eight bugs, issuing fixes to Teams and OneNote, Cisco Talos said.
Apple specialist Michael Covington, VP of Strategy at Jamf, told The Stack that Apple's layered security model for macOS protects both user privacy and device integrity "very well to prevent mainstream attacks from being effective on a device running up-to-date software" through a combination of automated checks, app entitlements, and user-controlled permissions.
"However, security solutions are complex and a failure within one component can cause the entire model to break," he said. "Ultimately, the ‘defence in depth’ approach used by macOS requires trust in the applications to self-police the permissions they are granted. This is important in scenarios where applications which are granted elevated permissions can be hijacked, potentially allowing these apps to inadvertently provide unauthorised access to sensitive resources.
"In the case of the recent findings, Microsoft’s apps were [alleged] to disable checks on third-party libraries being loaded. This is a noteworthy flaw in apps that naturally require permissions to Apple’s controlled resources, like the camera or microphone, because users are inclined to grant such permissions to collaboration tools like Microsoft Teams or logging tools like OneNote. Fortunately, Microsoft agreed to update these applications.
"It is worth noting that some apps, such as Microsoft Word, Excel, Outlook, and PowerPoint, will not receive the fix. The reality is that vigilant users are unlikely to grant sensitive permissions to these productivity tools, so the risk is low. The question remains, however, why the lower risk is worth the confusion this causes users.”
We have written to Microsoft for comment.







