Windows 10 and 11 users have been urged to urgently apply a new Microsoft update after security researchers discovered a new exploit that targets Windows "relics" in the wild.
CVE-2024-38112, discovered by Zero Day Initiative (ZDI) researchers, has been exploited by the cybercrime group Void Banshee as part of its information-stealing campaign.
The exploit targets the remains of the disabled Internet Explorer (IE) browser as an attack vector. While IE had been disabled in later versions of Windows 10, including all versions of Windows 11, it was not removed from the system.
"This zero-day attack is a prime example of how unsupported Windows relics are an overlooked attack surface that can still be exploited by threat actors to infect unsuspecting users with ransomware, backdoors, or as a conduit for other kinds of malware," Trend Micro wrote.
By exploiting the vulnerability, Void Banshee executed malicious code by abusing the MHTML protocol handler and x-usc directives through (URL) files. Then, Void Banshee was able to access and run files directly through the disabled Internet Explorer instance on Windows machines.
This effectively brings the internet browser back to life as a malicious zombie before executing the final payload of the attack, which infects users and organisations with Atlantida malware. The "stealer" malware is designed to extract sensitive information from systems and applications installed on them.
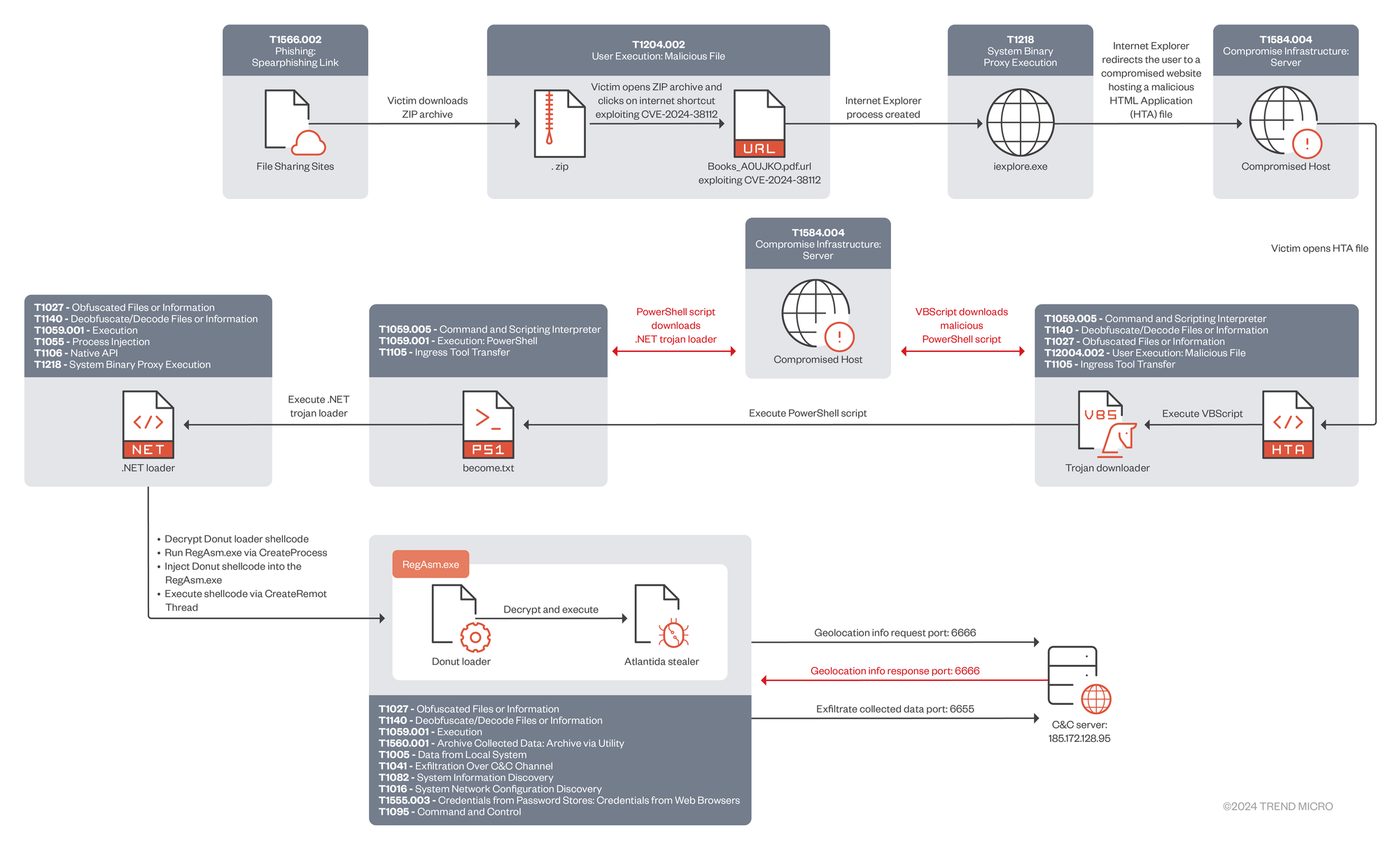
According to the ZDI researchers, variations of the Atlantida campaign have been highly active throughout 2024 and have evolved to use CVE-2024-38112 as part of Void Banshee infection chains. Since, the exploit has been added to CISA's catalogue of known vulnerabilities as well.
Void Banshee has reportedly targeted systems in North American, European, and Southeast Asian regions for information theft and financial gain.
"Since services such as IE have a large attack surface and no longer receive patches, it represents a serious security concern to Windows users," the ZDI security researchers wrote.
"Furthermore, the ability of threat actors to access unsupported and disabled system services to circumvent modern web sandboxes such as IE mode for Microsoft Edge highlights a significant industry concern," the report added.
A full list of indicators of compromise can be found here.






