
Multiple threat actors ranging from financially motivated cybercriminals to state-sponsored groups have exploited a critical vulnerability in Microsoft Exchange servers, Redmond said this week -- with the smorgasbord of exposed enterprise servers proving such a compelling target that more advanced attackers have acted to remove rival black hats from the systems, and used multiple persistence points to maintain access to a network.
"Attackers were observed cleaning up .aspx and .bat files to remove other attackers, and even rebuilding the WMI database by deleting .mof files and restarting the service. As the window on unpatched machines closes, attackers showed increased interest in maintaining the access to systems they exploited", Microsoft said.
"By utilizing 'malwareless' persistence mechanisms like enabling RDP, installing Shadow IT tools, and adding new local administrator accounts, the attackers are hoping to evade incident response efforts that might focus exclusively on web shells, AV scans, and patching," noted Microsoft 365 Defender Threat Intelligence.
The comments came in a March 25 2021 blog, which noted that many compromised systems "have not yet received a secondary action, such as human-operated ransomware attacks or data exfiltration, indicating attackers could be establishing and keeping their access for potential later actions... using credentials and data stolen during these attacks to compromise networks through other entry vectors." Patching is not enough.
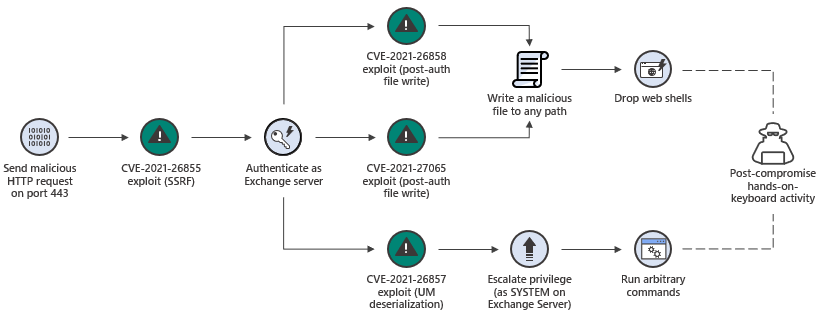
For those napping on the widespread global abuse of a series of chained vulnerabilities in Microsoft's on-premises email server, first reported in early March, the company was referring to post-exploit abuse enabled initially by CVE-2021-26855: a server-side request forgery (SSRF) vulnerability in Exchange; CVE-2021-26857 , a vuln in the Unified Messaging service (exploitation by the threat group gives attackers the ability to run code as SYSTEM); CVE-2021-26858 and CVE-2021-27065, post-authentication arbitrary file write vulnerabilities.
See also: UK pledges to make more “creative and routine” use of offensive cyber tools.
Organisations ranging from defence contractors to the European Banking Authority were compromised in early campaigns by Microsoft Exchange attackers believed to have Chinese state backing and dubbed HAFNIUM, with entire inboxes reported exfiltrated. After the bugs were patched by Microsoft and the vulnerability became known, others piled in. As Microsoft noted: "Attackers are known to rapidly work to reverse engineer patches and develop exploits. In the case of an RCE vulnerability, the rewards are high for attackers who can gain access before an organization patches, as patching a system does not necessarily remove the access of the attacker.
Various strains of ransomware, webshells, and other malware have been spotted on compromised systems, Microsoft said. Quelle surprise, cryptocurrency miners were some of the first payloads seen dropped by Microsoft Exchange attackers from the post-exploit web shells. Most also used access to perform extensive reconnaissance using built-in Exchange commandlets and dsquery to exfiltrate information.
For highly-security conscious organisations already reluctant to run communications systems via the cloud rather than on-premises, the incident has proved a serious wake-up call. Conversations had by The Stack with many IT leaders in the wake of abuse by Microsoft Exchange attackers suggest that many enterprises and public sector organisations are actively and more aggressively exploring alternatives to email outright. Stay tuned for a feature on one alternative that users may not have considered at all -- coming late next week.
