
When Microsoft locks the doors of a secretive security summit tomorrow, one topic is expected to loom large on the agenda.
The official goal of the Windows Endpoint Security Ecosystem Summit at Microsoft’s HQ in Redmond, Washington, is to set out “concrete steps” to improve security and resiliency in the wake of the Crowdstrike global mega-outage.
Microsoft has summoned Crowdstrike, chosen partners, government representatives and endpoint security vendors for “discussions about improving resiliency and protecting mutual customers’ critical infrastructure”.
Government officials will be on hand to “ensure the highest level of transparency” and Microsoft has promised to set out “next steps in both short and long-term actions and initiatives”.
There will be no journalists at the event, with “updates” issued afterwards to let us know what was agreed (or possibly what orders Microsoft has issued).
But even though we don't know for sure what will be talked about at the summit, it seems almost certain that something is going to change around access of the kernel.
Kernel access and blue screens of death
Apple kicked developers out of the MacOS operating system several years ago. Flash forward to today and kernel access is once again on the agenda after the Crowdstrike outage caused 8.5 million computers to suffer the blue screen of death.
Crowdstrike's RCA found the outage boiled down to a failure to spot an input validation mismatch between a newly deployed threat detection configuration and its agent running in kernel mode that triggered an out-of-bounds read.
In a technical report, Microsoft’s David Weston, Vice President, Enterprise and OS Security, also blamed the outage on a read-out-of-bounds memory safety error in CrowdStrike’s CSagent.sys driver.
I don't do Windows but here are some (initial) details about why the CrowdStrike's CSAgent.sys crashed
— Patrick Wardle (@patrickwardle) July 19, 2024
Faulting inst: mov r9d, [r8]
R8: unmapped address
...taken from an array of pointers (held in RAX), index RDX (0x14 * 0x8) holds the invalid memory address@_JohnHammond pic.twitter.com/oqlAVwSlJj
Restricting kernel access enhances security by minimising the attack surface and reducing the blast radius of of vulnerabilities in user-mode applications. But it can also impede the performance and capabilities of legitimate security solutions requiring deep kernel interaction such as EDR (Endpoint Detection and Response) tools.
Microsoft itself told the Financial Times it was “considering several options to make its systems more stable and had not ruled out completely blocking access to the Windows kernel”. The newspaper also noted that “rivals” (such as, we argue, security vendors) could be put at a competitive “disadvantage” against Defender, Microsoft’s own security product.
READ MORE: CrowdStrike’s unholy cluster is terrible news for CISOs
Keith McCammon, Co-founder and Chief Security Officer at Red Canary, a provider of managed detection and response (MDR) and other security capabilities, told The Stack that Microsoft had three choices ahead of it.
“It can maintain the status quo, introduce or impose additional safeguards, or restrict access to the kernel entirely,” he said. “It’s highly unlikely that Microsoft would host this summit if their plan were to maintain the status quo, so we can assume that it's planning to announce a change.”
Any change to kernel interfaces or access will have downstream impacts on security product vendors, McCammon noted. Vendors, too, will have to change their working practices - particularly when trying to make their products stand out in the market.
“Today, endpoint security vendors are differentiated in part based on their instrumentation of the Windows platform, including their use of kernel drivers, for data access and threat response,” McCammon said. Depending on the path that Microsoft chooses, this type of differentiation may be a thing of the past.”
Adventures in a "virtual police state"
If it's not your job to venture deep into the kernel, then you might be glad to hear of any updates offering increased security, particularly in the wake of a widely publicised global outage.
Andrew Plato, CEO at IT strategist Zenaciti and founder of security firm Anitian, told us: “Ultimately this will be a net benefit to consumers. Kernel restrictions create a sort of 'virtual police state’ inside the core operating system.
“Nothing can run without explicit approval, in the form of a cryptographically signed certificate, from Microsoft. Apple has restricted kernel access on iOS and MacOS for years and it has made those products generally more secure.”
However, any attempt to lock vendors out of the kernel is likely to lead to massed wailing and gnashing of teeth, forcing software rewrites at best and playing havoc with long-established business models at worst.
Plato added: “Most antimalware products, such as CrowdStrike, Sentinel One, or McAfee require kernel access to perform security monitoring functions. This means those vendors will need to work with Microsoft to get access.
"Microsoft will likely follow Apple’s lead and implement a cryptographic signing system, where only approved drivers can access the kernel. Furthermore, Microsoft will likely need to implement ways for end users to disable this ability, much like Apple does as well.”
Morey Haber, Chief Security Advisor at BeyondTrust and author of a number of books on security, pointed out that a famous case in Europe will inevitably shape Microsoft’s decisions about closing down kernel access.
“In 2009, the EU ruled against Microsoft in an anti-competitive lawsuit,” Haber said. “All Microsoft Windows APIs, files, and developer kits are now equally available to competitors and developers as Microsoft uses internally.
"This anti-competitive ruling also governs kernel access and is why CrowdStrike and other vendors can succeed in developing security solutions as good, or better than Microsoft itself. If Microsoft does limit Kernel access, its must honour the guidelines of the EU ruling or be prepared to revisit the litigation.”
Microsoft itself reportedly told the Wall Street Journal that it “cannot legally wall off its operating system” like Apple due to the “understanding” with the EU that gives security software vendors the same level of access to Windows that Microsoft enjoys.
Sign up for The Stack
Interviews, Insight, Intelligence for Digital Leaders
No spam. Unsubscribe anytime.
What happens if Microsoft restricts or reduces kernel access?
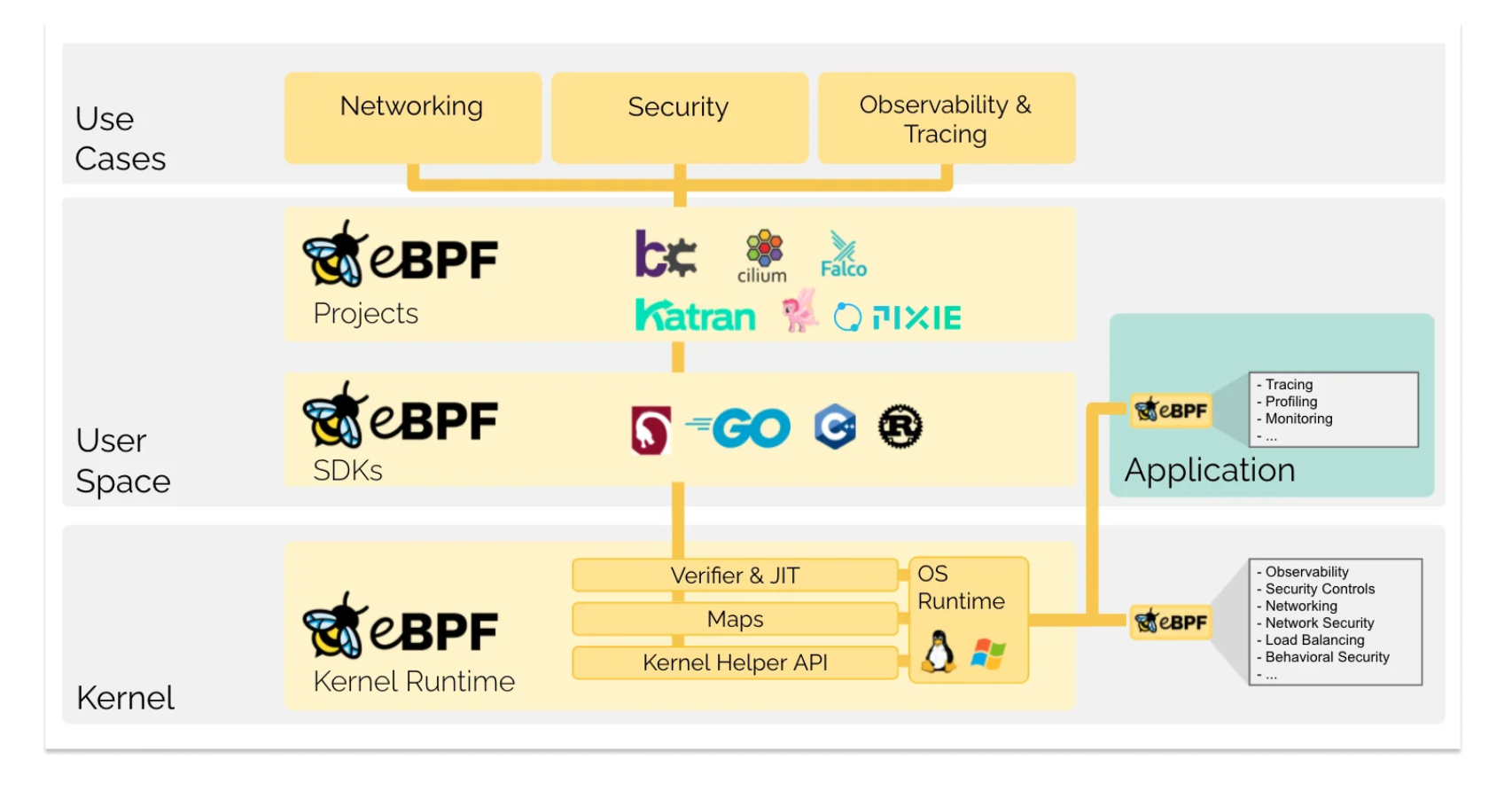
If it restricts access to the kernel, Redmond will need to develop new interfaces to facilitate security monitoring as well as low-level operating system functions for which drivers are currently required. Technologies such as eBPF (Extended Berkeley Packet Filter) let sandboxed programs run in privileged contexts, including the kernel. However, whilst eBPF is commonly used on Linux, it hasn't yet made the jump to Windows. Read more about eBPF here.
Ashley Manraj, CTO of Pvotal Technologies, predicted that Microsoft will not “merely seek input but actively guide the trajectory of eBPF for Windows”.
Manraj said: “Microsoft likely wants to propose an adoption plan subject to limited user input, revisiting a stance they've held for over a decade but weren't able to deploy after European regulators’ decision. It is likely to establish or even enforce specific development practices, testing protocols, and stringent security measures for eBPF programs.
“To streamline adherence to these standards, Microsoft may introduce new development tools, testing frameworks, or even specialised runtime environments tailored for eBPF security applications.”
Microsoft: Dictator or collaborator?
Eric O'Neill, Former FBI Counterterrorism and Counterintelligence operative, founder of security service provider Nexasure AI and global security speaker, suggested that Microsoft may “prioritise damage control over transparent collaboration.
“The closed-door nature of these meetings limits diverse perspectives from the broader security community,” he warned. “A more open and inclusive approach to addressing Windows security shortcomings might lead to more effective solutions. Microsoft owes their user base and the tech community at large far more transparency.
“Restricting access to the kernel is a good practice for operating system stability and security. However, security software requires full visibility into what OS and Applications are executing and the only way to do that in Microsoft’s current Windows environment is kernel access.
“There are ways for Microsoft to change this but I suspect its large market share, legacy systems, and concern over forcing the many applications that survive off of Windows like sucker fish on a whale to revise their code have prevented Microsoft from making the necessary changes.”
Stay tuned to The Stack for all the news from Windows Endpoint Security Ecosystem Summit - and please contact jasper@thestack.technology in confidence if you're able to tell us what went on behind closed doors.