
It’s been a long time coming, but Microsoft customers can now use a much wider range of multifactor authentication (MFA) providers with Entra ID (previously known as Azure Active Directory) – including offerings from Cisco Duo, Entrust, Ping Identity, Thales, and others.
In a move first teased four years ago, Redmond is also allowing “external authentication methods” by customers; i.e. “a standards-based open model where any authentication provider that wants to build an integration can do so” (using this integration documentation.)
This decision means customers can use a a range of third-party identity providers to plug in directly into Microsoft backbone identity systems.
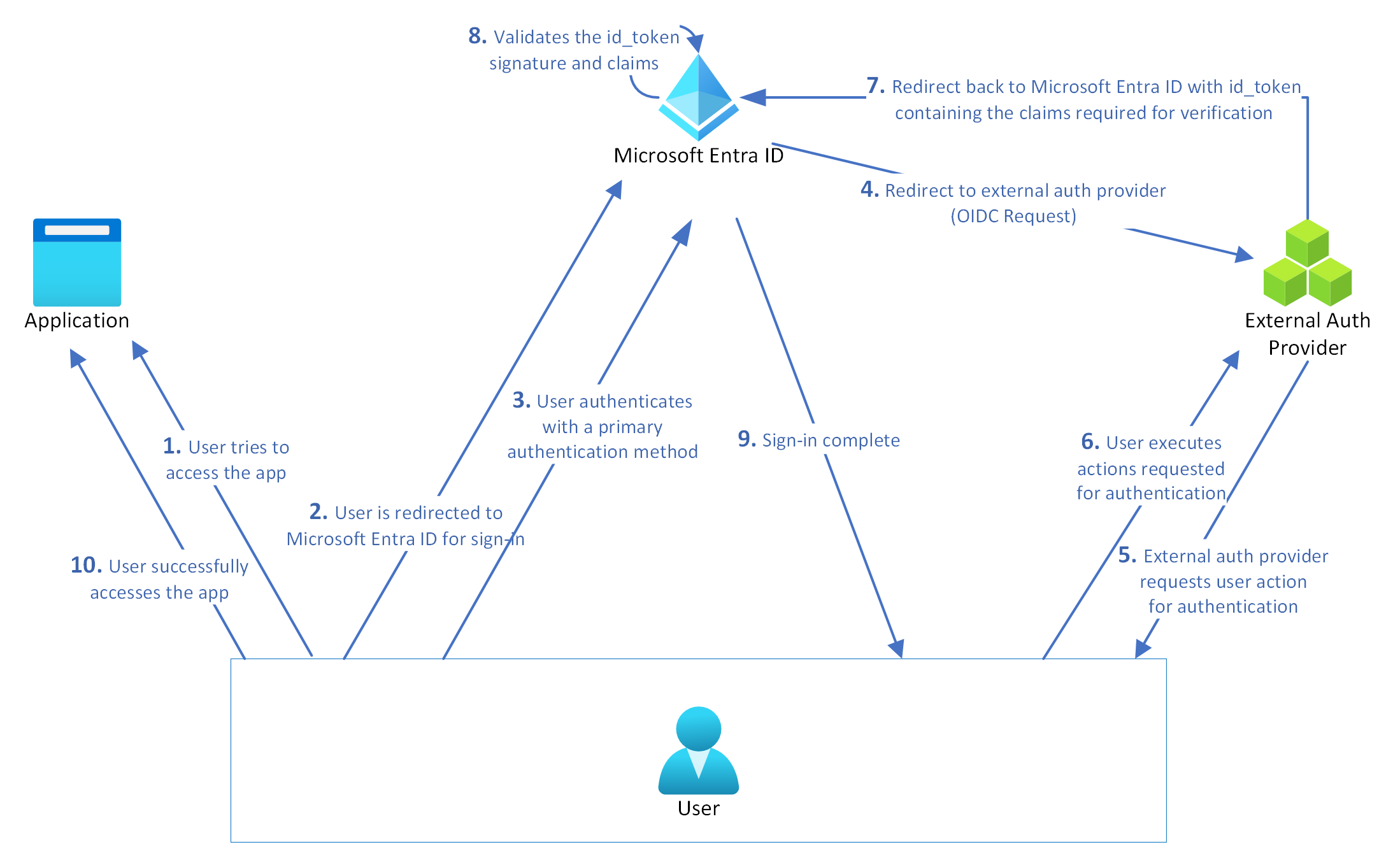
As Microsoft MVP Daniel Bradley, a technical architect with Six Degrees put it tidily: “Prior to external authentication methods, external authentication providers would have had to use the Custom Controls feature of Conditional Access. While this could be used to redirect a users sign-in to the external providers challenge page, it would not satisfy the MFA requirement in Microsoft Entra and hence the MFA grant control within Conditional Access could not be enabled. In this instance, not MFA claim would be issued in the access token and many security related functions in Conditional Access could not be utilised.
“EAMs differ from federation in that the user identity is originated and managed in Microsoft Entra ID. With federation, the identity is managed in the external identity provider. EAMs require at least a Microsoft Entra ID P1 license” a separate blog post from Microsoft on May 2 noted.
Bradley added: “A lot of MSPs utilise a third-party authentication providers (such as Cisco’s Duo) to supply a consistent MFA experience for their clients across systems such as workstations, servers, VPNs and Microsoft Entra. However, when this is deployed in the context of Microsoft Entra, while it might serve up some additional ‘perceived’ security, in a modern world, that is not completely the case.
"If we look at traditional attack tactics, such as credential phishing, an attacker may use compromised credentials to attempt to sign in to Microsoft Entra as that user. Conditional Access, whether requiring MFA or custom controls would prevent this successfully. However, attacker methodologies are rapidly evolving and no longer is it enough to just defend against traditional credential-based attacks. Adversary-in-the-middle (AitM) phishing attacks are seeing increased use in the wild, this is where attackers attempt to steal access tokens instead of passwords. In this scenario, custom controls do not suffice.
"This is where Conditional Access comes in, by ensuring external authentication methods can satisfy MFA requirements in Conditional Access, administrators can enforce stronger controls such as sign-in frequency and other token protection mechanisms. These MFA claims, delivered through external providers could also be used to satisfy PIM role activation, risk-based policies and Intune device registration..."
This is available in public preview later in May with Microsoft running a May 15 webinar in which it will share more details, Redmond said.
See also: Microsoft unleashes new Deputy CISOs, will tie leadership compensation to security
