Updated January 25, 2023, 09:47am BST as Microsoft blames a WAN update.
A global Microsoft networking issue is impacting "multiple Microsoft 365 services" it confirmed this morning as users said everything from VPNs, SQL, web applications and more had failed.
The massive Microsoft outage was reflected the Azure status page which was a sea of red warning codes for "network infrastructure" across Americas, Europe, APAC and Middle East and Africa.
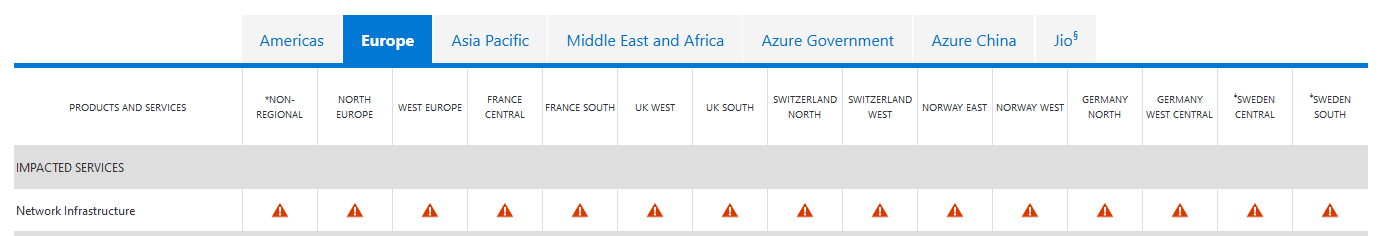
The Azure stagus page said: "Starting at 07:05 UTC on 25 January 2023, customers may experience issues with networking connectivity, manifesting as network latency and/or timeouts when attempting to connect to Azure resources in multiple regions, as well as other Microsoft services."
"We’ve isolated the problem to networking configuration issues, and we're analyzing the best mitigation strategy to address these without causing additional impact" Microsoft Tweeted.
The company later added: "We've determined the network connectivity issue is occurring with devices across the Microsoft Wide Area Network (WAN). This impacts connectivity between clients on the internet to Azure, as well as connectivity between services in datacenters, as well as ExpressRoute connections.
"The issue is causing impact in waves, peaking approximately every 30 minutes.
https://twitter.com/thousandeyes/status/1618254883173576705
"We have identified a recent WAN update as the likely underlying cause, and have taken steps to roll back this update. Our latest telemetry shows signs of recovery across multiple regions and services, and we are continuing to actively monitor the situation" Microsoft added.
The incident comes less than two weeks after a botched code deployment to Windows Defender saw the cybersecurity platform delete Microsoft's own applications from desktops globally.
"On January 13th, Windows Security and Microsoft Defender for Endpoint customers may have experienced a series of false positive detections for the Attack Surface Reduction (ASR) rule "Block Win32 API calls from Office macro" after updating to security intelligence builds between 1.381.2134.0 and 1.381.2163.0."
"These detections resulted in the deletion of files that matched the incorrect detection logic primarily impacting Windows shortcut (.lnk) files" Microsoft admitted at the time.