“You don’t rise to the occasion in incident response; you fall to the level of your preparation” said Bill Siegel, speaking from the experience of supporting one too many ransomware response engagements.
The CEO and co-founder of Coveware, an IR specialist sold to Veeam in April 2023, was speaking on stage at the latter’s annual conference, as Veeam published its 2024 Ransomware Trends report – born out of the analysis of 1,200 ransomware victims’ experiences and 3,600 attacks.
As well as the need to regularly rehearse disaster recovery scenarios, organisations need to be aware of the need to operate cautiously in IR, Siegel added, saying: “We’re often trying to slow companies down…”
That might sound counter-intuitive: For most ransomware victims, every minute down costs lost revenues and drives up reputational damage.
But restoring from backups in a panicked manner can do the obvious damage of putting data/applications back onto unsafe systems.
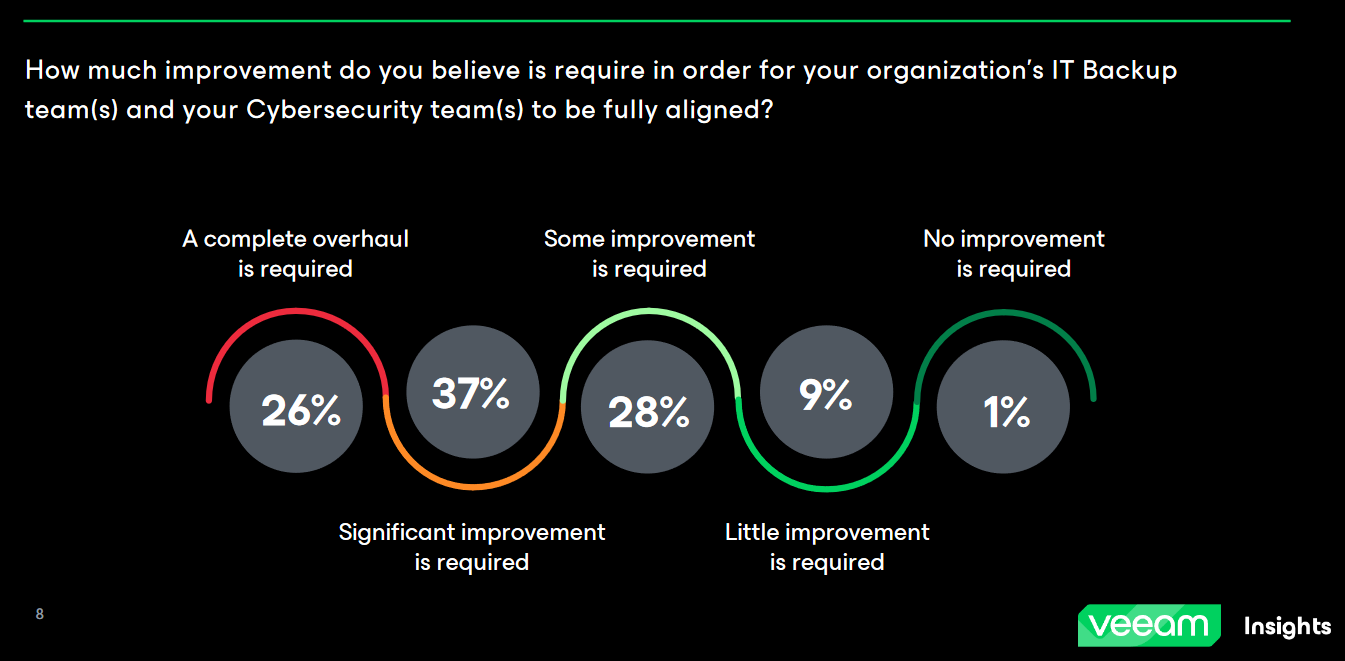
It can also expose those backups to attackers squatting compromised infrastructure: “You have to get contained or they’ll discover and wipe your backups” as Siegel put it; with Veeam’s ransomware report showing that backup repositories “are targeted in 96% of attacks, with bad actors successfully affecting the backup repositories in 76% of cases…”
That’s a somewhat unusual statistic for a backup specialist to be touting. Veeam backups are often explicitly targeted in ransomware attacks (risk is often heightened by poor customer implementations) and Gartner warned in its last Magic Quadrant that “implementing a secure Veeam Data Platform requires clients to thoughtfully design, configure and manage the deployment to mitigate cyberthreats” – but the data point serves to accentuate another notable takeaway from the report.
Chiefly that is that for the third year in a row, more than half of organisations (63%) believe that there is either a “significant improvement” or “complete overhaul” needed for their organizations to be aligned between their backup and cybersecurity teams.
As the report, published on June 4, noted: “Of the three roles surveyed backup administrators were the least satisfied with the alignment of these teams. This suggests that backup, while important, may not be as involved in the preparedness strategy as organizations ought to consider.”
Why aren’t they?
Siegel, collared briefly by The Stack at a media briefing, suggests that organisational structures in which backups were traditionally thought of just as a disaster recovery (think floods, fire) insurance rather than being inherently part of a cybersecurity strategy is part of that answer.
Turning that institutional ship can take a long time.
Often, he said, the first encounter backup managers might have with infosec teams is still when the latter comes asking for restoration.
Bringing backup managers in early into tabletop exercises and more regular engagements with cybersecurity leaders clearly seems judicious.
Not least since other IR expects regularly bewail that too often poorly coordinated crisis planning means that when ransomware does strike, major challenges have been overlooked; e.g. do you know how to restore when you’ve lost access to Active Directory? (Numerous victims over the years have faced a situation in which their backup solution required AD to log in, but they’d lost access, couldn’t authenticate, and nothing worked.)
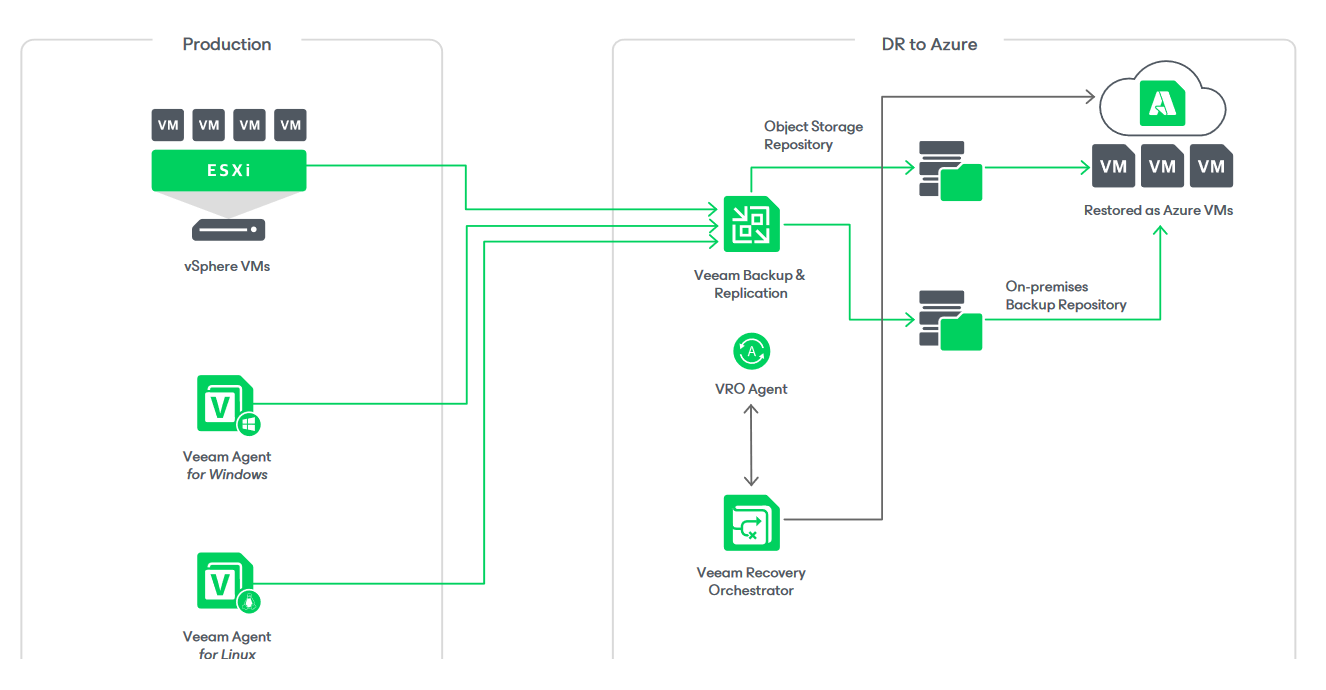
Veeam, of course, boasts a suite of offerings intended to help here, including just by way of one example, its Veeam Recovery Orchestrator which gives users the ability to restore VMware and other workloads and Veeam Agent backups directly to Microsoft Azure in addition to VMware environments. As a recent Veeam whitepaper has it: “Enterprises can plan for recoverability by creating orchestration plans to combat downtime, whether that’s due to ransomware or aftereffects like restrictions imposed by law enforcement. Once plans are built out, they can be tested in a sandboxed environment. This not only ensures that everything will work as expected, but it will also provide proven RPOs and RTOs, giving you the confidence that you need to recover from an incident."







