UPDATED May 13 with reported ransom payment.
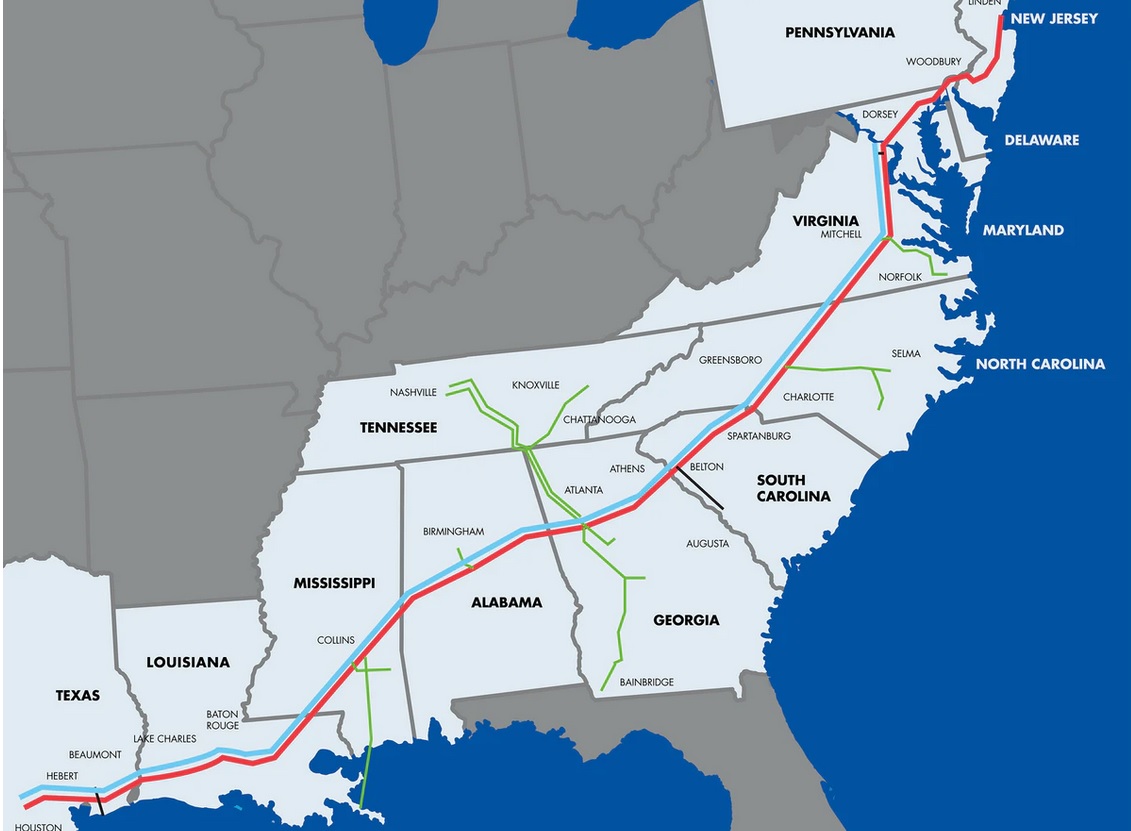
A ransomware attack on the US's Colonial Pipeline took the major East Coast energy artery completely offline Friday, May 7, threatening to send US gasoline prices to their highest levels in seven years. The pipeline carries some 45% of the East Coast's supply of diesel, gasoline and jet fuel, as well as fuel for the US Military through its 5,500 mile pipeline network.
Some 10% of petrol stations in Virginia were reported empty by Wednesday, although fuel is now being moved by road. The FBI confirmed Monday "that the Darkside ransomware is responsible for the compromise of the Colonial Pipeline networks. We continue to work with the company and our government partners on the investigation."
Bloomberg reported Thursday May 13 that the company had paid a $5 million ransom within hours of the attack: "Once they received the payment, the hackers provided the operator with a decrypting tool to restore its disabled computer network. The tool was so slow that the company continued using its own backups to help restore the system, one of the people familiar with the company’s efforts said", Bloomberg claimed.
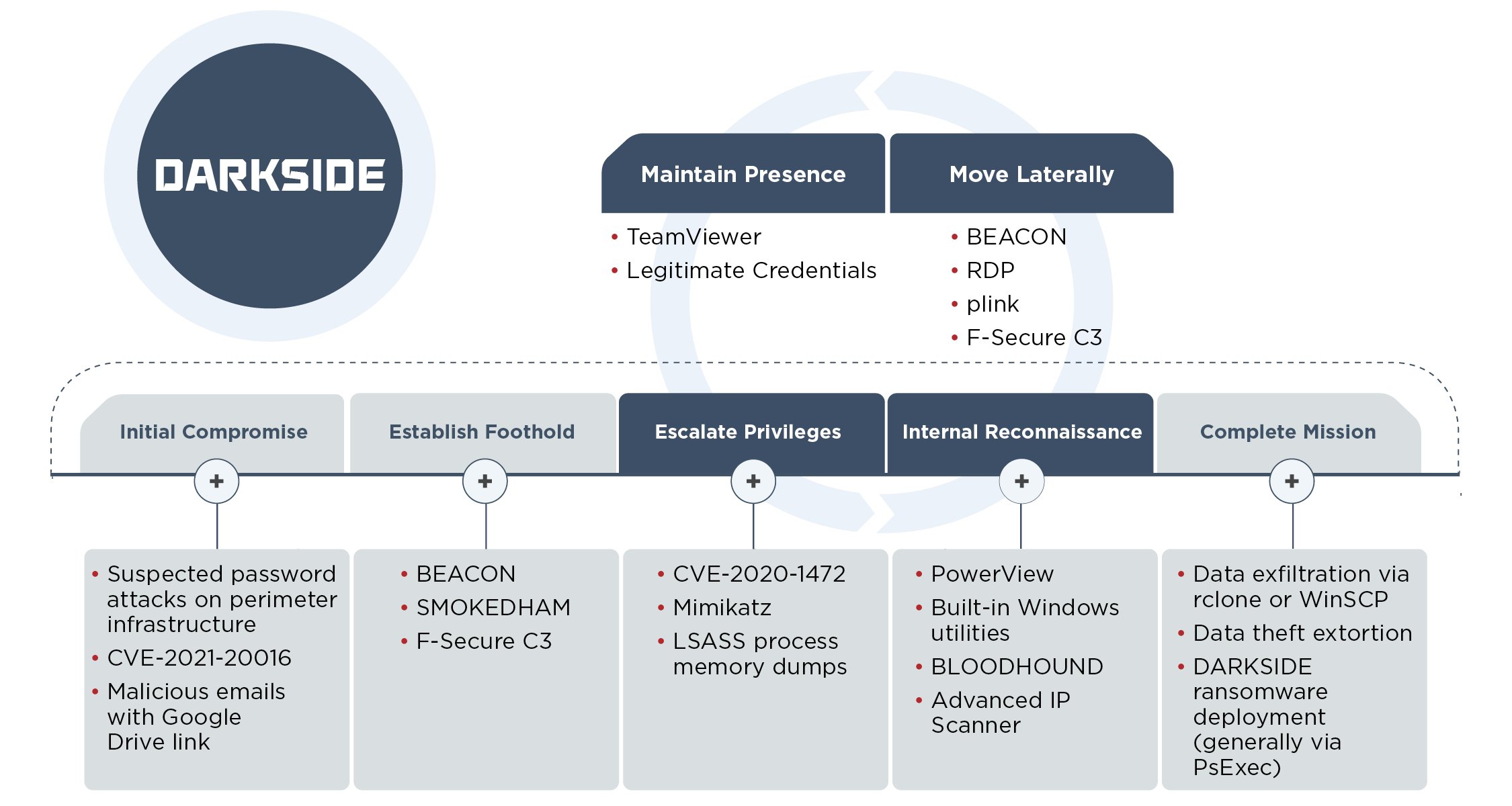
The cybercrime syndicate is reported to be based in Russia or Eastern Europe and follows a Ransomware-as-a-Service (RaaS) model. It is not a discrete entity, as FireEye notes in a detailed blog that highlights "five clusters of threat activity" ultimately involving the ransomware payload and a range of techniques deployed by users of its ransomware.
In a statement last updated late Monday, the pipeline operator said: "The Colonial operations team is executing a plan that involves an incremental process that will facilitate a return to service in a phased approach.
"This plan is based on a number of factors with safety and compliance driving our operational decisions, and the goal of substantially restoring operational service by the end of the week. We continue to evaluate product inventory in storage tanks at our facilities and others along our system and are working with our shippers to move this product to terminals for local delivery. Actions taken by the Federal Government to issue a temporary hours of service exemption for motor carriers and drivers transporting refined products across Colonial’s footprint should help alleviate local supply disruptions and we thank our government partners..."
The Federal Motor Carrier Safety Administration has issued a regional emergency declaration permitting the transport of fuel by road. Hackers stole almost 100GB of data from Colonial Pipeline's networks, before locking its computers with ransomware and demanding payment, according to multiple reports. The White House has formed a task force to probe the pipeline breach. CISA is also coordinating with Colonial Pipeline.
It was not clear Monday if -- or the extent to which -- the attackers had pivoted from the IT infrastructure to the OT infrastructure behind the physical operations. Sources told security reporter Kim Zetter that the ransoming of IT systems like the automated ticketing system for billing customers on the corporate IT network could delay the pipeline restart -- if crippled, Colonial can’t invoice customers automatically, they said.
Security and incident response experts meanwhile emphasised that time and again ransomware crews are succeeding based on the simplest of attacks; utilising unpatched critical vulnerabilities in software, lack of network segmentation and no multi-factor authentication to gain and sustain access in organisations.
The company reports extensive recent "digital transformation" on its site, however, saying it is "evolving from a mechanical environment into the digital world... our operators have the latest technology at their fingertips to monitor, control, and adjust product flows for safety and efficiency.
"Colonial operators are also leveraging computerized technology to monitor pressures, pump operating status, and valve positions -- 24/7, 365 days a year. These modernizations enable operators to make better and more knowledgeable decisions to optimize our pipeline."
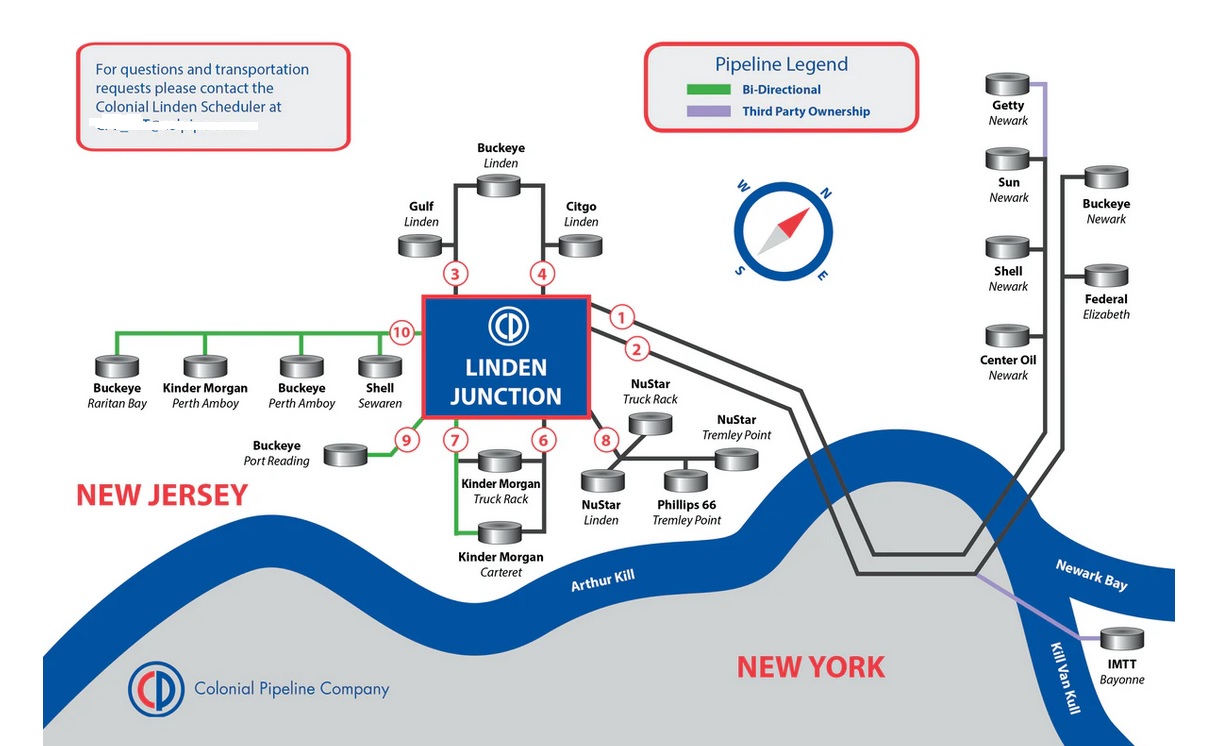
Along with transmission, Colonial offers partners both short term and long term storage based on available tank space along the Colonial system, as well as products transfer at a complex hub new New York. The US's CISA said it is "monitoring the ransomware incident affecting Colonial Pipeline. Every organization must be vigilant and strengthen its cybersecurity posture against ransomware and other types of cyber-attacks."
Gasoline futures climbed by over 4.2% in Asian trading on Monday.
Lesley Carhart, Principal Industrial Incident Responder at the industrial cybersecurity firm Dragos. noted: "A lot of firms are going to be out there shilling magic boxes to fix “everything” in the coming weeks, but while the malware and anti-forensics in these cases are often quite sophisticated, we see the same lack of security hygiene and basic defense in depth exploited repeatedly. Like, lack of basic monitoring or logging capability. No MFA where it counts. Forgetting to check system exposure with assessments or at least Shodan. No IR plan or retainer."
In a statement posted on their onion site on Monday, DarkSide tried to pin the blame on a RaaS customer, saying: "We are apolitical. We do not participate in geopolitics. Our goal is to make money and not creating problems for society. From today, we introduce moderation and check each company that our partners want to encrypt to avoid social consequences in the future.”
Cyberreason was among the early vendors to track DarkSide activity and TTPs, saying in April the crew "is observed being used against targets in English-speaking countries, and appears to avoid targets in countries associated with former Soviet Bloc nations. The ransom demand ranges between US$200,000 to $2,000,000, and according to their website, the group has published stolen data from more than 40 victims, which is estimated to be just a fraction of the overall number of victims."








