Kroll, a risk advisory heavyweight based in New York that serves more than half of the S&P 500, has laid the blame squarely at T-Mobile’s door after a social engineering attack that resulted in a data breach.
In an unusually direct apportioning of blame on Friday after the security incident, which Kroll said was limited to just three accounts in the digital assets segment (BlockFi, FTX, and Genesis) the company revealed that one of its employees had fallen victim to a “SIM swapping” attack on August 19.
The company said on August 25: “T-Mobile, without any authority from or contact with Kroll or its employee, transferred that employee’s phone number to the threat actor's phone at their request… We are cooperating with the FBI and a full investigation is underway. We have no evidence to suggest other Kroll systems or accounts were impacted,” it added.
(Kroll is handling bankruptcy restructuring for the three and has issued an FAQ for FTX account holders that reveals that the attacker "accessed files in Kroll’s cloud-based systems that... contained your name, address, email address, and the balance in your FTX account" but did not access any digital assets. The information could be used in further phishing attacks.)
As Shaun Nichols noted of the breach for The Stack: “While Kroll described the attack as ‘highly sophisticated’ SIM-swapping is a relatively straight-forward technique that relies far more on social engineering than any technical prowess. In a SIM-swapping attack the criminal convinces the target's mobile carrier that the target's phone was lost or stolen and asks that their SIM card status (including their mobile phone number) be transferred to a new device controlled by the attacker. From there, the attacker can reset passwords or get token access to other accounts.”
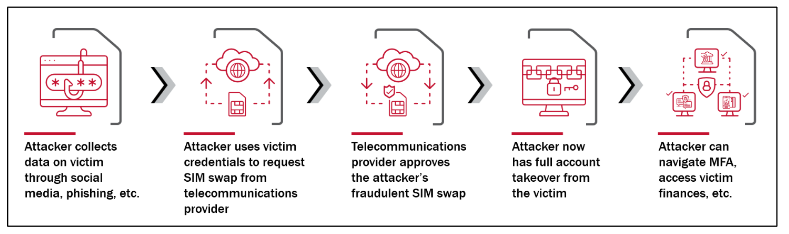
The SIM swapping attack on Kroll comes just weeks after CISA warned that organisations – including telcos like T-Mobile – are not doing enough to protect themselves and customers against the risk of SIM swapping








